How Accounts Payable Can Improve Fraud Detection with Robotics and Machine Learning
Panelists: Brian Shannon, Dolphin, and Ingo Czok, Hanse Orga Group
Date: Thursday, February 8th
Sponsor: Hanse Orga
Fraud prevention and compliance are pressing issues for global organizations.
Read the transcript to get advice on how to optimize and centralize Accounts Payable and Payments processing to improve compliance and reduce the risk of fraud. By applying new technologies, such as robotics and machine learning, and strategically leveraging cloud services, companies can better protect against fraud and ensure they are working with the right partners, paying the right amounts, and receiving the expected sums.
Kendall Hatch: Hi, everyone. Thanks for joining us for today’s Live Q&A, “Preventing Fraud with Tight End-to-End Security and Integrated AP and Payments Processing.” We’re pleased to be joined today by Brian Shannon from Dolphin, and Ingo Czok from Hanse Orga Group. Brian and Ingo will be presenting on this topic at the SAPinsider Financials and GRC conference.
Thanks to everyone who has asked questions so far. We’re excited to get started. Now, I’ll turn it over to our experts. Thanks for joining us today, Brian and Ingo!
Ingo Czok: Hi Kendall, thanks for the invitation. I´m excited to be here and look forward to the questions.
Brian Shannon: Hi Kendall…we are happy to be here.
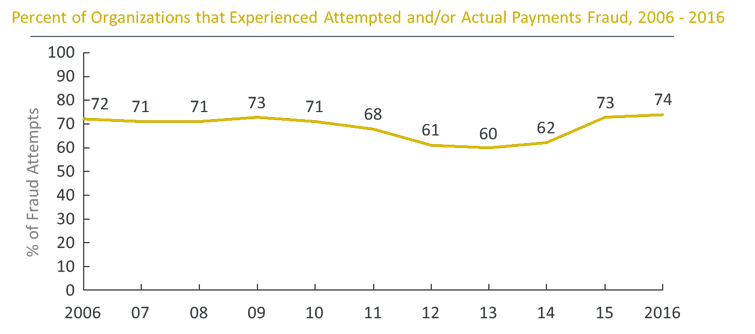
As you know, fraud is a significant issue for all organizations. According to the Association for Financial Professionals (AFP), 74% of companies experienced fraud in 2016.
Ingo Czok: Look at these numbers, quite impressive, I think:
Comment From Matthias: What are the leading causes of fraud? How can I protect my company from fraud attempts?
Ingo Czok: There are many causes for fraud. Typical causes include:
- BEC Scam (Business Email Compromise)
- Trojans and Key-loggers
- Phishing Mails
- Man-In-The Middle Attacks with intercepted payments
- Ransomware
Protection can be accomplished through organizational and technical measures like:
- Centralization
- Segregation of Duty
- Audits
- Standard Operating Procedures
- Business Continuity Strategy
- 2-Factor Authentication
- 4-Eye-Prinicple
- Encryption & Digital Signatures
- Intrusion and Fraud Detection
Comment From Sebastian: How can I gain greater visibility into my entire procure-to-pay process from invoice receipt to payment? How can I secure this process and be alerted to potential fraud attempts?
Brian Shannon: Transparency is your ally when it comes to managing against potential fraud activity. Firstly, insist on centralization of receipt of ALL invoices. Then capture the data electronically from the invoice (eInvoicing receipt is best) and get it into the system as quickly as possible. Once into a dedicated workflow, digital signatures and appropriate authorization levels are required. But that still doesn’t mean that transactions won’t slip through the cracks. Understanding the ways in which fraudulent transactions can occur means that you can establish criteria for creating algorithms to analyze the data and provide early warnings. Checking inbound invoices as well as outbound payments against these algorithms can alert staff at various functions within the organization that something may be cause for concern. Comprehensive reporting and analyses can then provide greater insight.
Comment From Patrick: Which fraud checks can I automate using RPA or ML?
Brian Shannon: Machine Learning can be used to generate new rules based on previous decisions of the Fraud Officer. These rules can then be automated using Robotic Process Automation to deal with low fraud score transactions that do not contain a high risk. The human Fraud Officer can than concentrate on the high-value/high-risk payments.
Comment From Marilyn: How can I use RPA and ML to improve fraud detection?
Ingo Czok: Fraud detection is typically done by a complex set of rules like these: Is the payment going to a known beneficiary? Is the payment within a valid amount range? Etc. These rules will be applied to all the payments and a fraud score is calculated. The resulting payments with a higher fraud score are presented in the fraud monitor to the Fraud Officer, who decides whether a payment is executed or rejected. ML technology can be used to generate new rules based on the decisions the Fraud Officer did in the past.
Comment From Gyani: Is machine learning supported by SAP? Do you use ABAP or some other language?
