Mining of important security-related logs has always been a challenge for most enterprises in terms of how to gain appropriate security intelligence from collected data sets in order to forestall malicious attacks from within and outside an enterprise. Kehinde Eseyin shows how to set up the SAP Enterprise Threat Detection system landscape to facilitate log collection and consequent analysis.
Key Concept
In view of the increasingly complex computer-driven business processing environment, it is expedient to have tools and resources in place to detect, analyze, and respond to cyber and related security threats. SAP Enterprise Threat Detection (SAP ETD) is based on the SAP HANA database. It allows you to perform real-time assessment and evaluation of security threats in your IT landscapes by leveraging SAP and non-SAP log data. Products such as SAP ETD are designed to provide the desired surveillance for enterprise IT infrastructures and a certain level of assurance that you can detect vulnerabilities before the risks are realized.
SAP Enterprise Threat Detection (SAP ETD) brings insight into the analysis of different logs, including business transaction, change document, SAP Gateway, http server, read access, security audit, system, and user change logs. It is designed to bring knowledge about attack patterns into an executable format so that attacks can be detected automatically. This product is useful for real-time security monitoring and ad hoc analysis for forensic investigation and compliance processes. It leverages the capability of SAP HANA and SAP Event Stream Processor (SAP ESP) for analysis of different types of logs in both SAP systems and non-SAP systems.
In this article, I discuss how to configure an SAP ETD system and set up the SAP NetWeaver ABAP system as a log provider for enhanced log mining, threat detection, improved system security, and forensic investigation. I cover the following sub-topics:
- Understanding the technical landscape of SAP ETD
- Deploying the SAP HANA delivery unit for SAP ETD
- Installing licensing of SAP ESP
- Maintaining the workspace repository
- Importing projects in SAP ESP
- Maintaining SAP ETD background jobs
- Maintaining roles for the SAP ETD launch pad
- Maintaining SAP HANA Open Database Connectivity (ODBC)
- Maintaining environment variables
- Configuring the SAP ESP cluster workspace
- Parameterizing SAP ETD projects in SAP ESP
- Restarting the cluster
- Installing the log learning and SAP Gateway log adapters
- Compiling projects
- Deploying projects to the cluster workspace
- Starting the wsp service
- Configuring the ABAP system as a log provider
- Setting up the connection to SAP ETD
- Testing the connection
- Sending log data to SAP ETD
- Accessing the SAP ETD launch pad
Understanding the Technical Landscape of SAP ETD
The system landscape of SAP ETD is made up of the three components:
- The log providers
- SAP ESP
- SAP HANA database
Log providers: These systems, which can be SAP NetWeaver application servers or SAP HANA or non-SAP systems, provide the logs that drive threat analysis and alerts in the SAP ETD system.
SAP ESP: SAP ESP provides a tool for capturing, analyzing, and acting on streaming data. SAP ETD projects are typically imported into the SAP ESP so that logs from SAP and non-SAP systems are processed and normalized into events before they are sent to the SAP HANA database for further enhanced analytics.
SAP HANA database: The SAP ETD delivery unit is deployed on the SAP HANA database and contains the main application codes that drive this product. The SAP HANA database is the repository for storing events, attack detection patterns, and context about the users and systems in the landscape that are used to trigger alerts. A browser-based (front-end) application is used to browse events, configure patterns, manage alerts, and conduct investigations in the monitored network.
Technically, setting up a landscape for SAP ETD can be broadly divided into the following steps:
- Deploy the delivery unit on the SAP HANA database
- Import and configure SAP ETD projects in SAP ESP
- Configure systems as log providers
When you are installing the components of the SAP HANA landscape, it is important to review SAP Note 2137018 (Compatibility information for SAP Enterprise Threat Detection support packages and SAP HANA revisions), to ascertain the compatibility of the SAP ETD version with a particular SAP ESP version and, of course, the dependent SAP HANA version. Table 1 is an excerpt of this SAP Note. It explains the version dependencies between the SAP ETD delivery unit, SAP HANA, and SAP ESP.
ETD Support Package Stack and patch level |
Compatible to SAP HANA revision |
Compatible to ESP version |
| SPS 02 PL 1 |
95 and above |
5.1 SP09* |
| SPS 02 PL 0 |
95 and above |
5.1 SP09* |
| SPS 01 PL 1 |
85, 95 |
5.1 SP08* |
| SPS 01 PL 0 |
85 |
5.1 SP08* |
| SPS 00 PL 0 |
85 |
5.1 SP08* |
Table 1
Version compatibility matrix for SAP ETD delivery unit, SAP HANA, and SAP ESP
Deploying the SAP HANA Delivery Unit for SAP ETD
First, you need to download the delivery unit after extracting it from the Service Marketplace and place it in a directory that is accessible from SAP HANA studio. Launch SAP HANA studio and navigate to the SAP HANA Modeler perspective as shown in Figure 1.

Figure 1
The initial screen of the SAP HANA modeler
Click the Import quick link to open the screen shown in Figure 2.

Figure 2
Dialog box to import SAP HANA content
Navigate to the SAP HANA Content folder. Click Delivery Unit and the Next button. In the screen that displays (Figure 3) choose the SAP HANA system into which you want to import the delivery unit. In my example it is EDT (SYSTEM).

Figure 3
Select the system relevant for the import process
Click the Next button, and in the screen that opens (Figure 4), choose the Client radio button.

Figure 4
Select the client as the source of the delivery unit to be imported
Click the Browse… button to navigate and select the directory where you unzipped the downloaded SAP ETD delivery unit as shown in Figure 5.

