Innovate with Confidence
Defeating Cyber Risk with the Strong Security Capabilities of SAP HANA
Cybercrime is a persistent, growing challenge in today’s digital economy. The significant growth of data that stems from trends such as big data and the Internet of Things (IoT) means that information is becoming both more plentiful and more valuable, making cybercrime more attractive and rewarding than ever before.
This has led to some alarming statistics: Over 85% of companies reported an increase in security threats in 2016, and 78% thought risks had risen despite only half of those companies increasing their IT security budgets.1 And this is all with 62% experiencing recent control breaches, showing that security concerns are not some theoretical threat — they’re a real issue for companies of all shapes and sizes. Wherever you are and whatever industry you’re in, security threats are omnipresent and constantly growing.
IT organizations understand that it’s imperative that their data be safe, regardless of the hardware, data platform, architecture, programming language, or apps they use. Unfortunately, the realities of today’s economic landscape make this a difficult feat to achieve. The growing use of personally identifiable information (PII) for advanced analytics opens a new dimension for data misuse. Trends such as cloud computing and IoT lead to significantly more data touchpoints, and with an expected 21 billion new connected devices and 521,000 PB of data storage capacity to be shipped by 2020, data is vulnerable from myriad angles. Taken together, these factors have the potential to put the credibility of an entire organization at risk with a single data leak. Consequently, security needs to pervade all systems and processes to enable digital transformation.
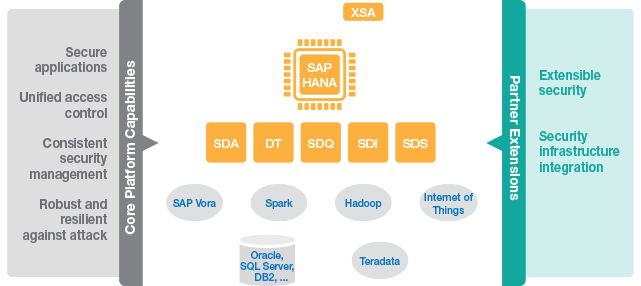
To run simple or live in the digital economy, you must run secure — or you won’t be running for very long. With the SAP HANA platform, SAP provides organizations with a database that has security built into its core (see Figure 1), and one that can be complemented by a variety of specialized security and governance solutions, such as SAP Enterprise Threat Detection, SAP Identity Management, and SAP Access Control. Let’s look at how SAP HANA can help you avoid cyber threats and instead provide a secure digital platform that enables innovation throughout the organization.
Thorough Data Security
In SAP HANA, your data is safe. A comprehensive role and privilege framework, together with granular controls and data masking, ensure that only authorized users have access to it. Cutting-edge user and identity management technologies are paired with configurable authentication and single sign-on options to allow persona- and role-specific access permissions.
These features are secure, easy to use, and flexible to manage and adapt. Backup encryption and comprehensive data-at-rest encryption provide another layer of data protection, while data in motion is secured with TLS/SSL — all of which use SAP’s FIPS 140-2 certified encryption library.
Secure Application Innovation
SAP HANA also provides a secure platform for developing and running your applications. SAP HANA extended application services come with a full-featured application server, a web server, and an integrated development environment (IDE).
By using SAP Web IDE for SAP HANA, developers can leverage comprehensive security frameworks to build secure and robust applications for numerous scenarios. The default multi-container database mode of SAP HANA enables strict application isolation and makes it easy to implement advanced segregation of duties (SoD) scenarios by separating tenant and system databases.
Comprehensive Availability and Reliability
Using SAP HANA helps ensure a secure and reliable data center. As an ACID-compliant database, SAP HANA uses advanced logging, backup, replication, and high availability/disaster recovery (HA/DR) mechanisms to prevent data loss in case of disaster. All these mechanisms are highly customizable according to your recovery point and time objectives.
For system upgrades, the capture and replay tool enables automated regression tests on captured production workloads, and the zero downtime maintenance concept maintains system availability when applying patches.
Simple Security Monitoring
SAP HANA provides you with the insight and monitoring capabilities you need to know your data is secure. SAP HANA cockpit, the central tool for SAP HANA administration and monitoring, comes with a rich feature set for managing data security within the platform. Dedicated services such as SAP EarlyWatch Check and detailed guides provide best practices and checklists for managing and monitoring the security configuration of your system.
With its innovative approach to securely integrating other data sources, SAP HANA can act as a hub for unified data processing. This provides a single point of access to all data and supports consistent security policies no matter where the data physically resides.
Learn More
SAP has unrivaled expertise in developing and managing secure solutions for critical business systems and processes across dozens of industries, and with SAP HANA, it leverages this expertise to provide companies with a safe way to obtain the competitive advantage needed to innovate quickly. By implementing SAP HANA as their platform for digital growth, organizations can achieve comprehensive access control, secure application development, and more. And they can stay ahead of cyberattacks by taking advantage of the latest security innovations. To learn more, visit https://hana.sap.com/security.
1 KuppingerCole Meta-Research 2016 study, commissioned by SAP. [back]