Brian Shannon: ML is an evolving technology. Some of our proprietary solutions are built within the SAP ecosystem and use the latest toolsets available within SAP (including ABAP), while some are external to SAP and are managed on a stand-alone basis.
Comment From jmr98usa: How do you best tune out false positives?
Ingo Czok: It is always difficult to fine-tune your rules to match each and every real fraud and not come up with too many false positives. ML will help with generating new rules based on previous fraud or non-fraud decisions. Therefore, it is best practice to have a fraud monitor to actually view the transactions with a high fraud score and manually accept or deny those and further train the AI through that process. This is precisely the reason it is important to have human engagement in the process. Balancing the advantages of RPA and AI with human experience leads to more efficient and effective processes and a higher overall fraud prevention result.
Comment From Kumar: What new P2P features can I take advantage of in SAP S/4HANA versus my existing SAP ECC system?
Brian Shannon: SAP does provide a fraud capability as part of the GRC component toolset. We have a proprietary solution that is tightly integrated into the SAP Business Workflow Engine that addresses fraud at the point of invoice receipt as well as part of the outbound payment run. SAP S/4HANA running on the SAP HANA database enables much greater processing capability for reporting and analyzing large volumes of data to better understand and develop algorithms to identify fraudulent transactions.
Comment From Andrew: Will analytical techniques detect a significant proportion of potential frauds? Will machine learning significantly increase the proportion detected or is the main advantage that machine learning helps to prevent the transaction in the first place?
Ingo Czok: Machine learning will increase the quality of the fraud detection because it will learn from the human behavior in identifying real fraud versus false positives.
Comment From EMG97: What are the best ways to test transactions for fraudulent activity?
Brian Shannon: Independent of industry, there are some common traits that exist in fraudulent activities. Characteristics of master data records, transaction amounts, remit to addresses (home vs. business) and even invoice numbering and sequences can be used as early detection warnings.
It is best to examine any realized incidents within your organization first and then test against those for the rest of your transaction inventory.
Secondly, you can begin with a smaller subset categorized by the type of spend or vendor to begin to build evaluation protocols; eventually ramping up to a much more comprehensive evaluation organization-wide.
Additionally, analytics can help detect fraud, although preventing fraud BEFORE it happens should be the first goal.
In our solution, when a potentially fraudulent transaction is detected, it is assigned an individual score. If the total score exceeds the limit set by a corporation, the fraud attempt is grouped according to the risk level and the solution automatically initiates a pre-configured follow-up process, such as:
- Stop the entire payment file that includes one or more suspicious payments
- Block only suspicious payments and execute all other payments
Comment From John: How can I ensure that the payments I make are secure and can’t be intercepted?
Ingo Czok: Payments need to be signed digitally with strong cryptography technology. The payments are hashed first then signed using asymmetric encryption. Staff at corporates have a private and a public key pair and store the private key in a safe place like on a smartcard or within a secure mobile app. The public key is shared with the financial institution. Payments are encrypted with the private key by the corporate and then send to the bank. Banks decrypt using the public key. Would the payment be intercepted and modified, the decryption would not work and the bank will know that it is a fraudulent payment and not execute it.
Comment From Art: Where is it important for me to maintain manual checks in my payment processes?
Brian Shannon: The final decision if a payment is fraudulent or not is always going to be a human interaction. Payments are flagged with a fraud score and enter a Fraud Monitor that a human has to check and decide whether to reject or pass individual payments. The technology can only help to get better fraud scores and reduce the number of manual interactions needed on low risk/value payments.
Comment From Mia: How do I ensure that I’m working with legitimate suppliers? What can I do to qualify my suppliers, mitigate supplier credit risk, and ensure suppliers are regularly screened for potential sanctions?
Ingo Czok: You can use a compliance check that uses internal and external sources to rate suppliers. White & Blacklists from diverse agencies including Dunn & Bradstreet are connected to our compliance monitor. Transactions are first checked against the Whitelists and executed if they match. Those transactions not on the Whitelist are checked against the Blacklists and are sorted out accordingly. The Compliance Monitor then displays the questionable transactions to be acted on accordingly.

Adding to Mia´s question here is a picture of connected agencies for supplier information.
Comment From Srinivas: What if I have different ERP systems? How can I achieve better control and visibility over my P2P processes to prevent fraud?
Brian Shannon: Many organizations have grown through acquisition and along the way have collected a number of ERP and secondary SAP systems. The best way to control fraud is to have the same high-performing and standardized processes on the most centralized basis as possible.
Achieving a standardized process across ERP’s is certainly possible. Built within this process must be the capabilities to better analyze the master records, invoices, and payments for the key fraud indicators. Aggregating the data from these systems to enable an organization-wide evaluation is the key.
Comment From Mary: What’s your experience with implementing RPA in financial processes? Are there any lessons learned that you could share?