Figure 5
Define the directory for the delivery unit to be imported
Click the Finish button and you get a status message Completed Successfully, confirming the import.
Installing Licensing of SAP ESP
The installation guide for SAP ESP is here: https://help.sap.com/saphelp_esp_51sp09_win/helpdata/en/e7/74b6ee6f0f1014a524927f7f8f330c/frameset.htm
If you encounter any licensing issues that prevent an SAP ESP project from working correctly review this document: https://wiki.scn.sap.com/wiki/display/SYBESP/ESP+Licensing+Troubleshooting
Maintaining the Workspace Repository
A workspace can be defined as a local directory that can be mapped to all or to a section of a package hierarchy in the SAP HANA repository. Before you can start work on the development of an application, you need to set up a workspace where you store checked-out copies of your SAP ETD application’s source code files.
To create a new workspace in the SAP HANA studio, perform the following steps:
Navigate to SAP HANA studio and follow menu path Windows > Show View. Then click the Other menu option (not shown). The system now opens the screen shown in Figure 6. Expand the SAP HANA folder (Figure 7).

Figure 6
Additional Show View menu options
Click Repositories and then click the OK button.

Figure 7
Repositories node in the SAP HANA folder
The system displays the screen shown in Figure 8.
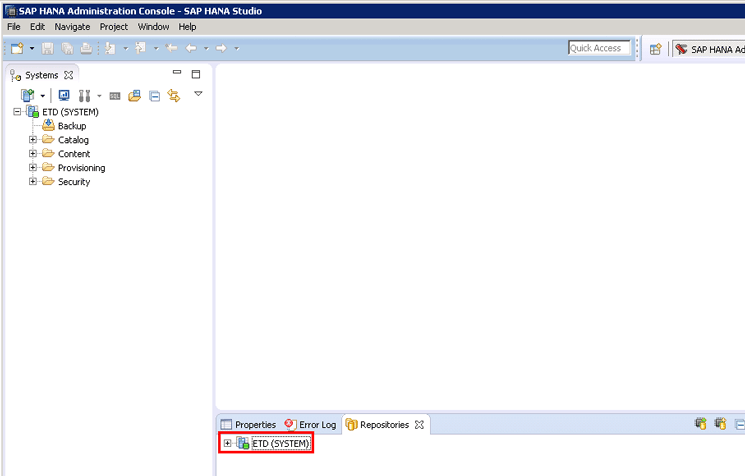
Figure 8
The Repositories pane in SAP HANA studio
Right-click the system ID node named ETD (SYSTEM) to create a repository workspace. In the initial screen that opens (not shown), click the Create Repository Workspace button. This action displays the screen shown in Figure 9.

Figure 9
Define the location for the new repository workspace
I adopt the suggested workspace location (i.e., I choose the directory suggested by the system), which is a directory of the logged-on user. It is good practice to ensure that only the owner of the data can access the data stored in a workspace. Therefore, a workspace should be created in the owner’s home directory. This data is stored at the operating system level, so typical file share guidelines and permissions apply.
Click the Finish button. In the next screen (Figure 10), you see the EDT (SYSTEM) (Default) node. Expand it and right-click the esp sub-node to display the menu shown in Figure 11.

Figure 10
Expanded node of the new repository workspace
Click the Check Out option.

Figure 11
Menu path to check out repository
In the path at the top of the screen that opens (Figure 12), navigate to the directory of the repository workspace that you defined in Figure 9 to confirm the checked-out files are physically resident in the directory.

Figure 12
Directory where checked-out files are stored
Importing Projects in SAP ESP
Following the export of the SAP ETD-related project files to the operating system file system, you now need to import the files into SAP ESP. To perform this operation, launch SAP ESP Studio from the All Programs menu in your computer. The initial screen of the ESP Studio then appears (Figure 13).

Figure 13
The initial screen of the SAP ESP studio – SAP ESP Authoring perspective
While in the SAP ESP Authoring perspective, right-click in the left pane under the Project Explorer work area, and in the menu that appears, click the Import… option (Figure 14).

Figure 14
Path to initiate the import of the SAP ETD project into the SAP ESP operation
In the pop-up screen that appears (Figure 15), navigate to the General folder and expand it.

Figure 15
Options for import source in the General folder
Click the Existing Projects into Workspace option and then click the Next button. In the screen that opens, choose the Select archive file radio button as shown in Figure 16.

Figure 16
Select the archive file as the directory for the SAP ETD project
Click the Browse… button to search for the files (transfer_log and transfer_master_data) in the workspace directory. Your screen looks similar to the one shown in Figure 17 for the import of transfer_log project.

Figure 17
Imported SAP ETD Project – transfer_log
Click the Finish button. Figure 18 displays with the imported project in the Project Explorer window.

Figure 18
Transfer_log project successfully imported into SAP ESP
Follow the same procedure to import the transfer_master_data file.
Maintaining SAP ETD Background Jobs
SAP ETD uses a number of background jobs to collect logs and drive the display of alerts and reports on its dashboard. As a prerequisite, the user setting up the background job must have the role sap.hana.xs.admin.roles::JobAdministrator assigned. Additionally, the job scheduler must be enabled, which can be done via the SAP HANA Extended Services (XS) dashboard or by maintaining the applicable SAP HANA configuration file (i.e., parameter scheduler in the xsengine shown in Figure 19).

Figure 19
Status definition for the job scheduler in the configuration file
The SAP HANA XS Job Dashboard provides a centralized interface for monitoring and maintaining job schedules. You can also use the Scheduler Enabled button in the XS Job Dashboard to enable schedules for all XS jobs globally.
To access the XS Job Dashboard, use the URL https://<WebServerHost>:80<SAPHANAinstance>/sap/hana/xs/admin/jobs/. In the screen that displays (not shown) provide a user name and password to go to the screen shown in Figure 20.

Figure 20
The initial screen of the SAP HANA XS Job Dashboard
Note that the message highlighted in blue notifies you that the scheduler is disabled and no schedule will run. Change the Scheduler Enabled toggle to YES. The screen shown in Figure 21 appears with a dialog box.

