Protect Your SAP Systems from Cyberattacks
by Martin Müller and Arndt Lingscheid, SAP SE
Cyberattacks on systems that hold valuable and sensitive data, such as SAP systems, continue to rise at a significant rate. Internet of Things devices have emerged as a focus point, with attacks rising 300% in this area, and the total number of data breaches and records exposed increasing by 33% and 112%, respectively, in the first nine months of 2019 compared to mid-year 2018. The costs of these attacks are rising as well — one Accenture study found that the average cost of cybercrime is $13 million, an increase of 72% over the last five years. Compounding the situation, it takes 279 days on average for an attack to be detected and successfully tackled.
Explore related questions
To help protect its own systems, SAP began developing a monitoring solution to detect and respond to cyberattacks more than six years ago, and in March 2015, SAP released the solution for customer use as well. SAP Enterprise Threat Detection is a security information and event management (SIEM) tool that uses log data to provide real-time insight into suspicious activity taking place in enterprise systems, enabling organizations to quickly identify threats as they are happening and address them before serious damage occurs. The tool enriches the monitored log data with contextual data — such as the role or location of a system where a suspected attack has occurred — to make analysis and remediation faster and easier.
This article provides SAP competency center leads, CISOs, and CIOs with an update by looking at the setup options for meeting different requirements and how the tool addresses pressing needs for protecting modern SAP landscapes.
Meeting Different Needs with a Tailored Approach
SAP Enterprise Threat Detection uses the real-time processing capabilities of SAP HANA to manage external and internal cybersecurity threats to your data. As shown in Figure 1, it first extracts log data from source systems — such as SAP Cloud Platform, SAP NetWeaver (ABAP and Java), SAP HANA, and non-SAP systems — into SAP HANA, where it runs attack detection patterns (custom or predefined templates that automatically recognize attacks) on the data using streaming analytics and generates alerts for any detected activities. Users can visualize the results and interact with the data through the analysis and monitoring tools and dashboards provided in the tool’s user interface.
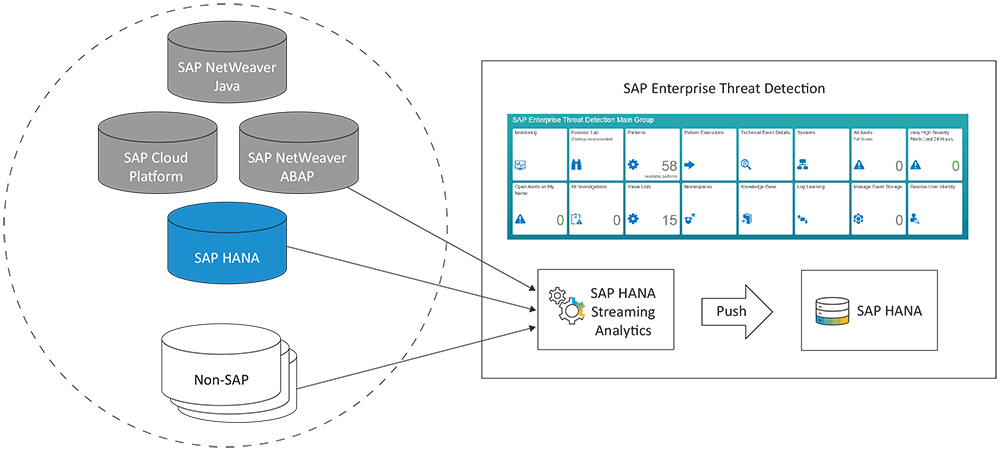
Figure 1 — SAP Enterprise Threat Detection extracts log data from source systems, performs analysis, and provides monitoring and analysis tools
When it comes to operating the tool in customer environments, SAP provides a tailored approach to support organizations with different needs. There are four options for operating SAP Enterprise Threat Detection, one of which is new with release 2.1. The approach best suited to an organization’s landscape can be very different depending on that organization’s unique requirements. Let’s take a closer look at the options and when it makes sense to use which.
