SecurityBridge
SecurityBridge is the leading provider of a comprehensive, SAP-native cybersecurity platform, trusted by organizations worldwide to safeguard their most critical business systems. Our platform directly integrates real-time threat monitoring, vulnerability management, and compliance capabilities into the SAP environment, empowering organizations to protect their data’s integrity, confidentiality, and availability with minimal manual effort. With a proven track record, including a stellar customer success rating and over 5,000 SAP systems secured globally, SecurityBridge stands out for its ability to accurately provide a 360° view of the SAP security posture, ease of use, rapid implementation, and transparent licensing.
Featured Solutions
-
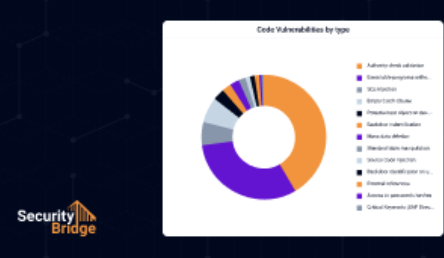
Threat Detection for SAP
Gain real-time visibility into SAP threats, centrally monitor malicious activities, and prioritise risks to protect critical systems. Guided security provides up-to-date controls to help your team detect threats.
-
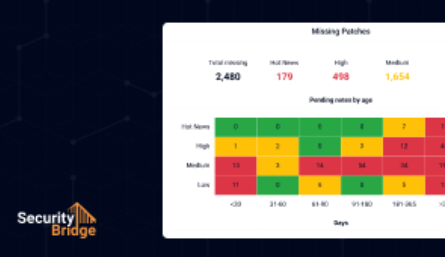
Patch Management for SAP
Reduce risk with timely SAP security patches and guided implementation of relevant Security Notes. Get tailored insights into their impact on your systems and streamline patching with automated or guided procedures, reducing workloads and enhancing security.
-
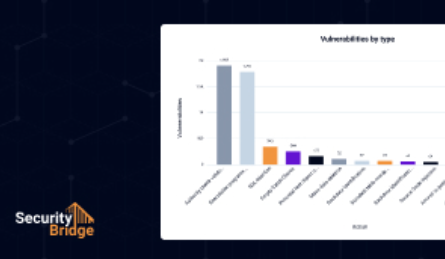
SAP Compliance Automation
Centralised compliance monitoring offers a unified view of system changes and their impact on SAP security and compliance. Preconfigured checks ensure best practices with minimal configuration, while integrated security events provide a 360° view of your security posture
Featured Content
-

Customer Stories
We are passionate about delivering a robust platform that makes our customers happy and, most importantly secure. We act as an extension of the SAP team to drive security processes, and our customers love us for it. See how leading organizations are securing SAP with SecurityBridge.
-
AI & SAP Security: Benefits, Risks and Prerequisites
Discover how integrating AI into SAP can enhance cybersecurity, while also understanding the associated benefits and potential risks.
-
Multimedia Centre
-

Security Automation: The Need for a Last Line of Defense
Watch our webinar on Security Automation, featuring a special guest from Answerthink. Discover how you can automate your SAP security and compliance processes to improve your security posture and implement a last line of defense for your mission-critical SAP landscape.
-

Mastering NIST and CISA Compliance for SAP
Watch this enlightning webianr here we simplify the NIST and CISA regulatory frameworks, map CISA guidelines to SAP instances, and showcase how the SecurityBridge platform can assist you in achieving your SAP compliance needs.
Articles / Case Studies / Videos
-

Securing SAP Systems: Strategies to Minimize Attack Surface and Protect Sensitive Data
Reading time: 1 mins
SAP systems are susceptible to cyber attacks due to configuration errors, access control issues, and software bugs, highlighting the need for continuous monitoring and robust security measures.
-

Interventions for SAP Fiori Security
Reading time: 3 mins
This article highlights the importance of securing the SAP Fiori platform through measures such as encrypted communications, user authentication, local data storage protection, compliance with regulations, virus scanning, and protection against UI redressing attacks to ensure a safe and intuitive user experience. Sales rely on the user experience; improving it is the edge every organization…
-
-

The Ultimate Guide to SAP RFC: Streamlining Communication and Ensuring Robust Security
Reading time: 3 mins
Securing and streamlining communication between SAP systems and external applications is critical for optimizing efficiency; this is where the SAP Remote Function Call (RFC) comes into play. RFC offers seamless integration and coherent communication between software systems, which today are indispensable components to an organization’s success in this rapidly changing digital world. This article will…
-

Enhancing SAP Security Through McCoy & Partners and SecurityBridge Collaboration
Reading time: 1 mins
McCoy & Partners, an independent SAP service provider in the Netherlands, addresses the security risks of SAP systems for mid-sized companies lacking IT expertise by offering comprehensive protection through a partnership with SecurityBridge.
-

Why MSP PASàPAS Selected SecurityBridge To Protect Customers’ SAP Systems
Reading time: 1 mins
PASàPAS specializes in helping small to midsize enterprises design and convert SAP systems to S/4HANA while addressing cybersecurity needs through partnerships with established security organizations, thereby simplifying the complex management of SAP for clients with limited IT resources.
-

SecurityBridge – Case Study: SAP Security for the pharmaceutical industry
Reading time: 1 min
Faced with resource restrictions and overwhelming amounts of data, this company needed a solution that could be implemented with little internal resources and within a tight schedule. This company had previously worked with a platform that produced false positive data that wasted time and resources to address. Although the company is aware of the importance…
-

The Patch and Vulnerability Management Symbiotic Relationship
Reading time: 1 min
IT professionals turn to patch management and vulnerability management procedures to mitigate hackers. Each process is unique; however, both are frequently used. Vulnerability management covers many risks, whereas patch management concentrates on identifying relevant patches and timely implementing security-relevant software updates for specific bugs or faults. Vulnerability management and patch management are both required processes…
-
-

Sanofi replaces traditional SAP security with SecurityBridge
Reading time: 1 min
Sanofi, a global biopharmaceutical company focused on human health, selected the SecurityBridge Platform to replace a traditional security tool that had been in use for three years. With a vast SAP enterprise this was not an initiative that was taken lightly. In 2020 Sanofi took that decision based on concerns that their business requirements had…