Figure 21
Dialog box confirming the activation of the job scheduler
Click the OK button. Figure 22 displays.
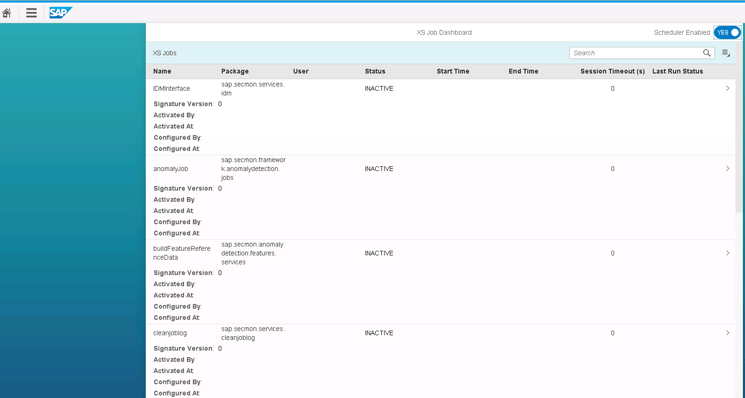
Figure 22
Background jobs supported by SAP ETD
The background jobs supported by SAP ETD have the prefix sap.secmon. They are listed below with a concise description of their different functions:
- sap.secmon.anomalydetection.features.services::buildFeatureReferenceData – Computes the reference data for outlier detection.
- sap.secmon.framework.anomalydetection.jobs::anomalyJob – Computes the aggregate and deviation on the basis of data from the last 12 weeks for anomaly detection.
- sap.secmon.framework.pattern.jobs::patternExecutionResultJob – Deletes all pattern execution results older than seven days.
- sap.secmon.framework.pattern.jobs::patternjob – Starts patterns.
- sap.secmon.services.healthcheck ::healthcheck – Checks for the arrival of logs and pings from log provider systems. The health checks job also checks for specific events from the SAP ETD infrastructure, such as pings from SAP Event Stream Processor and successful execution of the partitioning and pseudonymization jobs.
- sap.secmon.services.idm::IDMInterface – Checks the transfer tables for new user context information from SAP Identity Management.
- sap.secmon.services.partitioning::clearData – Deletes partitions of tables sap.secmon.db::Log.LogDetail and sap.secmon.db::Log.LogHeader in the schema SAP_SEC_MON older than the retention period with default value of 90 days.
- sap.secmon.services.partitioning::partitioning – Partitions the tables sap.secmon.db::Log.LogDetail and sap.secmon.db::Log.LogHeader in the schema SAP_SEC_MON. SAP ETD partitions these tables to keep the tables from becoming too large and to help performance.
- sap.secmon.services.pseudonymization::pseudonymization - Creates pseudonyms for users and records old pseudonyms in the pseudonym history for users.
- sap.secmon.trigger.jobs::dispatcher – Checks if an event corresponding to a trigger in a pattern definition has arrived and triggers the corresponding pattern.
- sap.secmon.trigger.jobs::thread – This is an on-demand dynamically started job allowing asynchronous pattern execution.
- sap.secmon.ui.browse.services2. jobs::rawdata – Deletes the temporary data created by the forensic lab.
To activate the job, choose a job—for example, `sap.secmon.framework.anomalydetection.jobs:anomalyJob. In the screen that displays, enter values for the user, password, and locale. Check the Active check box as shown in Figure 23.

Figure 23
Details of job - sap.secmon.framework.anomalydetection.jobs:anomalyJob
Click the Save Job button. Do the same for all the remaining jobs. Note that the frequency of the jobs is hard-coded and cannot be changed.
Maintaining Roles for the SAP ETD Launch Pad
You need to maintain SAP ETD roles by assigning a widget catalog and groups to them so that SAP ETD tiles can be displayed correctly. To perform this activity, navigate to the SAP HANA role-based cockpit via the URL <protocol>://<hostname>:<port>/sap/hana/uis/clients/role-editor/RoleEditor.html?scenario=onPremise&siteId=sap.secmon.ui.mobile.launchpad%7CETDLaunchpad.
After you provide the log-on credentials (screen not shown), the screen shown in Figure 24 opens.

Figure 24
The initial screen of the configure role-based cockpit access
In the search field, enter a value for a role. For my example, enter sap.secmon.db::EtdUser. Click the search icon  (not shown in Figure 24) to initiate the search. Figure 25 displays the search result.
(not shown in Figure 24) to initiate the search. Figure 25 displays the search result.

Figure 25
Output of the role search condition
Click the role to open the screen shown in Figure 26.

Figure 26
The initial screen for catalogs and groups maintenance for a role
Highlight the Catalogs icon and click the + icon. In the screen that opens, select the SAP Enterprise Threat Detection Widgets check box as shown in Figure 27.

Figure 27
Select the catqalog to be assigned to a role
After you click the OK button, the screen shown in Figure 28 displays the assigned catalog.

Figure 28
Assigned catalog to the role
Click the Groups icon to open the initial screen for groups maintenance against a role. Click the + sign under the Groups icon. In the screen that displays (not shown), select the SAP Enterprise Threat Detection Main Group check box. Click the OK button. Figure 29 displays the assigned group.

Figure 29
Assigned groups to SAP ETD role
Maintaining SAP HANA Open Database Connectivity (ODBC)
ODBC is a standard programming language middleware application programming interface (API) for accessing database systems. Like most database systems, SAP HANA provides a driver for connecting applications to the database with the ODBC API. ODBC facilitates communication between the SAP ESP and the SAP HANA database. The ODBC driver is typically installed as part of the SAP HANA client installation. Create a data source by running the odbcad32.exe tool. This activity is done on the client computer where SAP HANA studio is installed. ODBC is supported on any operating system, and the SAP HANA database is supported on only Linux (SUSE or Red Hat) systems.
You can run this via the command line or via the Start of the navigation path Control Panel > Administrative Tools > Data Sources (ODBC). The screen shown in Figure 30 opens. Click the System DSN tab.

