RISE with SAP and Its Impact on Security and Compliance
By Uemit Oezdurmus, SAP Global Head of Managed Security Services, and Gunnar Kosche, SAP Service Offering Manager for Cybersecurity and Compliance Services
Contributing Editor: Fred Donovan, SAPinsider
RISE with SAP focuses on bringing core business systems (SAP S/4HANA Cloud, private edition) into a customer environment that is cloud based, process driven, easy to scale, and easy to use.
Geopolitical tensions, environmental challenges, and the COVID-19 pandemic are forcing companies to change their business processes more quickly than ever. RISE with SAP is designed to help organizations adapt to this rapid pace of change by running their processes in the cloud.
Hyperscalers like Amazon Web Services (AWS), Google, Microsoft Azure, or Alibaba are running well-managed and highly secured (physically and technically) data centers worldwide, but where do their responsibilities and liabilities end? What does this mean for customers who want to utilize those environments? How can customers make sure that every aspect of their current landscape’s security is being reflected? How does security for hybrid landscapes work?
While trying to answer these questions, you can uncover additional questions about tooling (are there new/additional solutions to be used?) and processes (do we need to re-design security-related processes?) that relate to the organization’s setup.
When embarking on a RISE with SAP journey, the authors of this article recommend that you tackle the following three topics in parallel:
- Business transformation (business adoption)
- Technical system transformation
- Post-go-live activities
The following sections will shed some light on the main concerns involving the process and try to answer the most relevant questions.
Let’s start with a look at liabilities and responsibilities (Figure 1). In the classical on-premise world, everything was under the control and responsibility of the customer. Now, with the transformation approach, SAP customers are required to re-think roles, responsibilities, and liabilities.
Figure 1: RISE with SAP in a Nutshell
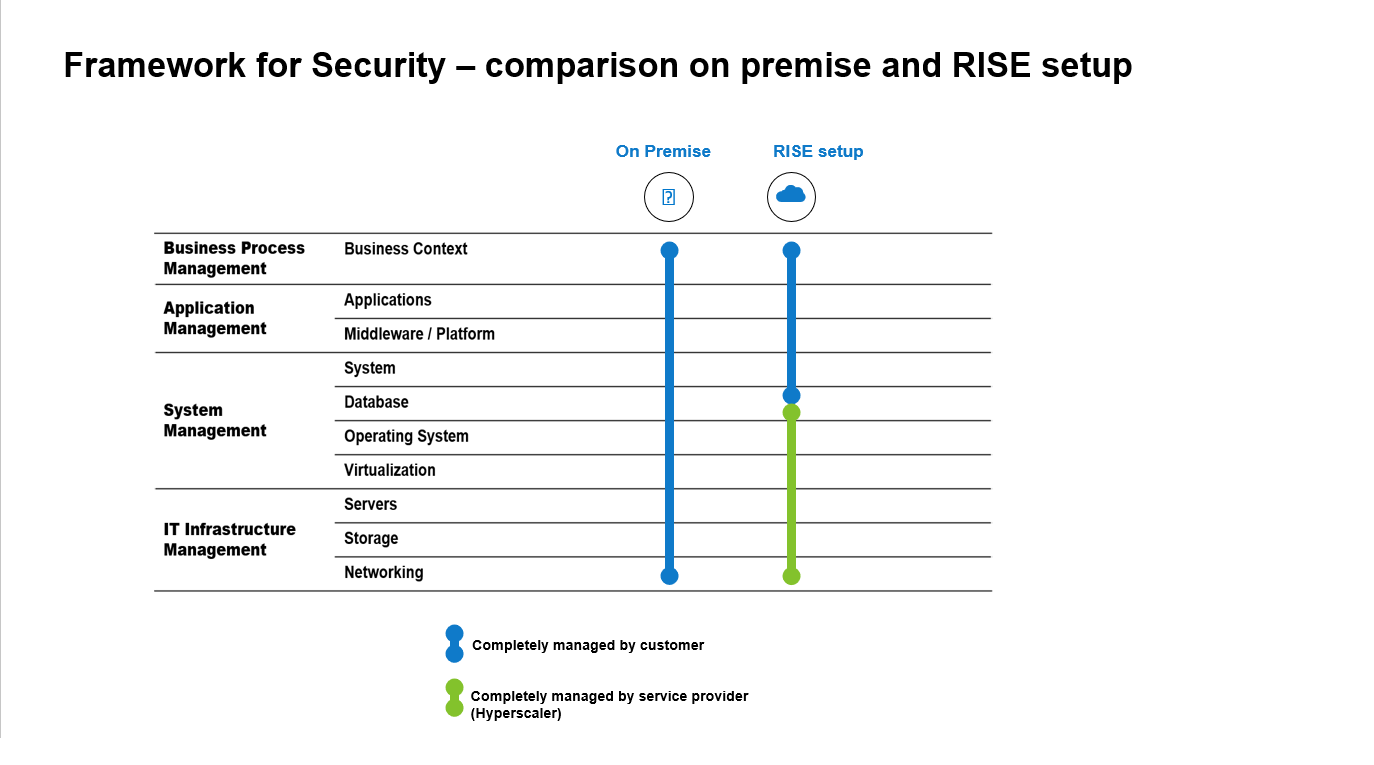
Source: SAP
In the new working model, hyperscaling vendors must fulfill their part of security and compliance while the rest of the tasks remain with the customer.
