Secure Your ABAP Code Against Attack
What’s New with the 7.51 Release of SAP NetWeaver Application Server, Add-On for Code Vulnerability Analysis
Modern business landscapes are increasingly large, heterogeneous, and complex. This trend has made securing enterprise software a challenging endeavor. Adding to this challenge is the need to quickly adjust to rapidly changing business requirements. To meet new needs as they arise, many organizations use custom code to extend the functionality of their business software, such as SAP Business Suite, which increases the amount, and complexity, of the code that needs to be tested and secured.
The stakes are high — SAP systems hold valuable data, and insecure software is a common cause of cyberattacks, which can have dire consequences, including negative publicity, penalties, and lost revenue. Unfortunately, many organizations become aware of vulnerabilities only after a breach has occurred. Securing custom code after the fact is extremely expensive — according to studies, it costs 30 times more to fix security issues after a breach than to build security into your code at the beginning of the design process.1
To prevent cyberattacks and avoid costly remediation, organizations must adopt reliable methods for testing new or altered code during development, before a breach occurs. To help with this task, SAP provides customers with a powerful, integrated tool as part of SAP NetWeaver Application Server (SAP NetWeaver AS) ABAP that scans ABAP source code for vulnerabilities: SAP NetWeaver AS, add-on for code vulnerability analysis.
This article looks at how SAP NetWeaver AS, add-on for code vulnerability analysis leverages integration into the ABAP development infrastructure to make it easy to scan, analyze, and secure your ABAP source code, and then examines the latest enhancements delivered with SAP NetWeaver AS ABAP 7.51 — including remote code analysis and baseline functionality — to help you minimize risks and errors and ensure overall quality in productive system landscapes. You will also get a sneak peek at some upcoming features for addressing evolving threats to your code.
An Integrated Approach to Securing Custom Code
SAP NetWeaver AS, add-on for code vulnerability analysis analyzes user input and data flow in source code to find vulnerabilities that can cause issues down the road, and provides guidance on how to address identified issues. Originally created by the SAP development team for internal testing, the tool was released to SAP customers in September 2013 (see the sidebar “Software Testing at SAP” for more on how SAP secures its application source code). SAP NetWeaver AS, add-on for code vulnerability analysis is a separately licensed tool that is available for use with SAP NetWeaver AS ABAP.2
SAP NetWeaver AS, add-on for code vulnerability analysis is seamlessly integrated into the ABAP Test Cockpit, which is a central, extensible infrastructure for performing functional, performance, and security code checks on ABAP development objects. Based on the Code Inspector, and integrated into the ABAP development environment, the ABAP Test Cockpit comprises a set of check variants that run smoothly alongside one another (see Figure 1).

SAP NetWeaver AS, add-on for code vulnerability analysis is used via the ABAP Test Cockpit and has access to all ABAP Test Cockpit features, such as new features included in SAP NetWeaver AS ABAP 7.51. It allows developers to take advantage of the ABAP Test Cockpit’s streamlined quality assurance processes and tight integration with ABAP development tools. This tight integration enables developers to easily launch code checks — including the security checks provided by SAP NetWeaver AS, add-on for code vulnerability analysis — from tools such as the ABAP Workbench (transaction SE80), the ABAP Editor (transaction SE38), and the Eclipse-based ABAP development tools for SAP NetWeaver (ABAP in Eclipse).
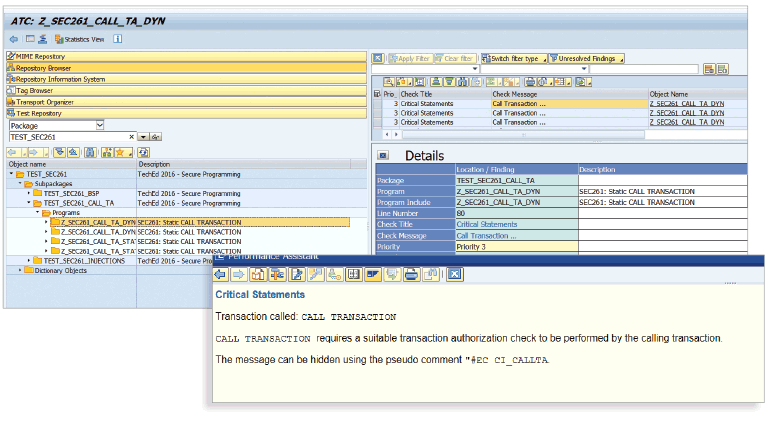
SAP NetWeaver AS, add-on for code vulnerability analysis provides a range of features for securing source code. Developers can launch checks for single objects or groups of objects. Quality assurance teams can schedule automated test runs, enable automatic test failure notifications, and aggregate test results for analysis. Developers can also adjust the priority of each check to meet test run or risk policy requirements, or to follow a phased approach to enabling checks, which can help increase acceptance and use of the checks. Once an issue is found, developers can navigate directly to documentation that explains how to fix it and avoid it in the future (see Figure 2), or to workflow functionality to create an exemption. The tool’s sophisticated data flow analysis, performed at the compilation unit level, combined with the exemption feature ensures minimal false positives.