Figure 30
The initial screen for ODBC data source definition
In the screen that opens (Figure 31), select the ODBC driver against which you want to create a data source (e.g., HDBODBC) and click the Finish button.

Figure 31
Installed ODBC drivers
In the next screen (Figure 32), enter values for the Data Source Name, Description, and Server:Port.

Figure 32
Attribute definition for ODBC data source
Click the Connect button. In the screen shown in Figure 33, enter values for the User name and Password.

Figure 33
User and password definition for the data source maintenance
After you click the OK button, you see a screen (not shown) with a status message for ODBC data source maintenance (in this case Connect successful). After you click the OK button to complete the maintenance of the ODBC data source, the screen shown in Figure 34 opens.
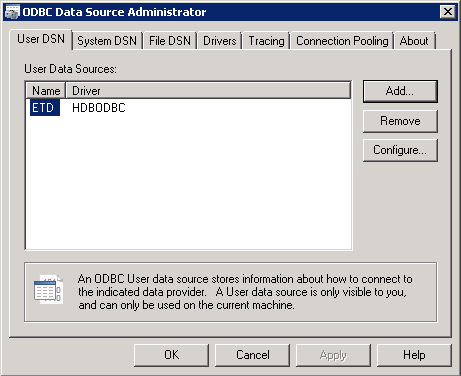
Figure 34
Newly created ODBC data source in the ODBC data source administrator
Click the Cancel button to exit the ODBC data source administration screen.
Maintaining Environment Variables
Irrespective of the operating system on which the SAP ESP system is installed, you need to maintain the following environment variables:
- HDBCLI
- ESP_HOSTNAME
- LANG
- PATH
- JAVA_HOME
For a Windows operating system, maintain the environment variables as shown in Figure 35. You access the interface to maintain environment variables via menu path System Properties > Advanced > Environment Variables.

Figure 35
Environment variables maintenance in Windows
Configuring the SAP ESP Cluster Workspace
The cluster workspace is the run-time environment in which the SAP ETD projects are executed. To create a cluster workspace, launch the SAP ESP Studio as shown in Figure 36.

Figure 36
The initial screen of the SAP ESP Studio
Follow menu path Window > Open Perspective > SAP ESP Run-Test, to open the next screen (Figure 37).

Figure 37
SAP ESP Run-Test perspective
Click the new server URL icon (circled in red in Figure 37). In the next screen, enter values for the hostname and port of the ESP Server as shown in Figure 38.

Figure 38
Connection details definition for server connection
Click OK. Figure 39 displays the newly created server connections.
Figure 39
Newly created server connection in SAP ESP
Right-click the newly created server node, and in the drop-down menu, click the Connect Server option. Figure 40 appears with the ESP workspace name default. Use this default name.

Figure 40
Server successfully connected
Follow menu path Window > Show View > Other … to open the screen shown in Figure 41.

Figure 41
Additional Show View options in SAP ESP Studio
Expand the SAP Event Stream Processor folder, and then select Data Services as shown in Figure 42.
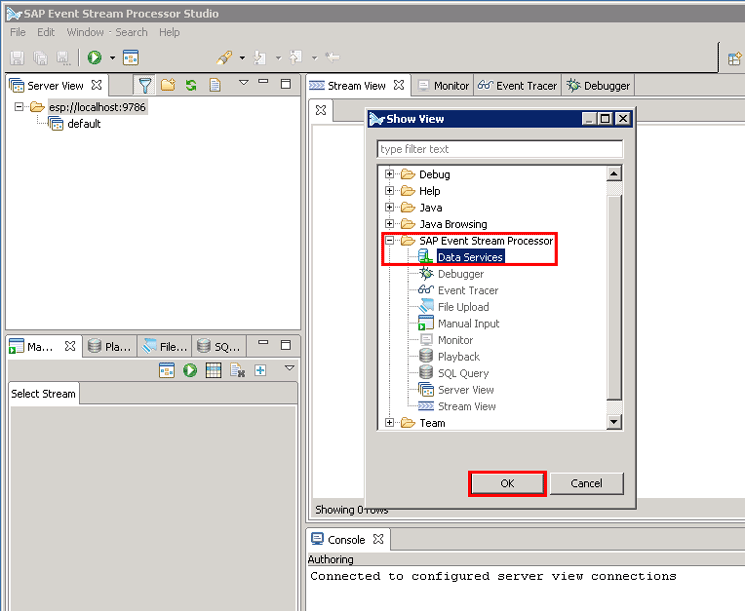
Figure 42
Menu path to select the Data Services sub-node
Click the OK button. Figure 43 displays with the newly created Data Services subnode.

Figure 43
Newly created data services
Right-click the Data Services node you just created to see the maintenance options (Figure 44).

Figure 44
Maintenance options for data services
After you click the Add ODBC Service option, the screen shown in Figure 45 opens.

Figure 45
Newly added ODBC service to the data service
Right-click the newly added ODBC service to give it to a meaningful name. Click the Rename Service option that appears as a drop down.
In the screen that displays, enter a meaningful name for the ODBC service, in this case ETD. Click the OK button and Figure 46 displays the name change of the data service.

Figure 46
Renamed ODBC service
Now, with the ODBC service renamed, you maintain the connection attributes of the service.
Follow menu path Window > Show View > Other… >. Figure 47 opens.

Figure 47
Show View additional options
Open the General folder and choose the Properties drop-down option. Click the OK button to go to the Properties screen (Figure 48). Maintain the values as shown.