The “Alarm System” Approach
Businesses that want to focus and protect only the most sensitive data and assets stored in their SAP systems, rather than monitoring the entire SAP landscape, use the “alarm system” approach, which is available as of release 2.1 of SAP Enterprise Threat Detection. This type of smaller, focused scenario often involves financial, customer, manufacturing, and employee data variants. In small environments, only a subset of attack detection patterns (for example, 10 patterns instead of the 130 that are included in the standard content package) are used to reduce the efforts of those involved (usually Basis administrators).
The advantage of the alarm system approach is that Basis administrators typically can run SAP Enterprise Threat Detection themselves, without the assistance of system administrators. System administrators need only check the status of the system’s health twice a week (Monday and Friday, for instance) and check any generated alerts.
The Full-Blown SIEM Approach
Those that do not use the alarm system approach use a full-blown SIEM approach — they run SAP Enterprise Threat Detection across their entire SAP system landscape to holistically protect their assets. With this scenario, most SAP customers integrate SAP Enterprise Threat Detection with an existing SIEM solution.
Many organizations use these solutions to collect log and event information from various systems on a central server, which acts as a security console for monitoring security and audit-related incidents. One of the major challenges with these solutions is consistently analyzing events, especially from large application systems such as SAP systems — a task for which SAP Enterprise Threat Detection is designed. Combining SIEM solutions and SAP Enterprise Threat Detection brings the best of both worlds together, and consolidates all relevant security and incident and event information in a single console.
This approach can also help reduce costs. Processing all SAP log data directly in an SIEM solution can be costly, since SIEM solutions are usually licensed by data volume. To reduce the volume, and in turn the cost, you can first analyze the data in SAP Enterprise Threat Detection and forward only alerts to the SIEM solution. SAP Enterprise Threat Detection also provides ready-to-use content, such as attack detection patterns, based on an in-depth understanding of SAP logs, so there is no need to create this content in the SIEM solution.
Figure 2 shows the side-by-side installation of SAP Enterprise Threat Detection and an SIEM solution and the different communication channels between the two systems. SAP Enterprise Threat Detection receives log data from its own detectors as well as SIEM providers such as IBM QRadar, Splunk, and ArcSight via User Datagram Protocol (UDP) or Transmission Control Protocol (TCP), and enables these providers to pull alerts from SAP Enterprise Threat Detection via a REST-based application programming interface (API) using standard interface protocols such as Log Event Extended Format (LEEF), Common Event Format (CEF), and JavaScript Object Notation (JSON). SAP Enterprise Threat Detection can also send alerts to users via email.
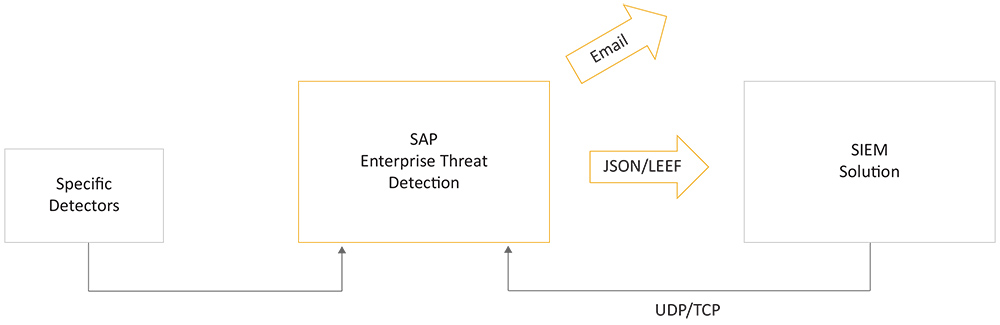
Figure 2 — SAP Enterprise Threat Detection integrates with an existing SIEM solution in a full-blown SIEM scenario
The Managed Service Approach
SAP customers that do not have the knowledge and skills to run and support the use of SAP Enterprise Threat Detection on their own, but want to take advantage of the benefits of a monitoring tool, can use the managed service offerings from SAP and SAP partners, which provide customers with infrastructure and operating support.
There are two variants of the managed service scenario available for SAP Enterprise Threat Detection (see Figure 3). The first scenario is for customers that do not want to run an SAP Enterprise Threat Detection system themselves — these customers are looking for a hosting partner to take care of running the tool in an infrastructure-as-a-service (IaaS) environment. The second scenario is for customers that are running SAP Enterprise Threat Detection themselves on premise, but need operational support from experts when customizing the tool, investigating the alerts it generates, and reacting appropriately in the event of a cyberattack. These scenarios require cloud integration or an open connection to a server on the internet.
