By Juan Perez-Etchegoyen, CTO, Onapsis
Enterprise Software is complex due to its nature and interconnectivity to business processes. On top of that, software is made by humans, which means that regardless of how much we want to avoid it, bugs will be there and not uncommonly... critical ones. This holds true for many software vendors such as Microsoft, Apple, Oracle, Intel, Adobe, VMWare...and also SAP. What all of these vendors also have in common is how they deal with the patches that solve those vulnerabilities, through what is called the “
Patch Tuesday.” Patch Tuesday happens to be the second Tuesday of every month and has now become a standard day where large software makers release the fixes for security vulnerabilities in their software. In this manner, patches are released in a coordinated way providing organizations’ IT departments the opportunity to be prepared. Even though it is impossible to know if the number of patches a vendor is releasing will be 0, 1 or 10, at least these IT teams can better expect the unexpected, knowing that the second Tuesday of every month, there's potentially going to be a bunch of things to fix across the board.
A Positive Trend
But what about the applications that support your most critical business processes and hold your crown jewels?
IT Admins have been dealing with Patch Tuesday for the last few years and getting used to the overhead of patches being implemented. But the SAP BASIS teams, who manage your SAP applications and ensure availability and uptime of applications, have been slowly adopting this patching process, because the cadence of changes within SAP applications is completely different in organizations, as compared to, for example, the ability to react and apply a patch in a windows-based host. Requesting a change management window is not a simple thing for SAP applications that run and support the most critical business processes of your organization.
But, that's been changing over the past few years, especially driven by a broader awareness of the need for cybersecurity controls around SAP applications. Additionally, even though the overall number of SAP Security Notes has been slowly decreasing over the years, due to SAP strategies to package and simplify customers' adoption of patches (for example multiple vulnerabilities fixed through the same patch), there's been an increasing number of patches addressing critical vulnerabilities (HotNews in the SAP world).
As seen in
Figure 1, the evolution of SAP Security Notes shows a decrease in the total number of patches as well as an increase on the HotNews over the past 5 years. This data does not consider the potential upcoming SAP Security Notes or HotNews in the remaining 4 months of 2020, which could change the trend too.
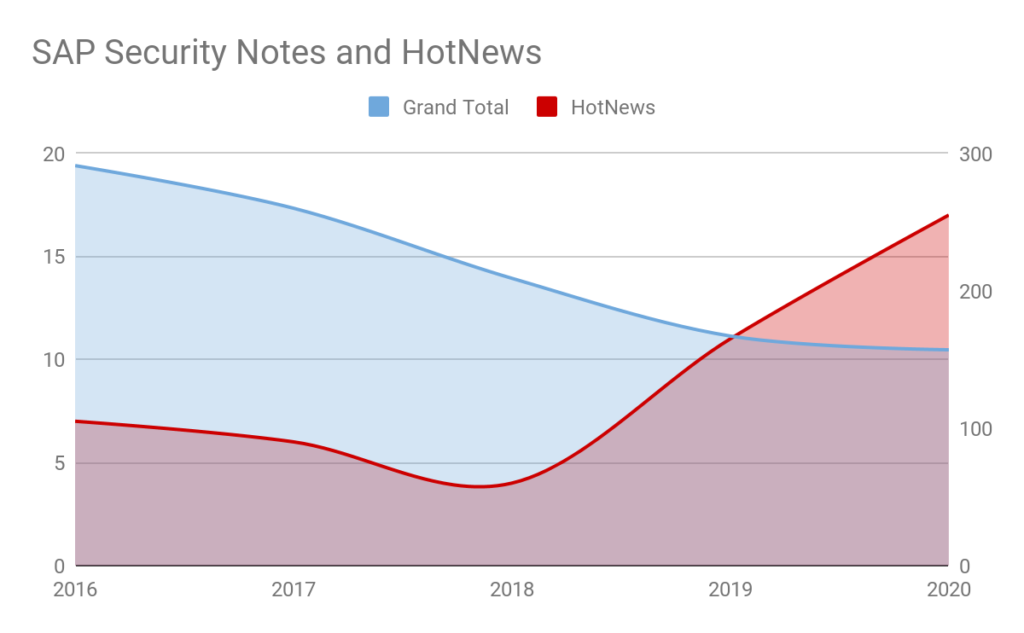 Figure 1—Evolution of SAP Security Notes over the past 5 years
Figure 1—Evolution of SAP Security Notes over the past 5 years
Besides the number of total and critical SAP Security Notes, over the last years, SAP increased the response time to deliver security patches, especially important for critical vulnerabilities, which shows an increasing focus on response time to critical issues.
