Learn best practices to enhance and optimize the process of structural authorization checks, such as using evaluation paths, creating indexes, and buffering large numbers of structural authorization check objects in the SAP memory via standard SAP reports.
Key Concept
Structural authorization is an authorization concept used to restrict and control access to data stored in time-based structures such as organizational structures, business event hierarchies (training and events management), and qualification catalogs (personnel development) via structural authorization profile assignment or provisioning.
The responsibility of defining structural authorization in a company is challenging for authorization or security administrators who are saddled with the task of enforcing security and control in the SAP ERP HCM system. It is even more challenging when they must manage the possible performance problem of slow response time that arises during structural authorization checks. Although authorization helps to safeguard business data via controlled user access, it has associated performance implications. You need to strike a balance between adequate security provisioning and optimal system performance.
I’ll provide you with best practices and strategies to help you address issues related to slow response time or runtime problems when using structural authorization profiles in SAP ERP HCM. I’ll also discuss how you can:
- Use evaluation paths to guarantee optimal performance of structural authorization checks at runtime
- Use standard SAP reports (e.g., RHBAUS00, RHBAUS01, and RHBAUS002) to reduce access time and response time during structural authorization checks and consequently improve the performance of the process and the entire system
- Create indexes for structural authorization profiles and buffer user data in the SAP memory to improve the performance of structural authorization checks
Authorization profile provisioning in SAP ERP HCM takes different forms, including structural authorization and general authorization. Structural authorization defines which objects in the organizational structure a user is allowed to access, while the general authorization profile defines the data (e.g., infotype and subtype) and access mode (e.g., read and write) the user possesses for these objects. In short, structural authorization controls access to objects while general authorization controls access to data. Structural authorization profile assignment is done via table T77UA (user authorizations). General authorization profile provisioning is done via the profile generator (transaction PFCG). Users’ overall authorization profile is the product of their structural authorization and general authorization profiles.
Define and Assign Structural Authorization Profiles
The structural authorization profile is an important concept in structural authorization checks. Before defining structural authorization, you must correctly map your company’s organizational structure in the system using objects and relationships. As asserted earlier, the structural authorization enforcement depends on the user’s structural authorization profile assignment. To define and assign structural authorization profiles, follow the steps below.
Step 1. Activate the structural authorization main switch via transaction OOAC (HR: Authorization main switch). The authorization main switch, stored in table T77S0 (system table) under the group name AUTSW ORGPD (HR: Structural Authorization Check), allows you to define the behavior of structural authorization checks on HR infotypes. AUTSW ORGPD (Figure 1) influences whether the system analyzes the organizational structure in the authorization check in Personnel Administration.
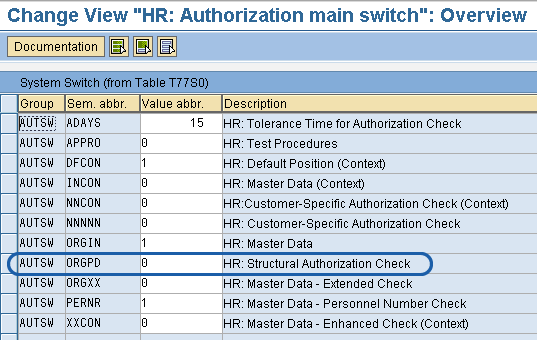
Figure 1
Entries in table T77S0 with default setting for HR: Structural Authorization Check
By default, the switch is set to 0. To activate the structural authorization check, set the switch to 1, 2, 3, or 4. These authorization switch settings define how the system handles situations in which personnel numbers are not linked with the organizational structure. Setting the switch to 1 or 3 allows you to use the organizational unit in the organizational assignment infotype (00001) for the authorization check; otherwise the switch is set to 2 or 4. Furthermore, you can define whether the system should deny (set the switch to 1 or 2) or allow (set the switch to 3 or 4) authorization by default. From the beginning, the following are the attributes of the different switch setting options:
- 1: Organizational unit is evaluated; authorization by default is denied
- 2: Organizational unit is not evaluated; authorization by default is denied
- 3: Organizational unit is evaluated; authorization by default is permitted
- 4: Organizational unit is not evaluated; authorization by default is permitted
Furthermore, the authorization main switch storage in table T77S0 allows you to define the switch differently at the client level.
Step 2. Create the structural authorization profile independently of the users via transaction OOSP (authorization profile) or by maintaining table T77PR (definition of authorization profile) via transaction SM30 or SM31. Structures are protected appropriately by maintaining the entries in this table.
Step 3. Assign the structural authorization profile to a user in table T77UA. You can maintain table T77UA via transaction SM30 or SM31 or by following menu path SAP Customizing Implementation Guide > Personnel Management > Organizational Management > Choose Basic Settings > Authorization Management > Structural Authorization > Assign Structural Authorization. In the screen shown in Figure 2, you can define (or maintain) the user name, authorization profile, and validity period for user authorization.
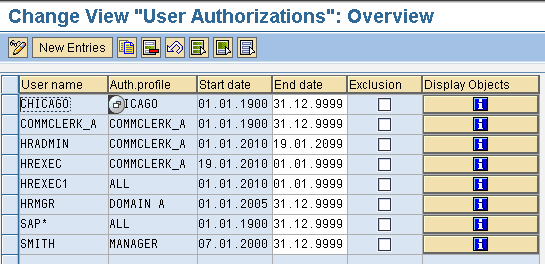
Figure 2
Authorization profile assignment to users
Performance Optimization of Structural Authorization Check
Structural authorization check performance is a factor in the number of read accesses performed when ascertaining whether an object passes the authorization check test. You can take a number of approaches to improve the performance of structural authorization checks, which I describe next in detail.