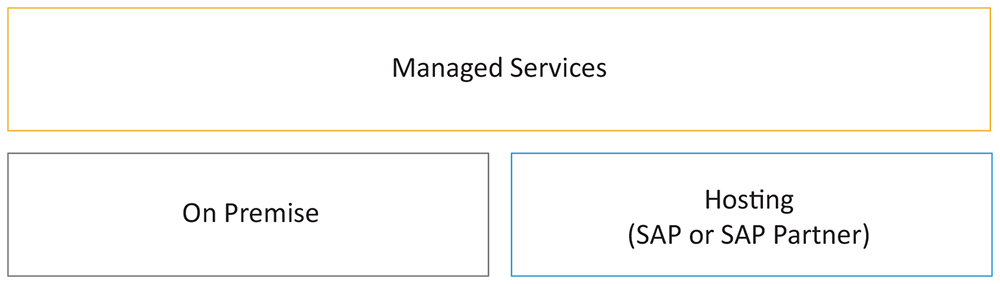
Figure 3 — Managed service options for SAP Enterprise Threat Detection include a hosted option and an option for on-premise support
The Self-Run On-Premise Approach
For those that have the necessary skills and understanding of SAP Enterprise Threat Detection and want full control, there is the option to run and operate the tool on their own, implemented fully on premise. This approach enables organizations to use the tool in their familiar environment with the in-depth knowledge they have about their own processes and the data that needs to be protected. No cloud extensions or open connections to a server on the internet are needed for this type of implementation, which also reduces the number of security considerations.
Protecting Modern SAP Landscapes
SAP Enterprise Threat Detection provides the support security teams need to perform real-time monitoring and analysis across their organization’s system landscape. One way it does this is with its easy-to-use dashboards and tools for managing attack detection patterns, viewing alerts, and visualizing the analysis results (see Figure 4).
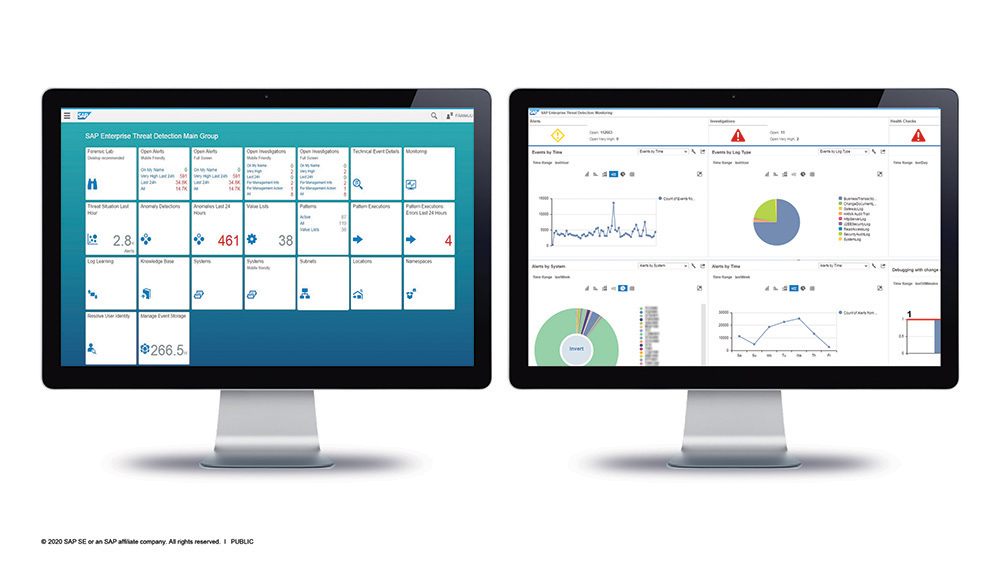
Figure 4 — SAP Enterprise Threat Detection supports security teams with easy-to-use dashboards and tools for managing attack detection patterns, viewing alerts, and visualizing the analysis results
In the next sections, we look at how the tool helps security teams meet three of the most pressing requirements for protecting modern
SAP landscapes:
- New release 2.1 features enable collaboration with established SIEM solutions and strengthen protections against data manipulation.
