You have the option in the Objective Setting and Appraisals (OSA) component to use structural authorizations to control access to appraisal documents. Two scenarios help you to understand the concept.
Key Concept
Structural authorizations for HR personnel data are used to grant authorizations based on objects and relationships in organizational structures. You assign structural authorizations to a user with a structural profile. The structural profile contains the following main characteristics:
• Object ID of the root object (which can be dynamically determined through a function module). This is the starting point within the organizational structure, from where authorizations are granted.
• Evaluation path along which the objects are evaluated. This evaluation path identifies all the objects to which the specific user has access.
In part 1 of this series, we explained which standard roles apply for the Objective Setting and Appraisals (OSA) component and which standard HR authorization objects and structural authorizations are relevant for setting up a secure performance management process. In part 2, we focus on the OSA-specific structural authorization concepts that you can use to control access to appraisal documents for persons from defined areas in Organizational Management (OM).
Note
Our explanations apply to R/3 Enterprise HR Extension Set 1.10 and 2.00 as well as to mySAP ERP 2004. This article assumes the reader has a basic understanding of the data model in OM.
Example
An example of the configuration for a structural profile is shown in Figure 1. The user has access to all organizational units, positions, and persons that are assigned to organizational unit number 1 PC4YOU.
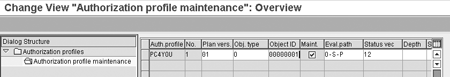
Figure 1
Example for a structural profile entered in table T77PR
You can use structural authorizations with context-sensitive access control to allow access to different types of information — for example, infotypes in Personnel Administration (PA) or appraisal templates in OSA — for different areas within the organizational structure. (See the explanation of authorization object P_ORGIN/P_ORGINCON in part 1 of this series for more detail.)
By assigning the structural profile to the appropriate authorization object in the user roles, you achieve context sensitivity:
• Authorization object P_ORGINCON for a context-sensitive authorization check on different infotypes in PA
• Authorization object P_HAP_DOC for a context-sensitive authorization check on different appraisal documents
We’ll give two examples of context- sensitive access via these authorization objects, focusing on two basic implementation scenarios:
• Scenario A — use structural authorizations in OSA but not in PA
• Scenario B — use structural authorizations in OSA and in PA (including context-sensitive access)
Scenario A: Structural Authorizations in OSA Only
You activate the structural authorization checks only for OSA — that is, for accessing personnel appraisals. In PA, you do not use structural authorization checks.
The technical prerequisites are the following: Activate the switch HAP00/AUTHO in table T77S0 and grant PA authorizations via authorization object P_ORGIN (without structural HR authorizations). Enter a structural profile in the authorization object P_HAP_DOC together with the user in table T77UA.
If, in this authorization object, the default value * remains in the authorization profile field and you do not enter the user in table T77UA, the system interprets this value as structural profile ALL. That is, the user has the authorizations to access all the appraisal documents of the persons to which he/she has access granted via P_ORGIN. If you enter no value or an invalid value in the authorization profile field for the authorization object P_HAP_DOC, the user cannot access any personnel appraisals. However, the user can access the corresponding infotypes in PA.
Use Case
The international company PC4YOU has two appraisal templates, Objective Setting Agreements and Qualification Appraisals. The Objective Setting Agreements are only for employees in Central Europe and the Qualification Appraisals are only for the US. Therefore, administrators working for the whole PC4YOU need context-sensitive access to the appraisal documents.
For PA data, differentiation is by employee group, not by country. Every administrator should be able to access infotypes 0000-0006 of all employees in employee subgroup Executive employees (Figure 2).
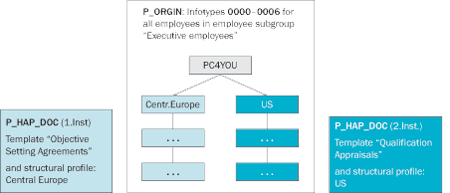
Figure 2
Structural authorization settings for scenario A
Authorizations
The administrator should be able to view and edit the appraisal documents for Central Europe based on the template Objective Setting Agreements only. For the US, the administrator should be able to view and edit the appraisal documents based on the template Qualification Appraisals only. As a consequence, the administrator is not able to view or edit Qualification Appraisals for employees in Central Europe. The country responsibility areas are represented as relationships in OM and as such are used in structural profiles (structural profile Central Europe, structural profile US).
