Learn about the key benefits arising from recoding version 10.0 of SAP BusinessObjects Access Control on the ABAP platform and its harmonization with other SAP BusinessObjects GRC solutions such as version 10.0 of SAP BusinessObjects Process Control and version 10.0 of SAP BusinessObjects Risk Management. Walk through the key improvements in the areas of access risk analysis, user access management, business role governance, centralized emergency access, and improved identity management integration.
Key Concept
SAP has recoded version 10.0 of SAP BusinessObjects Access Control on the ABAP stack, and the release cycles of all SAP BusinessObjects GRC solutions have been synchronized for the first time, resulting in a more simplified system component architecture.
Thanks to the synchronization of the release cycles in version 10.0 of SAP BusinessObjects GRC solutions, version 10.0 of SAP BusinessObjects Access Control, version 10.0 of SAP BusinessObjects Process Control, and version 10.0 of SAP BusinessObjects Risk Management have been harmonized to a unified compliance platform running on SAP NetWeaver Application Server ABAP 7.0 enhancement package 2 (aka 7.02). Consequently, all SAP BusinessObjects GRC solutions, including version 10.0 of SAP BusinessObjects Access Control, leverage ABAP application server features such as enterprise supportability, granular security, transport management system, robust scheduling, and archiving.
This harmonization effort may help lower total cost of ownership (TCO) by eliminating redundancy in administration, configuration, setup, and end-user training. ABAP-coded applications come with user exits that allow for customer enhancements and simplified maintenance with standard SAP notes and support packages. In addition, users can apply to SAP BusinessObjects Access Control 10.0 their existing knowledge and system maintenance procedures to operate ABAP stack applications. This article examines features and benefits of the unified compliance platform and discusses the key improvements added to the application.
Note
Whereas the previous release, SAP BusinessObjects Access Control 5.3, was a Java application running on SAP NetWeaver Application Server Java 7.0, the new release has been completely recoded to run as an ABAP application on SAP NetWeaver Application Server ABAP 7.02. In addition, the four main capabilities of the 5.3 release — risk analysis and remediation (RAR), compliant user provisioning (CUP), enterprise role management (ERM), and superuser privilege management (SPM) — that ran very much in silos with little integration have now been harmonized, and data redundancies have been removed. As a result of this enhancement, the naming of these capabilities has been dropped, and the terms access risk management, user access management, business role governance, and centralized emergency access are used instead. For a functional overview and an explanation of the main concepts of the previous release, SAP BusinessObjects Access Control 5.3, refer to my earlier articles posted in 2009.
Unified Compliance Platform
Suite 10.0 of SAP BusinessObjects GRC solutions comes as an enterprise GRC platform built to manage all risks and controls from a single environment. For this purpose SAP BusinessObjects Access Control, SAP BusinessObjects Process Control, and SAP BusinessObjects Risk Management have been harmonized across all levels from the user interface and information architecture to the data model, allowing for even tighter integration between the three applications. The information architecture defines much of the initial user experience and determines the presentation of user interface elements such as menu structure, tabs, and navigation alternatives. The goal is to provide a consistent and optimized user experience across the three SAP BusinessObjects GRC solutions and minimize redundancies for users of multiple SAP BusinessObjects GRC solutions.
At the top of the user interface are tabs, called work centers, that logically group the functionality of SAP BusinessObjects Access Control, SAP BusinessObjects Process Control, and SAP BusinessObjects Risk Management (Figure 1). The work centers include My Home, Master Data, Rule Setup, Assessments, Access Management, and Reports and Analytics. Users have access to areas of the solution based on their licensing and object level security, so users only see capabilities and data appropriate for their jobs. In addition, the user can customize the appearance and naming of the application folders and links in Figure 1.