Figure 48
Properties definition for ODBC service
Click anywhere outside the screen to save your entries.
Parameterizing SAP ETD Projects in SAP ESP
The projects imported into SAP ESP come with default parameter values that need to be maintained to align their values with the system environment and meet business requirements. These parameters include:
- ODBCConnectionName: This defines the name of the data service for the ODBC connection to the SAP HANA system in which the logs are to be stored.
- EMailNotificationOn: This is used to disable or activate email notification.
- toAddress: The recipient email address to notify when the host SAP HANA is not available.
- cctoAddress: An additional email address to notify when the host SAP HANA is not available.
- fromAddress: The sender email address of the notification message.
- ESPInstanceId: An identifier for SAP ESP Server which appears in the message subject matter.
- smtpHost: The host name of the email server to send the notification message.
- smtpPort: The port number of the email server to send the notification message.
- TimeSpanBetweenEmailsInSecs: The number of seconds between email messages from SAP ESP with a default value of 600 seconds.
- PseudonymizatioOn: This is used to determines whether user IDs are pseudonymized or not.
- ProjectName: This defines the name of the project in the email notification to determine which project triggered the notification.
These parameters have default values. You should review and revise the values as desired. For the purpose of this article, I only maintain the ODBCConnectionName parameter. To do this, navigate back to the SAP ESP Authoring perspective and open up the transfer_log project. Navigate to the node transfer_log.ccr and double-click it. The screen shown in Figure 49 opens.

Figure 49
Project configuration file for transfer_log project
Navigate to the Parameters tab. Click ODBCConnectionName under All Parameters as shown in Figure 50.
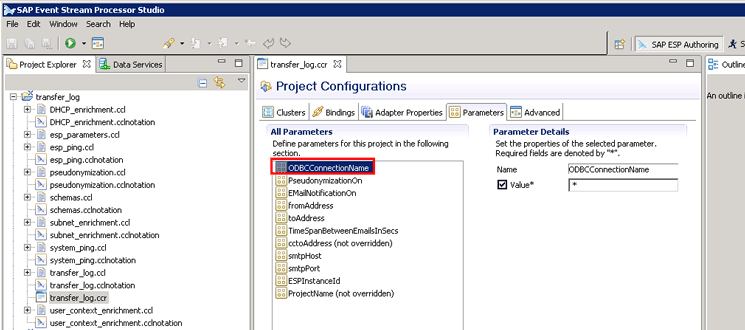
Figure 50
The initial screen for the maintenance of ODBCConnectionName property
Replace the default value by entering a value for the ODBCConnectionName property in the field circled in Figure 51. In my example I use etd that I created initially.

Figure 51
Custom value definition for ODBCConnectionName parameter
Click the save icon circled in Figure 51.
Follow these steps to maintain the parameter (ODBCConnectionName) for the transfer_master_data project. Navigate to the transfer_master_data project and then to transfer_master_data.ccr node in this case as shown Figure 52.
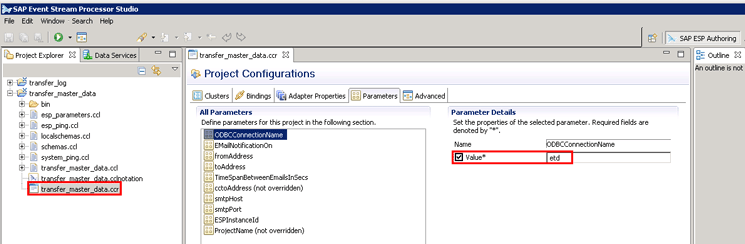
Figure 52
Maintain the ODBCCConnectionName parameter for transfer_master_data project
Restarting the Cluster
Open the run test perspective to restart the cluster by navigating to Windows > Open Perspective > SAP ESP Run-Test. In the screen that appears, right-click the cluster node as shown in Figure 53.
Figure 53
Menu options for disconnect and stop local server
Click the Disconnect and Stop Local Server option. The screen shown in Figure 54 opens.
Figure 54
Stopped cluster node
To start the cluster back, right-click the cluster node as shown in Figure 55.

Figure 55
Menu option to start the server
After you click the Connect Server option, the screen shown in Figure 56 opens.

Figure 56
Started cluster node
Installing the Log Learning and Gateway Log Adapters
The installation of the log learning and Gateway log adapters involves copying and replacing the content of specific folders (or files) in the SAP ESP installation directory with the content of the SAP ETD project that you checked out. Before you perform the copy and paste activities, it is good practice to back up the folders (or files) just in case you need to revert to a particular point.
Table 2 shows the applicable folder (or files), what is copied, and to where.
| File/Folder |
Source |
Target |
| gwlogadapter.cnxml |
<File location>/esp/esp_projects/adapter/common |
<Installation directory of SAP ESP>/ESP-5_1/lib/adapters |
| rtparseradpater.cnxml |
<File location>/esp/esp_projects/adapter/common |
<Installation directory of SAP ESP>/ESP-5_1/lib/adapters |
etd_gwlog-1.2.1.jar
|
<File location>/esp/esp_projects/adapter/<adapter_name>
|
<Installation directory of SAP ESP>/ESP-5_1/adapters/framework/libj |
etd_runtimeparser-1.2.1.jar
|
<File location>/esp/esp_projects/adapter/<adapter_name> |
<Installation directory of SAP ESP>/ESP-5_1/adapters/framework/libj |
| Gwlogadapter |
<File location>/esp/esp_projects/adapter/<adapter_name> |
<Installation directory of SAP ESP>/ESP-5_1/adapters/framework/instances |
| Rtparseradapter |
<File location>/esp/esp_projects/adapter/<adapter_name> |
<Installation directory of SAP ESP>/ESP-5_1/adapters/framework/instances |
| modulesdefine.xml |
<File location>/esp/esp_projects/adapter/common |
<Installation directory of SAP ESP>/ESP-5_1/adapters/framework/config |
parametersdefine.xsd
|
<File location>/esp/esp_projects/adapter/common
|
<Installation directory of SAP ESP>/ESP-5_1/adapters/framework/config
|
Table 2
Maintenance of log learning and Gateway log adapters
Furthermore, you need to maintain the adapter_config.xml file appropriately. The file is located here:
- <Installation directory of SAP ESP>/ESP-5_1/adapters/framework/instances/rtparseradapter
- <Installation directory of SAP ESP>/ESP-5_1/adapters/framework/instances/gwlogadapter
More importantly, at the minimum, the hostname, user name, and password should be maintained in the file. The file should look like Figure 57.