A previous SAPinsider article provided a detailed introduction to SAP NetWeaver AS, add-on for code vulnerability analysis and how it works — here, we explore some of the new features delivered with SAP NetWeaver AS ABAP 7.51 that enhance the capabilities of this tool.
What’s New with 7.51?
SAP NetWeaver AS ABAP 7.51 delivers several new features for testing ABAP source code with the ABAP Test Cockpit, two of which are particularly useful when performing security checks with SAP NetWeaver AS, add-on for code vulnerability analysis — the ability to perform remote code analysis and to define baselines for test runs. Let’s take a closer look at how these features can help you secure your code.
Remote Code Analysis
Remote code analysis is a key new feature delivered with SAP NetWeaver AS ABAP 7.51 for the ABAP Test Cockpit. This functionality enables you to use the latest checks available in 7.51, including the security checks of SAP NetWeaver AS, add-on for code vulnerability analysis, to analyze custom-developed code in older SAP NetWeaver systems — a critical capability in the face of increasingly sophisticated and frequent cyberattacks. Prior to 7.51, code checks had to be performed locally on the system containing the code, meaning that each and every system had to be upgraded to the latest SAP release or support package level in order to use the latest checks and functionalities for testing. This led to significant administrative overhead.
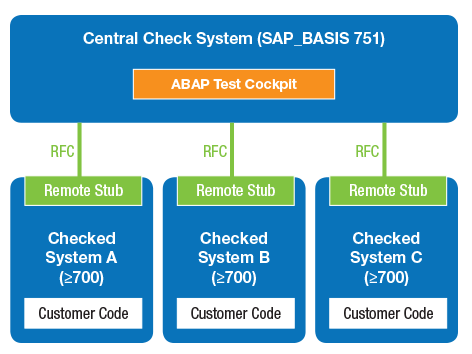
With the new remote code analysis feature delivered with 7.51, you need only set up one SAP NetWeaver AS ABAP system, running SAP_BASIS 751 only, in your SAP system landscape to serve as a central check system. From this central system, you can run checks via the ABAP Test Cockpit on any SAP NetWeaver AS system in your landscape that is running SAP_BASIS 700 or higher — there is no need to upgrade every single system to 7.51 to take advantage of the latest security checks. In addition to reducing administrative overhead and saving time, this capability provides access to the features customers with older systems need to ensure the quality of their custom code and comply with increasingly complex corporate security requirements.
So how exactly does a remote check scenario work? Administrators simply deploy a remote stub to each system to be checked (see SAP Note 2270689), which the central check system accesses via a remote function call (RFC) connection (see Figure 3). These remote stubs return a model of the custom code to the central check system, where it is then analyzed using the checks provided for potential security vulnerabilities. The check variant used to perform the checks, which are RFC-enabled, is maintained by administrators in the central check system.3
In addition to providing a means to apply the latest checks to older systems, a remote code analysis scenario offers several other advantages. It enables a centralized approach to checking multiple SAP systems and applying one quality standard across the entire system landscape, regardless of the release used in local development systems. It is also a low-effort, low-impact installation that will not affect existing business processes.
The remote code analysis functionality included with 7.51 is a valuable tool for quality assurance teams working in the central check system — going forward, SAP’s development team is working on making this functionality available to developers working in remote systems as well. This capability will enable developers to execute checks, view and correct findings, request exemptions, and check transports before release, all in the local development system.
Baseline Functionality
Another new feature delivered with 7.51 that adds valuable functionality when using SAP NetWeaver AS, add-on for code vulnerability analysis is the ability to configure a baseline for static code analysis. This feature enables customers that have legacy debts in their existing code to ignore these expected findings and instead focus their test runs on new or recently changed code. This enables customers to start their testing with clean code and create a separate project to work on the findings from their legacy coding. It also allows for the development of new functionalities without an overload of code corrections.
The baseline functionality enables the ABAP Test Cockpit to isolate errors found during the execution of a check variant and exclude them from subsequent test run results by adding them to the baseline, where they are treated as a special kind of exemption. This approach helps developers improve the efficiency of their testing processes by isolating the code that is most in need of attention, which is particularly useful when you need to secure business-critical applications against potential cyberattacks.
The baseline feature is accessed via the ABAP Test Cockpit administration tool (transaction ATC), which displays a list of results of executed checks. To add a check result to the baseline, you simply select it from the list of results and then specify the handling for those results during subsequent test runs. You can choose to suppress the findings (exclude all findings from the check results list); exempt the findings (include the findings in the check results list, marked as exempted); or assign a low priority to the findings (the findings will appear lower in the check results list).
Figure 4 shows the handling options for a check result being added to the baseline.