Version 10.0 of SAP BusinessObjects Access Control can share organizations and controls with SAP BusinessObjects Process Control and SAP BusinessObjects Risk Management. The object business unit in SAP BusinessObjects Access Control 5.3 has been replaced by the object organization, to which mitigation controls are now associated. However, it is still possible to keep the master data in each application separate. Version 10.0 of SAP BusinessObjects Access Control uses two different object types of controls to mitigate access risks:
- Controls created in version 10.0 of SAP BusinessObjects Process Control
- Mitigation controls maintained locally in SAP BusinessObjects Access Control
The first option requires a license for SAP BusinessObjects Process Control as well and allows for a closed-loop mitigation of access risks because the controls used for access risk mitigation in SAP BusinessObjects Access Control are documented, assessed, monitored, tested, remediated, and signed off within the separately licensed SAP BusinessObjects Process Control application. The SAP BusinessObjects Access Control application provides a simplified and customizable view on the controls pulled in from SAP BusinessObjects Process Control for access risk mitigation (Figures 2 and 3). The second integration scenario between SAP BusinessObjects Access Control and SAP BusinessObjects Process Control is the ability to schedule segregation of duties (SoD) risk analysis that is executed in SAP BusinessObjects Access Control for continuous monitoring from the automated rules framework in SAP BusinessObjects Process Control, already available in the previous release.
Note
An SoD risk refers to access privileges to two different business functions in one or multiple ERP systems, which in combination could lead to fraud. SoD risks are distinguished from a critical action or permission risk where a single transaction can already lead to fraud (example: user admin).

Figure 1
An SAP NetWeaver Business Client (NWBC)-based user interface with harmonized information architecture structured in work centers, application folders, and application links
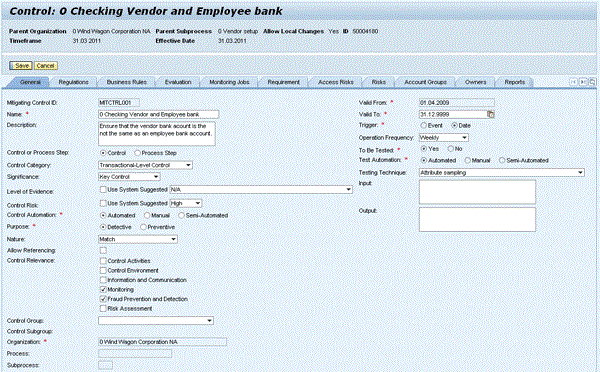
Figure 2
SAP BusinessObjects Process Control view of a control used in SAP BusinessObjects Access Control for access risk mitigation
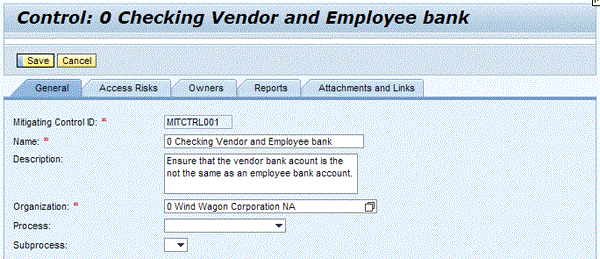
Figure 3
A simplified SAP BusinessObjects Access Control view of the control shown in Figure 2
Enhanced Access Risk Analysis
The enhancements of the access risk analysis capability can be grouped into the following areas:
- An intuitive user interface supporting end-user customization and personalization
- A new risk analysis framework
- New ability for system- and rule-specific mitigation
- New ability for mass mitigation
- A workflow-driven approval process for function maintenance
- Additional audit-trail tracking with configuration options and easy to access change history
The user interface comes with usability features that considerably improve the overall user experience compared with the previous release. All result lists now consistently contain easy-to-use abilities for filtering, sorting, arranging, and hiding columns (Figure 4). A number of settings for column selection, sorting, calculations, filters, display, and printing are available to end users and can be saved as user-specific views (Figure 5). In addition, a guided procedure helps end users create on-the-fly queries (Figure 6), and personalization settings define the default view.

Figure 4
New user interface features improve usability and include filtering, sorting, hiding, and changing the sequence of columns
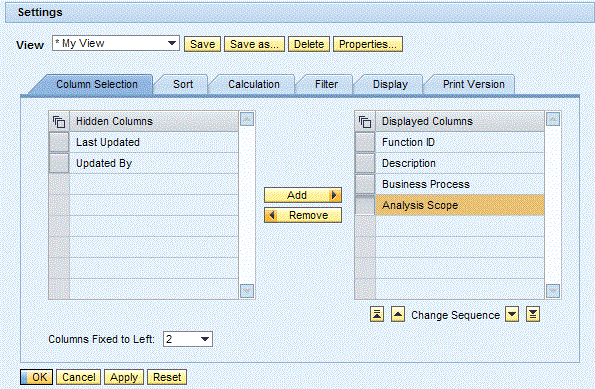
Figure 5
Settings for selecting columns, sorting, calculating, filtering, displaying, and printing can be saved as user-specific views

Figure 6
A guided procedure helps end users create queries
The enhanced risk analysis framework allows for a far more flexible selection of analysis criteria than in previous versions. The upper part of the screen shown in Figure 7 shows the Analysis Criteria. Rows for analysis criteria can be added or removed by the plus (+) and minus (-) buttons on the right. Users can add analysis criteria based on System, User, User Group, Custom Group, Risk Level, Rule Set, user lock and validity status, role assignment validity status, org level, org rule, org value, org unit, risk by process, access risk ID, and user type.