- Regularly shipped content enables organizations to react quickly to new threats.
- Regulatory compliance capabilities help businesses address new and updated compliance requirements to protect themselves from
costly penalties.
New Release 2.1 Features
Released in December 2019, SAP Enterprise Threat Detection 2.1 includes several new features that help organizations meet their cybersecurity needs.
With release 2.1, SAP Enterprise Threat Detection can now publish an alert event, including all the necessary details, to the widely used SIEM solution Splunk in JSON format. The user can then view the alert in Splunk and drill down into the details to determine what action to take. Splunk can now also send alerts about suspicious items back to SAP Enterprise Threat Detection. This new integration enables security teams from both the SAP and non-SAP worlds to work together in their respective environments and identify bad actors early on by sharing information across platforms.
Another new feature is the integration of SOAP Web Services into SAP Enterprise Threat Detection via the high-performance Kernel API, which was introduced with release 2.0 of the tool. When using Kernel API log files — such as the security audit log, the read access log, the system log, and now also the SOAP Web Services log — it is no longer necessary to write the log information to a persistence layer. All information can be routed via the Kernel API directly into SAP Enterprise Threat Detection, which protects it from external manipulation.
Regularly Shipped Content
Content for SAP Enterprise Threat Detection is shipped on a regular basis to help organizations quickly react to new threats. Similar to the well-known SAP patch day, which is every second Tuesday of the month, to support security teams in the use of SAP Enterprise Threat Detection, SAP delivers ready-to-go, easy-to-deploy content packages every other month that contain predefined attack detection patterns, new log learnings, and value lists for whitelists and blacklists to help reduce the overall false positive rate.
To keep customers up to date, SAP ships these content packages independent from the SAP Enterprise Threat Detection product release, so they can be delivered more frequently than the product releases.
Regulatory Compliance Features
Automated monitoring of SAP log files is a must for fulfilling new and updated compliance requirements, such as reporting security breaches to mitigate or eliminate audit-relevant risks. Using the information stored in various log files, security teams can identify potential issues and auditors can determine an organization’s overall compliance.
To help protect organizations from costly penalties, SAP Enterprise Threat Detection continuously checks all log files for compliance and completeness of security measures, allowing companies to reach a higher level of security and compliance. In addition, these continuous checks enable security teams to respond to compliance validation anomalies in real time, and to verify for auditors that they responded immediately. Specific audit patterns can also be used to meet an auditor’s requirements.
Looking Ahead
Based on the current cybercrime climate, SAP strongly recommends that its customers use SAP Enterprise Threat Detection in addition to standard perimeter security measures to detect and respond to cyberattacks and bring their organization to a higher security level. The future goal of SAP Enterprise Threat Detection is to take security even further by providing threat intelligence through supervised and unsupervised machine learning for advanced persistent threat detection, better alert qualification, and predictive threat notification.
To enable SAP customers to evaluate the tool, SAP is offering a one-day workshop, free of charge, with an SAP security consultant. During the workshop, SAP customers can connect one of their own SAP ERP or SAP S/4HANA systems to SAP Enterprise Threat Detection via SAP Cloud Appliance Library, with no additional hardware or software installation required. Through this workshop, SAP customers can get a guided tour of the tool’s features and functionality and gain a solid understanding of how to best meet the security needs of their organization.
Learn more at https://community.sap.com/topics/enterprise-threat-detection.

Martin Müller (mart.mueller@sap.com) obtained an engineering degree from HFT Stuttgart, and went on to hold various positions in application development and product management in Germany and abroad. He joined SAP in July 1998 and worked in SAP Business Information Warehouse development until June 2000. Martin has been responsible for presales and program management for SAP’s various security products for more than 15 years, focusing on cybersecurity for the past six.

Arndt Lingscheid (a.lingscheid@sap.com) studied mechanical engineering at the Rheinische Fachhochschule in Cologne. He then worked in Germany and abroad in the areas of SAP NetWeaver Basis, ABAP application development, and ABAP product development. Beginning in 2007, Arndt served as product manager for various SAP add-on products, and then in 2013, became pre-sales and product manager for SAP security add-on products. Since September 2019, he has been Product Manager for SAP Enterprise Threat Detection.