Going Over Some Examples
In the next sections, we will go over some of the most recent and relevant examples of vulnerabilities, misconfigurations and exploits affecting SAP applications. The ones that are highlighted in this article are the ones that historically generated CERT alerts due to the criticality of the issues.
RECON Vulnerability
On July 14th, 2020, SAP released its regular set of security patches, including the patch for a critical
Common Vulnerability Scoring System (CVSS) 10 vulnerability, which was identified and reported to SAP by the Onapsis Research Labs. This vulnerability allows any unauthenticated attacker to completely compromise the SAP application through the Web service, which could be internal or Internet facing.
Passive scannings of the Internet provided indicators of over 2500 vulnerable and exposed SAP Applications before the patch was released. This proves the broad attack surface that the vulnerability opens by measuring the amount of Internet-facing applications. Besides that, there are potentially thousands of internal SAP applications also exposed as almost every SAP customer was affected by this vulnerability due to the mandatory nature of some specific JAVA-based products, such as the SAP Solution Manager.
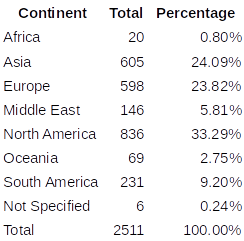 Figure 2—Distribution of Internet-facing systems
Figure 2—Distribution of Internet-facing systems
This vulnerability got the attention of a number of International
Computer Emergency Response Teams (CERT) who released alerts to their audiences in many different countries. Some examples of these are the US-CERT, through the alert
AA20-195A and the BSI CERT-bund through the
CERT Bund -Meldungen - CB-K20/0690. The reasons why alerts were issues are related to the following aspects of the RECON vulnerability:
- A broad attack surface both internal as well as Internet-facing.
- No prerequisites for exploitation, anyone with network access can exploit it.
- Full compromise can be achieved by the attacker.
- Due to the critical nature of SAP applications, business data could be exposed.
SAP Released several SAP Security Notes to address this issue and will continue to update them as more facts become known about the vulnerability and its impact.
If you have not applied the SAP Security Note 2934135 or the mitigation through SAP Security Note 2939665, it is highly recommended to do so to reduce the risk of exploitation, as threat actors are already exploiting it through both manual as well as automated campaigns.
Invoker Servlet Vulnerability in SAP Applications
In 2016, the Onapsis Research Labs identified indicators of exploitation and compromise of dozens of organizations who were exposing SAP JAVA applications to the Internet, without properly taking care of vulnerabilities or misconfigurations. The Invoker Servlet vulnerability in SAP JAVA applications, which was patched by SAP in 2010, was still a prevalent issue amongst SAP installations in 2016 and it opened a significant attack surface that threat actors were using to compromise SAP applications.
With several publicly available exploits to abuse this vulnerability as well as detailed information on how to exploit it, the Invoker Servlet became a very critical issue for SAP applications and because of the criticality as well as the fact that threat actors were actively exploiting it, the very first US-CERT alert around cybersecurity for SAP applications was issued in May of 2016: the Alert
TA16-132A.
 Figure 3—US-CERT Alert highlighting an SAP security issue
Figure 3—US-CERT Alert highlighting an SAP security issue
What made this issue hard to patch is the fact that it is not a pure “software vulnerability,” but is a combination of a software vulnerability and a configuration of the system. So even if organizations fix the issue, it can come back if proper controls are not in place. Even though the issue was fixed almost 10 years ago, and the US-CERT alerted organizations 4 years ago, Onapsis still sees the Invoker Servlet vulnerability in SAP applications between 10-20% of its assessment engagements. This provides another data point around how organizations struggle with applying patches, even the most critical ones.