The users have the option to choose among the following criteria to support their selection: is, is not, starts with, contains, is between, and Multiple Selections. When the Multiple Selections option is chosen, the button Add Selections appears. Clicking it brings up the Multiple Selection screen (Figure 8). This screen allows you to select objects by inclusion and exclusion of lists and ranges. Particularly interesting is the ability to upload object lists; for example, a list of users on which to run an access risk analysis. With these options you can generate much more selective reports, thus saving time for report processing and presenting only information that is relevant to the end user.
The lower part of the screen in Figure 7 contains the Report Options. With the new framework you can perform multiple risk analysis types at the same time. You can save all selections in variants and execute the risk analysis in foreground or background mode.
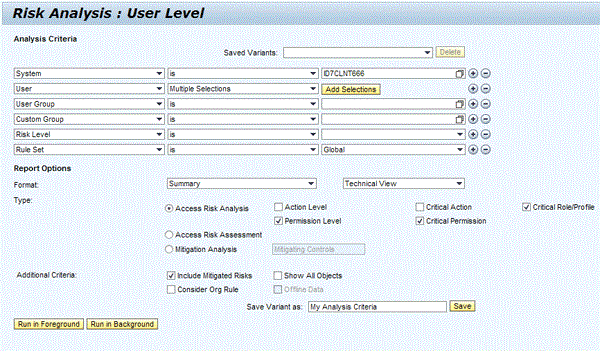
Figure 7
The new risk analysis framework allows for very flexible selection of analysis criteria and report options
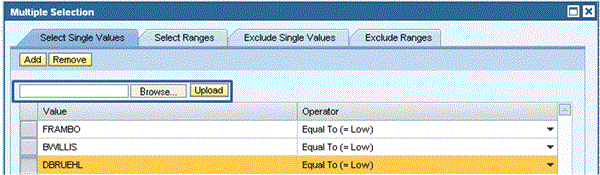
Figure 8
The Multiple Selections option in Figure 7 allows you to select or exclude object ranges and upload object lists from a flat file
The analysis results screen is shown in Figure 9. The top part of the screen repeats the analysis criteria for which the report was generated. In the upper part of the Analysis Results area, select which Result Set you would like to display. When the reports are too large they are split into different Result Sets, allowing you to export them in multiple files and thus prevent file size restrictions and provide better memory management. The report provides the usability features for end-user customization and personalization.

Figure 9
The Analysis Results screen includes information on execution of transactions by the reported users
With the new release the report displays how many times, and when, a transaction was last executed that caused an access risk violation. This new report format facilitates remediation activities because you can now drill down on user IDs and Access Risk IDs and display more detail. With the Display As drop-down menu, you can switch from the tabular Advanced List Viewer (ALV) to Crystal Reports (Figure 10). However, this feature requires the installation of the client software component SAP Crystal Reports Adapter on the desktop of your business users. The Print Version button generates a PDF version of the report. This feature requires an SAP NetWeaver Application Server Java 7.02 with Adobe Document Services instances on it in your system landscape.
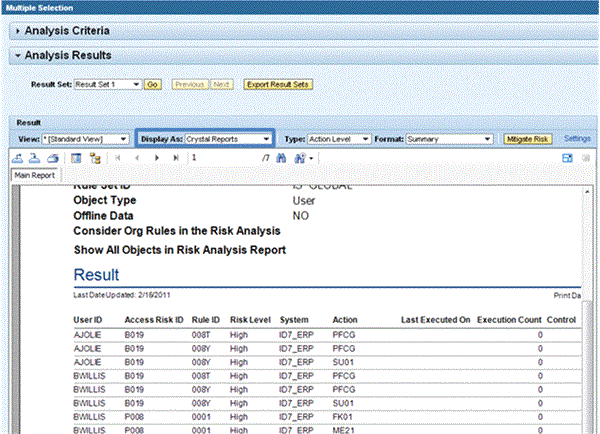
Figure 10
Risk analysis reports displayed as Crystal Reports
Access risk mitigation allows for assigning mitigation control for a given access risk by system or by rule. Mass mitigation has also become available, accelerating the process considerably and helping you avoid errors. Simply select multiple risk violations and assign new or update existing mitigation controls (Figure 11).