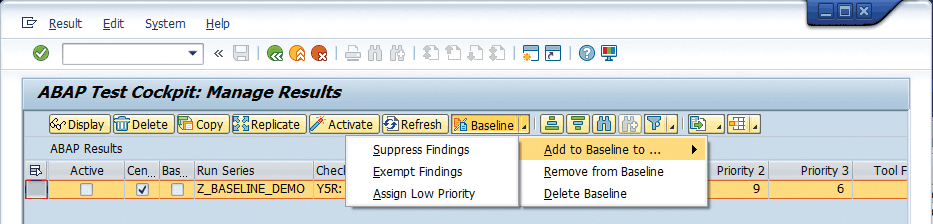
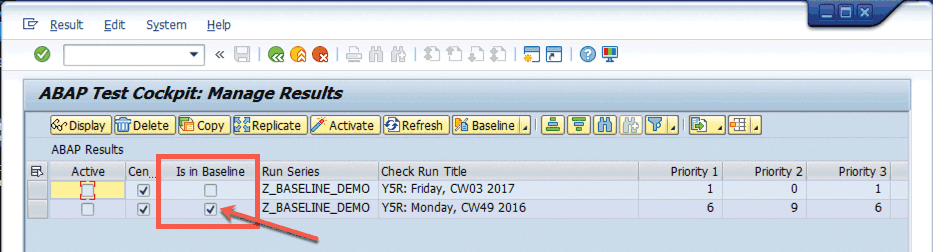
Figure 5 shows the check results list with the baseline selections reflected — in this case, added to the baseline with the findings exempted.4
The baseline is effective as long as the related code sections remain unchanged. If the code does change, you will need to correct the coding and the check will automatically become active again for the modified code section. You also have the option of adding or removing individual findings from the baseline as your needs change (if the immediate removal of all SQL injection flaws becomes a high priority, for instance) or even deleting the baseline entirely and resetting the test system to its original state (if the overall security testing concept is renewed, for example).
Looking Ahead: New Security Checks
Regardless of how robust your security tools are, protecting against cyberattacks is a moving target that requires new ways of securing your code, and SAP continues to add new features to support you in this task. Support package 1 for SAP NetWeaver AS 7.51, due for release in January 2017, includes a variety of new security checks for use with SAP NetWeaver AS, add-on for code vulnerability analysis.
Here is a look at a few of the planned features that will help keep your code safe from evolving threats:
- Potential abuse of URL redirect: Vulnerabilities are introduced wherever external data (such as user input) is used as a source for URL redirects. This check evaluates the potential for attackers to direct victims to other websites.
- Missing content check during HTTP upload: This checks if the method IF_HTTP_REQUEST~GET_DATA( ) is called without the parameter VSCAN_SCAN_ALWAYS, which can lead to cross-site-scripting (XSS) attacks via file upload (MIME sniffing). More detail is available in the SAP NetWeaver Security Guide and in SAP Note 1714836.
- Potential infiltration of harmful SQL statements or conditions when calling a specific method: Security problems can occur when external data, such as user input, is processed unchecked. This check evaluates whether input validation is performed before data is processed. SAP Note 1852318 provides further information about how to protect against SQL injections.
- Read access to sensitive database tables: This checks if there is read access to database tables that are declared as sensitive.
- Write access to sensitive database tables: This checks if there is write access to database tables that are declared as sensitive.
- Call of a procedure with a hard-coded password: This checks if a method or function is called with a hard-coded password, which can compromise system security — anyone who can access the source code has access to the hard-coded password.
These are just some of the security checks planned for future release. SAP is continuously monitoring the security landscape and working to ensure that customers have the tools they need to ensure the security of their software.
Summary
While technology that provides a competitive edge is a business imperative, vulnerable software is a prime entry point for compromising an enterprise. With SAP NetWeaver AS, add-on for code vulnerability analysis, and the powerful new features for the ABAP Test Cockpit delivered with SAP NetWeaver AS ABAP 7.51, you can continue to develop innovative and effective software without worrying about introducing security risks to your organization.
Learn more about how to ensure secure ABAP code in your SAP business systems with SAP NetWeaver AS, add-on for code vulnerability analysis at https://wiki.scn.sap.com/wiki/display/Security/SAP+NetWeaver+Application+Server%2C+Add-On+for+Code+Vulnerability+Analysis.
1 Alan Pearson, “Why It’s Important To Squash Vulnerabilities Early In The Software Development Lifecycle,” The Security Innovation Europe Blog, March 6, 2014. [back]
2 The tool is available for use with the following releases: SAP NetWeaver AS ABAP 7.0, enhancement package 2, support package 14; SAP NetWeaver AS ABAP 7.0, enhancement package 3, support package 09; SAP NetWeaver AS ABAP 7.3, enhancement package 1, support package 09; SAP NetWeaver AS ABAP 7.4, support package 05 and later; and SAP NetWeaver AS ABAP 7.51. [back]
3 Additional details on configuring remote security checks with ABAP 7.51 are available from the SAP Help Portal site. [back]
4 Additional details on the baseline functionality delivered with ABAP 7.51 are available from the SAP Help Portal site. [back]