The role requires two instances of the authorization object P_HAP_DOC that differ in the fields shown in Table 1. For access to PA data, the setting for authorization object P_ORGIN shown in Table 2 is required.
|
Appraisal template field |
Authorization profile field |
| 1. Instance |
Objective Setting Agreements |
Central Europe |
| 2. Instance |
Qualification Appraisals |
US |
|
Table 1
|
Differing P_HAP_DOC settings for Central Europe and US |
|
Infotype field |
Employee subgroup field |
| 1. Instance |
0000–0006 |
“Executive employees” |
|
Table 2
|
Setting to allow access to PA data |
Scenario B: Structural Authorizations in OSA and PA
Note
As the combination of different structural profiles for a given user can become very complex, you can use the standard report
RHUSERRELATIONS to get an overview of which objects a user can access via which authorization profile. As of Web Application Server (Web AS) 6.40, you can also start this report directly from the table
T77UA by clicking on the information icon (
Figure 3).
For more information, refer to the following SAPexperts articles by A.J. Whalen: “Conquer Context Problems in HR Security,” and “Improve HR Authorization Audits with the ‘Display User Assignments’ Report.”
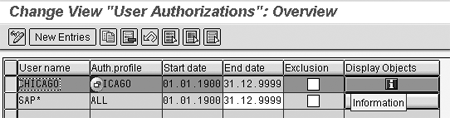
Figure 3
Start report RHUSERRELATIONS
In this scenario, the context-sensitive, structural authorizations are active for OSA as well as for PA. That means you can control access to HR master data and personnel appraisals in OSA in a context-sensitive manner.
The following settings are required: Activate the switch HAP00/AUTHO in table T77S0 for OSA. Additionally, activate the switches AUTSW/ORGPD and AUTSW/INCON in table T77S0 for structural and context-sensitive authorization in PA. As a consequence, the system checks the authorization object P_ORGINCON when accessing PA data. You also must enter a structural profile into the relevant fields of authorization objects P_ORGINCON and P_HAP_DOC.
Use Case
In the international company PC4YOU, all administrators have access to the infotypes 0000, 0001, and 0002 of all employees in the employee subgroup salaried staff. In addition, administrators have more authorizations for the employees within their area of responsibility that correspond to the countries. In this example, the administrators have authorizations to maintain all the infotypes and the appraisal documents of the template Performance Check of all their employees within their responsibility area (Figure 4).
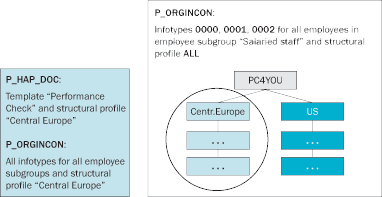
Figure 4
Structural authorizations settings for scenario B
Authorizations
The authorizations for the authorization object P_ORGINCON and P_HAP_DOC shown in Tables 3 and 4 are required for the relevant fields. As described in the scenarios above, you must enter the user in table T77UA to be able to get the structural authorizations. If you use the Business Add-In (BAdI) “Determine user profile” from table T77PR (HRBAS00_GET_PROFL) as opposed to maintaining table T77UA manually, note that you must also consider the structural profiles from the authorization object P_HAP_DOC.
|
Infotype field |
Employee subgroup field |
Authorization profile field |
| 1. Instance |
0000, 0001, 0002 |
“Salaried staff” |
* (all) |
| 2. Instance |
* (all) |
* (all) |
“Central Europe” |
|
Table 3
|
Required authorizations for P_ORGINCON |
|
Appraisal template field |
Authorization profile field |
| 1. Instance |
“Performance Check” |
“Central Europe” |
|
Table 4
|
Required authorizations for P_HAP_DOC |
When a specific template, appraiser, appraisee, or a combination of these should have additional checks for authorization, you can achieve this by creating an implementation for the BAdI definition “Appraisal Document — Authorization Check” (HRHAP00_AUTHORITY). You can also exclude documents from the standard authorization check via this BAdI.
Bianka Piehl
Bianka Piehl has been working as HR Consultant since 1999, joining SAP HR Consulting 2003. Her consulting activities were focused on the areas of Organizational Management, Personnel Development and Performance Management, including related Self-Service scenarios. Since May 2005 she is working for SAP Solution Management, being responsible for Shared Services in HCM.
You may contact the author at bianka.piehl@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Maurice Hagen
Maurice Hagen started at SAP in 2000 as a developer for Dutch Payroll. In 2001 he joined the Performance Management project where he has been involved from the start with the specification, design, and development of the Objective Setting and Appraisals module.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.
Martina Schuh
Martina Schuh joined SAP in 1999. She has been dedicated to the subject of HCM Analytics from the outset. Since 2001 she has been product manager for HCM Analytics and Talent Management, including Employee Performance Management and Succession Planning.
You may contact the author at martina.schuh@sap.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.