Figure 11
Enhanced access risk mitigation allows for system- and rule-specific controls, as well as mass mitigation
SAP BusinessObjects Access Control 5.3 already provided approval workflows for mitigation control maintenance, mitigation assignment, and risk maintenance. The new release completes this list with an approval workflow for function maintenance. You can activate all four approval workflows individually in IMG customizing. All work items are sent to the unified in-box of the approvers and are accessible in the My Home work center. Optionally, an email notification can be sent out as well.
You can track all changes to access rules by activating the audit trail in the IMG individually for the following objects:
- Function (Figure 12)
- Risk
- Org Rule
- Supplementary Rule
- Critical Role
- Critical Profile
- Rule set
You can easily access, export, or print the change history through the Change History tab of the respective access rule component (Figure 12) or via the Change Log report available in the Reports & Analytics work center.
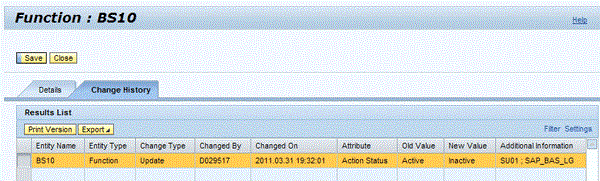
Figure 12
Change History tab of an example function
Streamlined User Access Management
With the move to the ABAP platform the standard SAP Business Workflow technology is now used for all types of approval workflows in SAP BusinessObjects Access Control, including access requests. This enhancement reduces manual tasks and streamlines access request processing for simple to highly complex organizations. Customers can leverage existing resources for workflow administration and configuration. A number of new features make it easier and faster for users to request the access they need:
- New customizable access request forms (Figure 13)
- New template-based access requests that are prefilled and personalized for users working in specific locations, departments, or jobs. Requesters just pick a suitable template and submit a prefilled request, leaving little opportunity for errors.
- New model user-based access requests permit you to refer to existing users for role selection
- New organizational assignment requests can be used to create access requests for positions, jobs, and org units in your SAP ERP Human Capital Management (SAP ERP HCM) system (Figure 14)
- New end-user display of access assignments and request history
- Enhanced search for roles, groups, and systems based on authorizations granted to the requester
- Options for group owners and controllers and improved provisioning of emergency access
You can now customize approver screens for each individual workflow stage, and risk analysis for approvers has become much more flexible, allowing for multiple rule sets (Figure 15).

Figure 13
Access Request in version 10.0 of SAP BusinessObjects Access Control
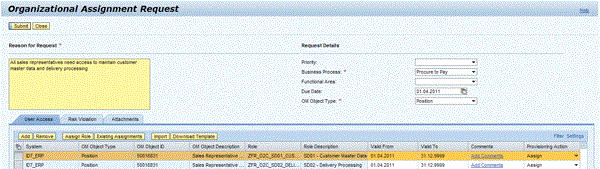
Figure 14
The new workflow process to request access for positions, jobs, and org units in your SAP ERP HCM system

Figure 15
Access request approval in version 10.0 of SAP BusinessObjects Access Control
Because of the shift to SAP Business Workflow, the configuration of the multistage-multipath (MSMP) workflow used in SAP BusinessObjects Access Control is considerably different compared with the old Java workflow. This configuration represents an area that requires some delta training even for experienced SAP BusinessObjects Access Control 5.3 administrators. The good news, however, is that an MSMP workflow configuration Web interface (Figure 16) has been added to the IMG, providing a guided procedure tailored to SAP BusinessObjects Access Control. MSMP workflows leverage the Business Rule Framework Plus (BRF+) that is part of SAP NetWeaver.