Evaluation Paths
Evaluation paths are a chain of relationships that exists between objects in a hierarchical structure. They are used for the object selection evaluations process. Basically, an evaluation path defines the start object and determines which object types using which relationships are evaluated by the system. If you strictly adhere to best practices, evaluation paths can greatly enhance structural authorization check performance. The higher the number of different object types with different evaluation paths that exist in the authorization profile, the higher the access times. Furthermore, an evaluation path with an undefined target object type of relationship can cause performance bottlenecks at runtime. To reduce the response time of the structural authorization check and consequently enhance its performance, it is a best practice to:
- Try to limit the number of evaluation paths used in structural authorization checks as much as possible
- Use evaluation paths with specified target objects
Standard SAP Reports
Evaluation paths are less effective when users have large numbers of authorization objects. In such a case, you can use standard SAP reports to address any performance issues. The reports create indexes and store authorization objects in SAP memory, thereby stimulating faster response time during structural authorization checks and consequently enhancing the overall system performance. These reports play important role in achieving this requirement:
- RHBAUS00 (regeneration INDX [INDX system tables] for structural authorization)
- RHBAUS01 (output of views on objects in the structural authorization)
- RHBAUS02 (check and compare table T77UU [user data in SAP memory])
You can use report RHBAUS00 to generate person-specific indexes for structural authorization. The preconditions to executing report RHBAUS00 includes:
- The definition (in table T77UU — save user data in SAP memory) of the users’ structural authorization data that should be stored permanently in the SAP memory
- The definition of the frequency (in days) in which the stored data in the SAP memory is refreshed (Figure 3)
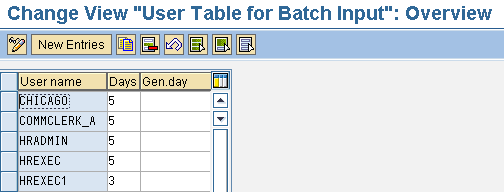
Figure 3
Definition of users and index refresh frequency in table T77UU
You can access Figure 3 via menu path SAP Customizing Implementation Guide > Personnel Management > Organizational Management > Choose Basic Settings > Authorization Management > Structural Authorization > Save User Data in SAP Memory. Alternatively, you can specify the table name in transaction SM30 or SM31. Report RHBAUS00 regenerates indexes for structural authorization profiles of users who have corresponding records in table T77UU. The indexes benefit the defined users in table T77UU by providing quick access to organizational structures thereby enhancing the performance of structural authorization checks.
You can use report RHBAUS01 to carry out data comparison between table INDX and table T77UU. Running this report generates the list of users who have structural authorization data in the SAP memory even though they are no longer available in table T77UU. Also, the report allows you to delete user records from the INDX table that are unavailable in table T77UU (Figure 4).
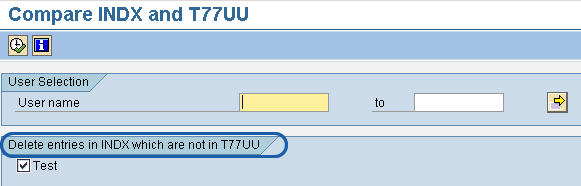
Figure 4
Initial selection criteria for report RHBAUS01 showing the delete option
Indexes for Structural Authorization Profiles
As I mentioned earlier, structural authorization objects for users defined in table T77UU are stored in the SAP memory. This speeds up the process of structural authorization checks. Report RHBAUS02 allows you to define users who have authorization for a large number of objects in table T77UU. You can also delete users with a smaller number of objects from table T77UU. The selection criteria displayed when executing the report via transaction SA38 (ABAP: program execution) is shown in Figure 5.
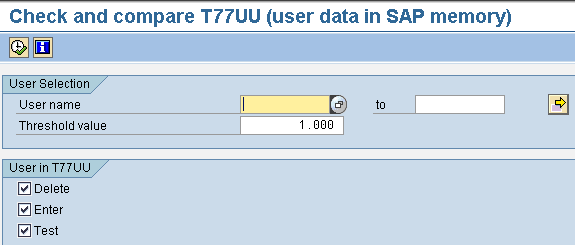
Figure 5
Selection criteria for report RHBAUS02
In the user selection area, you need to provide the name of the user you’re checking in table T77UU. If you do not want to restrict users from the action, leave the field blank. The system retrieves user names from table T77UA, which stores users’ structural authorization (Figure 6).

Figure 6
Content of table T77UA
Furthermore, the value specified in the Threshold value field in Figure 5 controls the number of objects for which a user has authorization in table T77UU. The default threshold value is 1,000. The implication of this threshold value is that users with authorization for more than 1,000 objects are entered into table T77UU while users with fewer than 1,000 are deleted from table T77UU. The User in T77UU area of the initial selection screen of report RHBAUS02 contains three check boxes:
- Delete: If this option is selected, users with authorization of fewer than 1,000 objects are deleted from table T77UU
- Enter: If this option is selected, users with authorization of more than 1,000 objects are added as entries to table T77UU
- Test: If this option is selected, you perform a simulation run of the users that will be processed in a live run of the report
Kehinde Eseyin
Kehinde Eseyin is a security architect. He holds a bachelor’s degree in computer science. He has about 12 years of IT security, governance framework, IS risk, and compliance experience gained by working in numerous global organizations. Over the years, he has demonstrated competencies in security design, information assurance, cyber security, data privacy, threat and vulnerability management, penetration testing, business architecture, project management, IT audit, IS controls framework, and identity and access management.
You may contact the author at eseyinok@gmail.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.