Figure 57
Maintained adapter_config.xml configuration file
Restart the SAP ESP cluster after maintaining the files.
Compiling Projects
Follow the instructions below to compile the SAP ETD projects. You need to compile the SAP ETD projects to transform them into executable programs so that you can ensure they run without any errors.
Open the SAP ESP authoring perspective. Right-click a project, for example, transfer_log as shown in Figure 58.

Figure 58
Menu path to compile projects in SAP ESP
Follow menu path SAP ESP > Compile ESP Project. As expected, the projects should compile successfully. If errors are encountered during the compilation run, they are displayed on the screen. Repeat the same process to compile project - transfer_master_data.
Deploying Projects to the Cluster Workspace
Following successful compilation of the (transfer_log and transfer_master_data), you need to deploy the projects to their run-time environments to enable the projects for streaming data. Follow the procedure below to deploy the projects to the cluster workspace.
Open the SAP ESP authoring perspective. Right-click a project, for example, transfer_log. Follow menu path SAP ESP > Run > Run ESP Projects in workspace esp://localhost:9786/default. Figure 59 displays a log of the successful deployment run.

Figure 59
Successful deployment of the SAP ETD project in SAP ESP
If there are errors, the compilation does not run successfully and you see the error displayed on the screen. Repeat the steps above for transfer_master_data project.
Starting the wsp Service
The wsp.bat file in %ESP_HOME%wsp is used to start the Jetty (Java Servlet container) server (which initializes both Simple Object Access Protocol [SOAP] and Representational State Transfer [REST] ports). It is important that the JAVA_HOME environment variable be properly maintained in order to successfully start this service. Figure 60 shows how the service can be started from the command prompt in the Windows operating system. Navigate to the directory where the ESP application is installed and run the command wsp.

Figure 60
Starting a wsp service via a command prompt
Configuring the ABAP System as a Log Provider
SAP ETD can use both SAP and non-SAP systems as log providers. In this article, I discuss the configuration of the SAP ABAP system as a log provider. Before configuring the SAP ABAP system as the log provider, you must ensure that the relevant package is installed as detailed in SAP Note 1998675 (Unified ABAP Interface for SAP Enterprise Threat Detection).
The following standard logs are monitored by SAP ETD:
- Business Transaction Log: This is the ABAP statistics records, which contains technical information such as response time, transaction code, or central processing unit (CPU) time.
- Change Document Log: Records changes to business objects. You need to implement SAP Note 2128378 in order to monitor the change document log. The documents to monitor can be selected by maintaining the table view SECM_CDLOG_FILT.
- Gateway Log: Monitors the activities of the Gateway.
- HTTP Server Log: Logs HTTP requests to or from SAP NetWeaver AS for ABAP.
- Read Access Log: Logs read access to data that has been categorized as sensitive by legal requirements, by external or internal organizational policies.
- Security Audit Log: Logs security-related events on SAP NetWeaver AS for ABAP.
- System Log: Logs all system errors, warnings, user locks due to failed logon attempts from known users, and process messages.
- User Change Log: Logs all changes made directly to the authorizations of users and user master records.
In Maintain Table Views transaction (transaction code SM30), you define which logs you want to collect by maintaining table SECM_LOGS as shown in Figure 61.

Figure 61
The initial screen for the maintenance of table SECM_LOGS
Click the Maintain button and the message displays in a dialog box (Figure 62).
Figure 62
Dialog box confirming the cross-client attribute of table SECM_LOGS
Click the green checkmark and Figure 63 opens.

Figure 63
The initial screen to configure logs to be collected
If the table is empty as above, click the initialize entries, if empty icon (circled in Figure 63) to add entries with default settings and the screen shown in Figure 64 opens.

Figure 64
Default settings for log type, Security Monitor (SECM) log class, and logging status

Figure 65
Maintain table SECM_LOGS in change mode
The entries in this table are the standard logs types and log classes delivered by SAP for the SAP ABAP stack. You can create your own log type and implement log classes if you intend to monitor additional logs. For the log entries that you intend to monitor, you need to set the Log Active to true. For my example, I maintain all logs to true by changing the toggle to true as shown in the Figure 66.

Figure 66
Set the logs to true
After you click the save icon, the screen shown in Figure 67 opens.