On a high level BRF+ is used to evaluate result values from a given business context. In MSMP, workflow BRF+ is used to build rules that evaluate attributes from a given request to determine the correct routing and approvers. In the terminology of SAP BusinessObjects Access Control 5.3 one could say that BRF+ rules replace workflow initiators, custom approver determinators (CADS), and detour conditions in cases where the predelivered options don’t meet the requirements. However, the MSMP workflow provides the additional option to implement initiator rules, approver agents, and routing rules by function modules or ABAP classes. The latter option, however, obviously requires development skills, whereas the creation of BRF+ rules is a configuration task for which users can be trained in one or two days. In a nutshell it is fair to say that the move to standard SAP Business Workflow comes with a certain level of change, but its rewards are robustness and flexibility for customer enhancements.
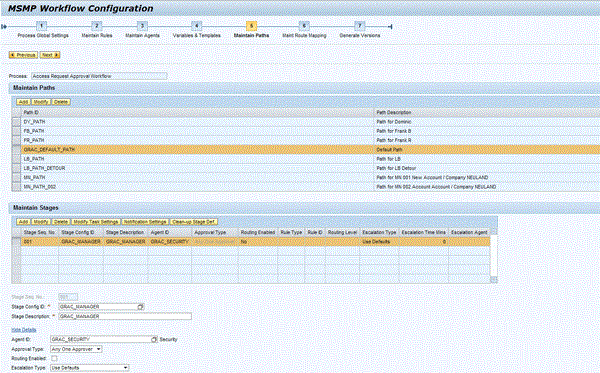
Figure 16
The Workflow Configuration user interface in version 10.0 of SAP BusinessObjects Access Control
Centralized Emergency Access
Emergency access management, known in previous releases of SAP BusinessObjects Access Control as firefighter or superuser privilege management (SPM), has undergone a significant architectural change and now provides centralized access for both administrators and business users acting as firefighters. Consequently, users now access the firefighter tables centrally in the SAP BusinessObjects Access Control system. Users with the required authorizations can manage assignments of firefighter IDs to owners, controllers, firefighters, and the reason code table. Authorized users also can access all related reports. These tables contain an additional column to indicate the back-end system (Figure 17). Likewise, firefighters log on with the SAP GUI to the SAP BusinessObjects Access Control system to start a firefighter session in one of the connected back-end SAP systems (Figure 18). In addition a number of powerful new enhancements have been added to the application:
- Options for group owners and controllers and improved provisioning of emergency access
- The ability for firefighters to update the activity log with unplanned firefighting tasks
- Access to specific log reports from a transaction report. Additional logs from the application server such as the system log (SM21), OS command log (SM49), and Security Audit Log (SM20) are now pulled in to the log report and provide information on critical activities, such as changes of variable values in debug mode, changes to external commands, and security relevant events (Figure 19).
- A workflow-driven log report to enforce and trace the approval process
- Enhanced categorization of firefighter access signifies criticality and drives workflow logic

Figure 17
A centrally managed firefighter table to assign firefighter IDs to business users (firefighters)
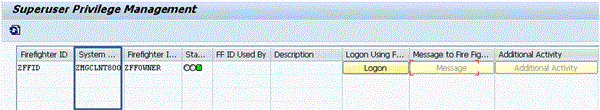
Figure 18
Firefighters log on to the SAP BusinessObjects Access Control system and select the system to start a firefighter session
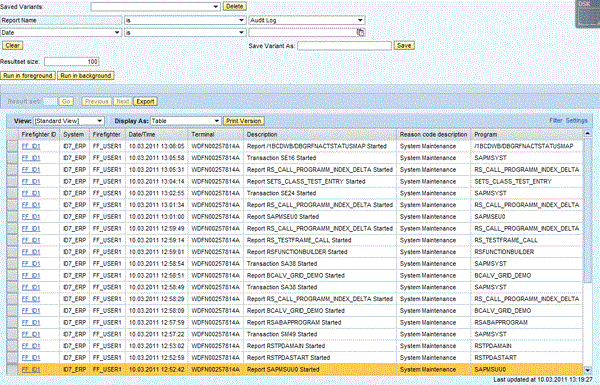
Figure 19
Information from the Security Audit Log configured in the SAP back-end system is pulled in to the log report documenting a firefighter session with firefighter ID FF_ID1
Business Role Governance
Version 10.0 of SAP BusinessObjects Access Control includes a powerful capability for scalable and collaborative business role modeling, supporting both technical and business users. It supports the design of compliant roles through a robust role governance process leveraging a central repository for role information and optimized integration for SAP systems through the profile generator. The following summarizes the key enhancements with respect to the previous release:
- New concept of business roles reflecting the jobs of your end users and reducing the complexity of your role concept. Business roles contain technical roles and can also contain other business roles.