SAP Released SAP Security Notes to address the issue in 2010 and after the US-CERT alert was released:
10KBLAZE Vulnerability
In 2019, another cybersecurity vulnerability got top level visibility across SAP customers: the 10KBLAZE vulnerability. This issue is not actually a software vulnerability as the ones seen in the previous examples but instead it is a security configuration of a key component of SAP ABAP-based systems: the SAP Gateway. This component is in charge of communicating SAP applications and if not properly secured, it could expose the entire SAP system and potentially its connected applications.
The security settings of the SAP Gateway were known and documented for years, however SAP customers still struggle with securing that component. In May, 2019, public exploits were released at a security conference, making this issue more critical as it significantly increased the probability of exploitation, even for internal systems.
US-CERT raised an alert in this case too:
AA19-122A providing details about the vulnerability, the exploits and some potential mitigations. SAP released SAP Security Notes years before the release of the exploits, to address these configuration issues:
Becoming Proactive with Cybersecurity for SAP Applications
With a security-by-design program you have visibility into your business-critical application environment, the ability to assess for vulnerabilities, prioritize and fix them, prevent configuration drift and detect potential malicious attacks or internal misuse. This program starts by establishing security baselines when assessing and monitoring code, configurations, and aspects of your business processes throughout development and carried through to production.
Figure 4—
A programmatic approach to security and compliance for SAP Applications
In working with some of our largest customers, Onapsis has identified the following key value drivers in defining and implementing an effective security program for your business-critical applications:
- Protect your SAP systems from external attacks and internal misuse by mitigating risk
- Streamline and automate compliance and audit processes to reduce manual effort and minimize inconsistencies
- Devise and implement a cross-functional program that meets the needs of your ERP, compliance and security teams so the impact is continuous and risk management is effective
- Accelerate your key business initiatives such as cloud migration, S/4HANA implementation, digital transformation or technical upgrades with reduced risk
 Figure 1—Evolution of SAP Security Notes over the past 5 years
Besides the number of total and critical SAP Security Notes, over the last years, SAP increased the response time to deliver security patches, especially important for critical vulnerabilities, which shows an increasing focus on response time to critical issues.
Figure 1—Evolution of SAP Security Notes over the past 5 years
Besides the number of total and critical SAP Security Notes, over the last years, SAP increased the response time to deliver security patches, especially important for critical vulnerabilities, which shows an increasing focus on response time to critical issues.
 Figure 2—Distribution of Internet-facing systems
This vulnerability got the attention of a number of International
Figure 2—Distribution of Internet-facing systems
This vulnerability got the attention of a number of International  Figure 3—US-CERT Alert highlighting an SAP security issue
What made this issue hard to patch is the fact that it is not a pure “software vulnerability,” but is a combination of a software vulnerability and a configuration of the system. So even if organizations fix the issue, it can come back if proper controls are not in place. Even though the issue was fixed almost 10 years ago, and the US-CERT alerted organizations 4 years ago, Onapsis still sees the Invoker Servlet vulnerability in SAP applications between 10-20% of its assessment engagements. This provides another data point around how organizations struggle with applying patches, even the most critical ones.
SAP Released SAP Security Notes to address the issue in 2010 and after the US-CERT alert was released:
Figure 3—US-CERT Alert highlighting an SAP security issue
What made this issue hard to patch is the fact that it is not a pure “software vulnerability,” but is a combination of a software vulnerability and a configuration of the system. So even if organizations fix the issue, it can come back if proper controls are not in place. Even though the issue was fixed almost 10 years ago, and the US-CERT alerted organizations 4 years ago, Onapsis still sees the Invoker Servlet vulnerability in SAP applications between 10-20% of its assessment engagements. This provides another data point around how organizations struggle with applying patches, even the most critical ones.
SAP Released SAP Security Notes to address the issue in 2010 and after the US-CERT alert was released:
 Figure 4—
Figure 4—