Figure 67
Maintained log active status in the SECM logs table
Setting Up the Connection to SAP ETD
The connection between SAP NetWeaver Application Server (SAP NetWeaver AS) ABAP and SAP ESP needs to be established to establish seamless data flow of logging data when reports SECM_LOG_2_ESP and SECM_MASTER_DATA_2_ESP are executed. These reports trigger data collection from the log provider system to SAP ESP for processing. SAP ESP then consequently sends this data to SAP HANA to be consumed by the SAP ETD application.
However, you first need to set up the connection settings by providing the attributes of the SAP ESP server and the related project’s details and settings. You need to create a configuration for the transfer_log project and another one for the transfer_master_data project. This can be done via program SECM_CONFIGURATION, which you can access with transaction code SE38. That take you to the initial screen, where you check the Add or Edit Configuration radio button. Then maintain the attributes as shown in Figure 68. For the purpose of this article, I defined values for the configuration name, SAP ETD Version, SAP ESP webserver/REST configuration and SAP ESP data.
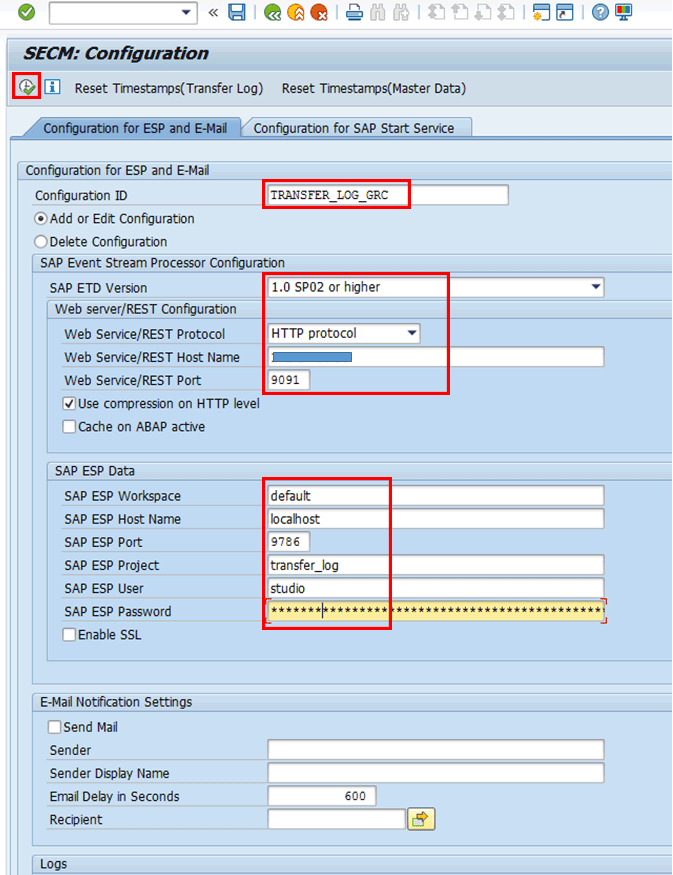
Figure 68
Attributes definition for the configuration ID of the transfer_data project
After you click the execute icon circled in Figure 68, you get a status message confirming the successful configuration.
Set up another configuration in like manner with the same attributes as in Figure 68, but with a different configuration name. Set the SAP ESP Project attribute to transfer_master_data to cater for the transfer_master_data project (Figure 69).
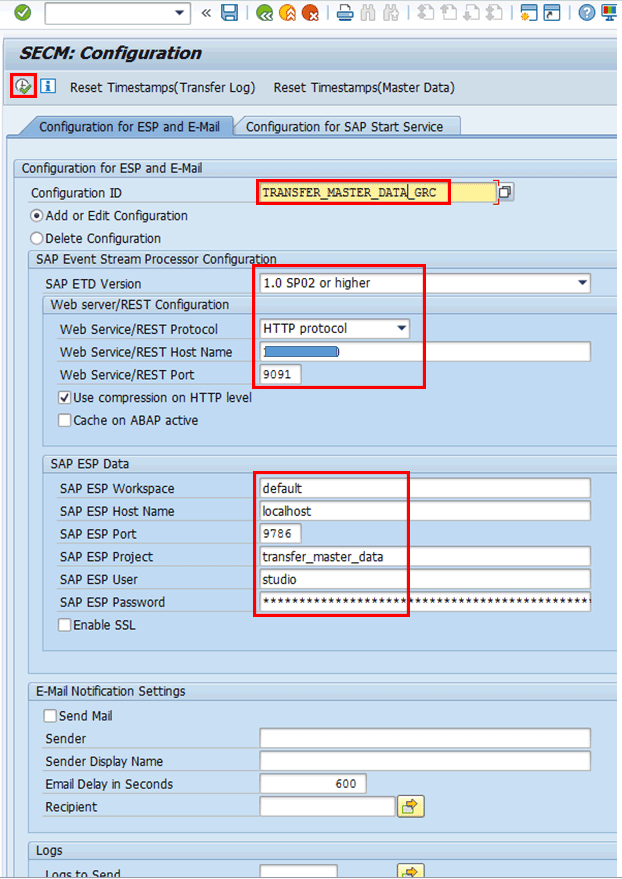
Figure 69
Attribute definition for the configuration of transfer_master_data project
After you click the execute icon, you receive a confirmation status message saying Done for: TRANSFER_MASTER_DATA_GRC.
Testing the Connection
After you define the connection attributes, it is important to ping the system based on the connection attributes defined in the different configurations. This is to ascertain that the connection can be successfully established. To do this, execute program SECM_LOG_2_ESP via transaction code SE38. Choose the configuration you created for the transfer_log project in the Configuration ID field. Choose the radio button Ping SAP ESP Server as shown in Figure 70. Note that the other details are auto-populated as maintained in the configuration ID.

Figure 70
The initial screen to transfer data to SAP ESP – Ping SAP ESP Server option
After you click the execute icon in Figure 70, you get the result of the ping test (Figure 71).

Figure 71
Confirmation of successful ping to the SAP ESP Server
Follow the same procedure to test the ping for the transfer_master_data configuration using program SECM_MASTER_DATA_2_ESP and you should see a message similar to the one in Figure 71.
Sending Log Data to SAP ETD
Now that you have established that you can successfully ping the SAP ESP server, you now initialize the data transfer. I call the programs SECM_LOG_2_ESP and SECM_MASTER_DATA_2_ESP using the configuration IDs I created for transfer_log and transfer_master_data, respectively. However, I use the default value for options (Transfer To SAP ESP Server) as shown in Figure 72 for the transfer_log project.