- New role design and flexible role-building workflows, including access risk analysis and preventive simulations (Figure 20)
- New ability to analyze role usage of your business users for optimal assignment and to keep role definitions up-to-date (Figure 21)
- Improved role comparison to detect back-end changes provides role consistency, synchronization, and compliance (Figure 20)
- New process for periodic role certification
- Improved role mass maintenance (Figure 21)
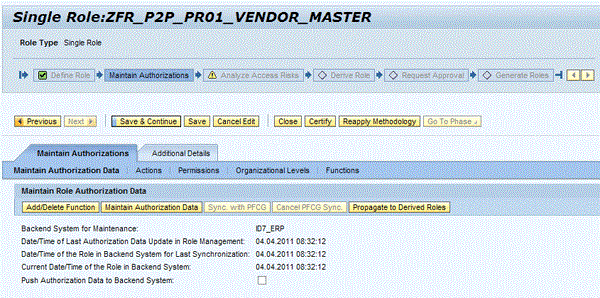
Figure 20
Role maintenance governed by a collaborative methodology process, including an access risk analysis
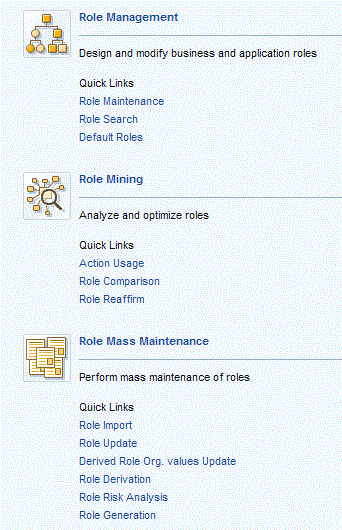
Figure 21
Enhanced capabilities for business role management, role mining, and mass maintenance streamlines management of technical roles and eases identification and selection of appropriate roles for users, positions, and jobs
Improved Identity Management Integration
The integration capabilities of SAP BusinessObjects Access Control with SAP or non-IdM solutions have been improved for provisioning and role management and provide increased flexibility to support enterprisewide compliant identity management. Users can better leverage existing investments in identity management solutions and SAP BusinessObjects Access Control and use both in combinations to unify compliant provisioning and ensure compliance through the role life cycle. A number of new integration scenarios are supported:
- The IdM solution can send a Web service request for risk analysis to SAP BusinessObjects Access Control and create a remediation request in SAP BusinessObjects Access Control, only if access risks are found. Once the remediation request has been reviewed and completed, SAP BusinessObjects Access Control can either send the cleaned access request back to an IdM solution for provisioning or provision the request itself.
- The SAP BusinessObjects Access Control business role governance process can be integrated with the IdM solution being used to collect all role types and import them into SAP BusinessObjects Access Control. SAP BusinessObjects Access Control then applies the role governance process to the imported roles to cleanse them from access risk before making them available for access requests either in SAP BusinessObjects Access Control or an IdM solution.
- IdM role management can leverage from SAP BusinessObjects Access Control to identify and remediate access risks. In this scenario the IdM system serves as central role repository for role design. An IdM solution sends a Web service request for risk analysis to SAP BusinessObjects Access Control and creates in SAP BusinessObjects Access Control a remediation request, only if access risks are found in a given role. During remediation in SAP BusinessObjects Access Control the roles are cleansed from access risks before they are made available for access requests in an IdM solution.
In addition, communication services have been enhanced to support look-up and call-back between an IdM solution and SAP BusinessObjects Access Control and improve audit tracking of request actions and events.
Frank Rambo, PhD
Frank Rambo, PhD, is managing a team within SAP’s Customer Solution Adoption (CSA) organization working with customers in the SAP analytics area with the objective to drive adoption of new, innovative solutions. Prior to this position, he worked eight years for SAP Germany as a senior consultant focusing on SAP security and identity management. Before he joined SAP in 1999, Frank worked as a physicist in an international research team. He lives in Hamburg, Germany.
You may contact the author at frank.rambo@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.



