Brian Shannon: Robotics is here to stay, yet it is not the panacea. Robotics and RPA can offer great value to the enterprise by cutting costs, eliminating manual errors, and freeing up high-value employees. However, it’s imperative to understand that there is a threshold and “dark side,” if not managed properly. For the classic rules-based RPAs, if the rules get too complex, or get setup by business analysts not familiar with all the nuances of the processes, RPA can produce incorrect results and put companies at risk. This is a classic case where you gain efficiency at the cost of effectiveness. Since people put machines to higher levels of accountability compared to humans, this could be a deathblow to such systems. This problem could be even worse for the Machine Learning-based Robotics systems as the Machine Learning models are notoriously opaque. Therefore companies need to be aware of both the pros and cons of RPA to ensure they’re implementing it for processes that will truly benefit from RPA – and properly balancing it with human oversight and processing.
Comment From Paul: How can Cloud Technology and Managed Services help to protect against fraud?
Ingo Czok: Using a cloud environment ensures that you are using state-of-the-art technical protection like Web-Application Firewalls with constantly adapted rule sets according to the OWASP Top 10 list. A managed service is available for doing the compliance checks and to establish and maintain fraud detection rules according to your profile and needs.
In a hybrid SAP-on-premises and cloud environment a tight end-to-end security is essential.
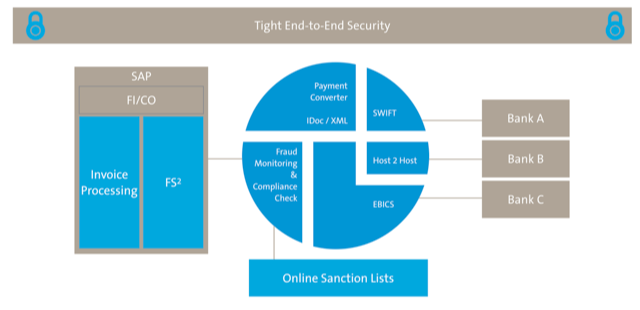
This is in addition to Paul’s question regarding the cloud and managed services options in fighting fraud.
Comment From Mary: Am I more susceptible to payment fraud if my business has a higher percentage of checks vs. electronic payment methods?
Brian Shannon: Yes, checks historically have been a more susceptible payment method. The ability to intercept and modify a check is a big part of the problem. But now that there is an increase in how payments are made via ACH, there are greater incidents of fraud here as well if appropriate steps are not taken proactively.
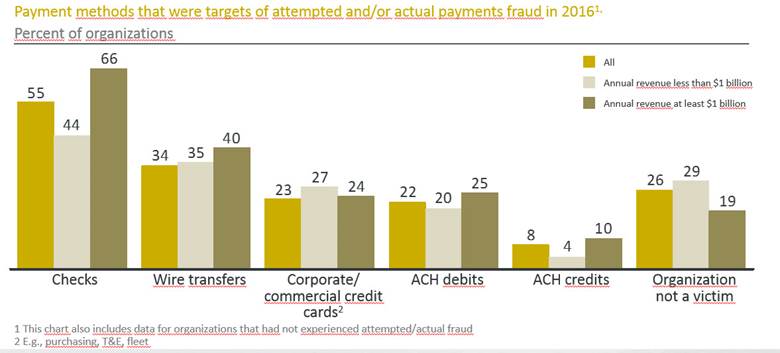
Ingo Czok: To second Brian’s comment on Mary’s question, here are some numbers on the payment methods. In Europe we do not use checks anymore and fully rely on electronic transfers. This has actually decreased fraud because it is much harder to compromise digital signatures rather than real ones.
Comment From Bukky: What about Bank Accounts? Is there any way to put additional fraud controls across the many bank accounts we manage?
Brian Shannon: Centralizing bank account information in ERP systems, or using ERP integrated solutions, provides instant visibility into:
- Open, closed, active, or inactive accounts
- Authorized document signatories
- User limits for various bank services
- Corporate bank account and signatory information
- Mandate information (authorizations)
Corporations can centrally direct, monitor, and manage processes such as the opening and closing of accounts and setting signing limits for services.
Changes to an account (e.g., opening, maintaining or closing an account, and adjusting mandates, authorizations and signatory information) become an activity or mandate in the system and follow the corporation’s preconfigured approval workflow. Any changes to bank account information are automatically updated in the corporation’s ERP platform, and are immediately communicated to the corporation’s bank.
Kendall Hatch: That about wraps up our time for today – thank you to everyone who joined us today for an engaging conversation! Brian and Ingo will present at SAPinsider Financials and GRC conference in Las Vegas.
A special thanks to Brian and Ingo – we’re so glad you could join us today!
Brian Shannon: Thanks for your time everyone. If you have any further questions, please feel free to reach out at brian.shannon@dolphin-corp.com.
Ingo Czok: Thanks everybody for the great questions. If you want to follow up, you can always reach me at czok@tembit.de