Figure 72
The initial screen to transfer data to SAP ESP server
Click the execute icon. The next screen (Figure 73) displays the logs of the data pushed to the SAP ESP server.
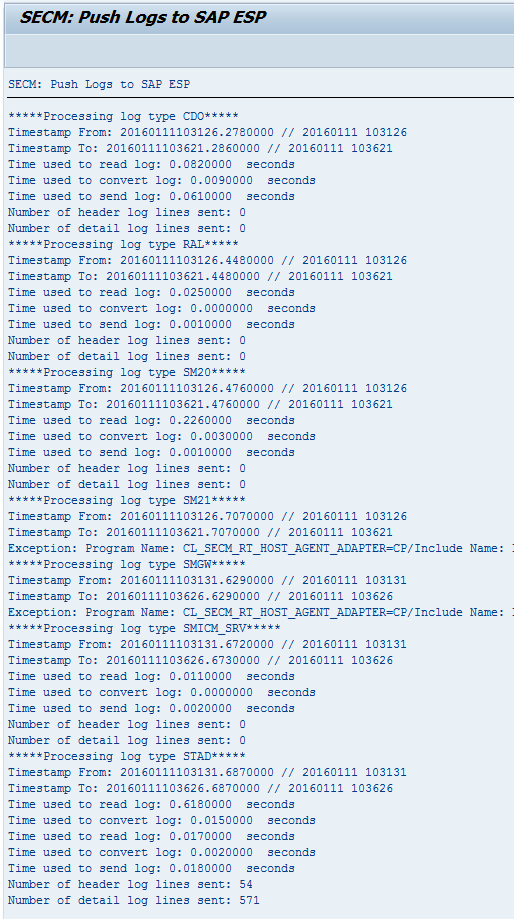
Figure 73
Log of data transferred to the SAP ESP Server
Follow the same procedure to transfer master data to the SAP ESP server using the program SECM_MASTER_DATA_2_ESP and the configuration for the transfer_master_data project as shown in Figure 74.

Figure 74
The initial screen to transfer master data to the SAP ESP Server
After you click the execute icon in Figure 74, the screen shown in Figure 75 opens.
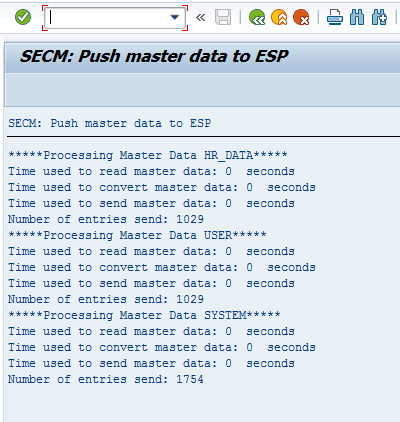
Figure 75
Log of the successful execution of program SECM_MASTER_DATA_2_ESP
Note: SAP recommends that you run program SECM_LOG_2_ESP once per minute and SECM_MASTER_DATA_2_ESP once per day.
Accessing the SAP ETD Launch Pad
Now that you have successfully configured the SAP ETD system and executed that log and master data collection job, you should have some information in the SAP ETD launch pad. The SAP ETD launch pad is based on the SAP Fiori application. The launch pad represents the interface to interact with the alerts and configuration settings of the application. The launch pad can be accessed via the link https://<SERVER>:<Port>/sap/hana/uis/clients/ushell-app/shells/fiori/FioriLaunchpad.html?sap-language=EN&siteId=sap.secmon.ui.mobile.launchpad|ETDLaunchpad (Figure 76).
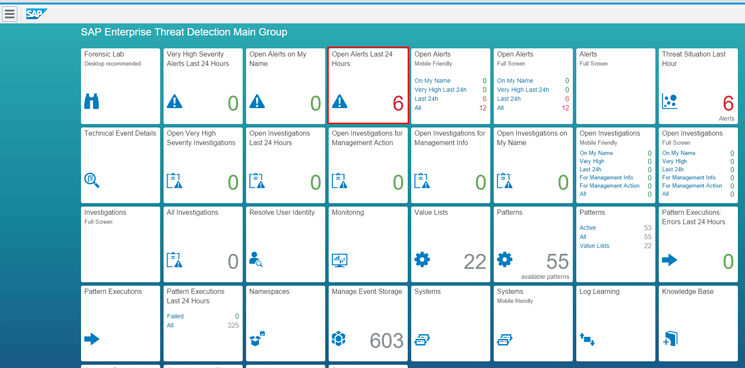
Figure 76
The initial screen of SAP ETD
For example, I click the Open Alerts Last 24 Hours tile.
Note: In a follow-on article, I explain how to apply the information in the different tiles for proper analysis of security threats as this is outside of the scope of this article. I only show how to navigate the Open Alerts Last 24 Hours tile in the remainder of this article to demonstrate the look and feel of the product.
After I click the Open Alerts Last 24 Hours tile, choose any alert from the list in the next screen (Figure 77). For example, I click Alert 8 - Security relevant configuration changes.

Figure 77
Details of Alert 8 - Security relevant configuration changes
Click the Security relevant configuration changes link in the Pattern field in Figure 76. Figure 78 displays the details of the configuration associated with the alert.

Figure 78
Attribute of the security pattern for the configuration changes
Kehinde Eseyin
Kehinde Eseyin is a security architect. He holds a bachelor’s degree in computer science. He has about 12 years of IT security, governance framework, IS risk, and compliance experience gained by working in numerous global organizations. Over the years, he has demonstrated competencies in security design, information assurance, cyber security, data privacy, threat and vulnerability management, penetration testing, business architecture, project management, IT audit, IS controls framework, and identity and access management.
You may contact the author at eseyinok@gmail.com.
If you have comments about this article or publication, or would like to submit an article idea, please contact the editor.