RISE with SAP offers the following:
- Business transformation in the cloud with predefined packages
- Bundling several products into one offering
- One contract covering service level agreements (SLA), operations, and issue management
The idea is to offer a solution for the transition of business processes to a cloud environment. This includes one of the key pillars — business process intelligence — to review and refine the customer business processes.
Additionally, SAP is offering process discovery for SAP S/4HANA transformation and RISE with SAP. This provides insights to understand an organization’s current business process performance and identify SAP S/4HANA functionalities to support ongoing business goals.
RISE with SAP also contains the integration of operations to get the application as a cloud offering.
RISE with SAP is an offering provided by SAP that includes business advisory services supporting business transformation and collaboration with the SAP partner ecosystem (Figure 2).
This article is focused on the SAP Customer Success program, which includes consulting, support, and operations.
Figure 2: Overview of RISE with SAP
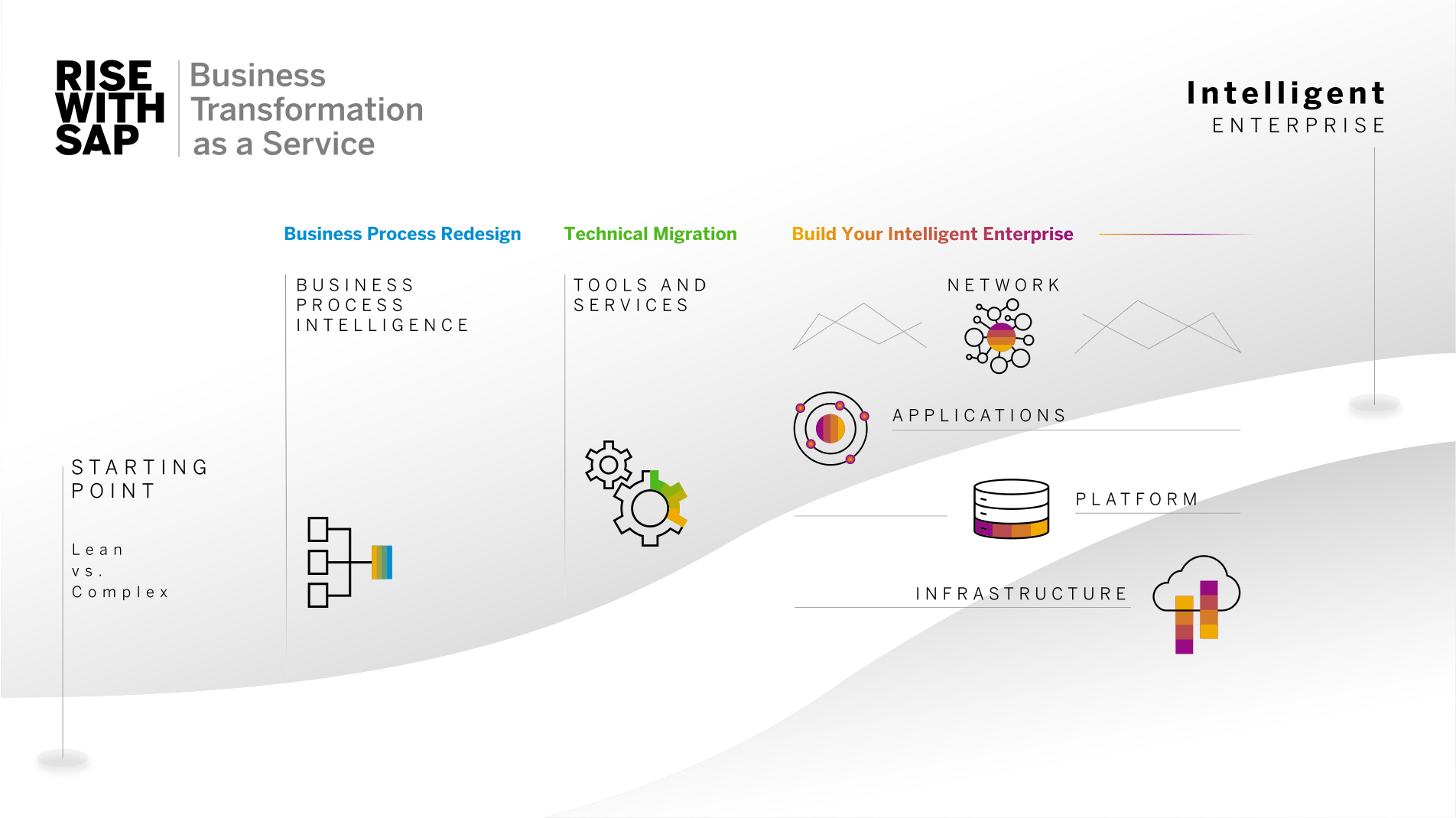
Source: SAP
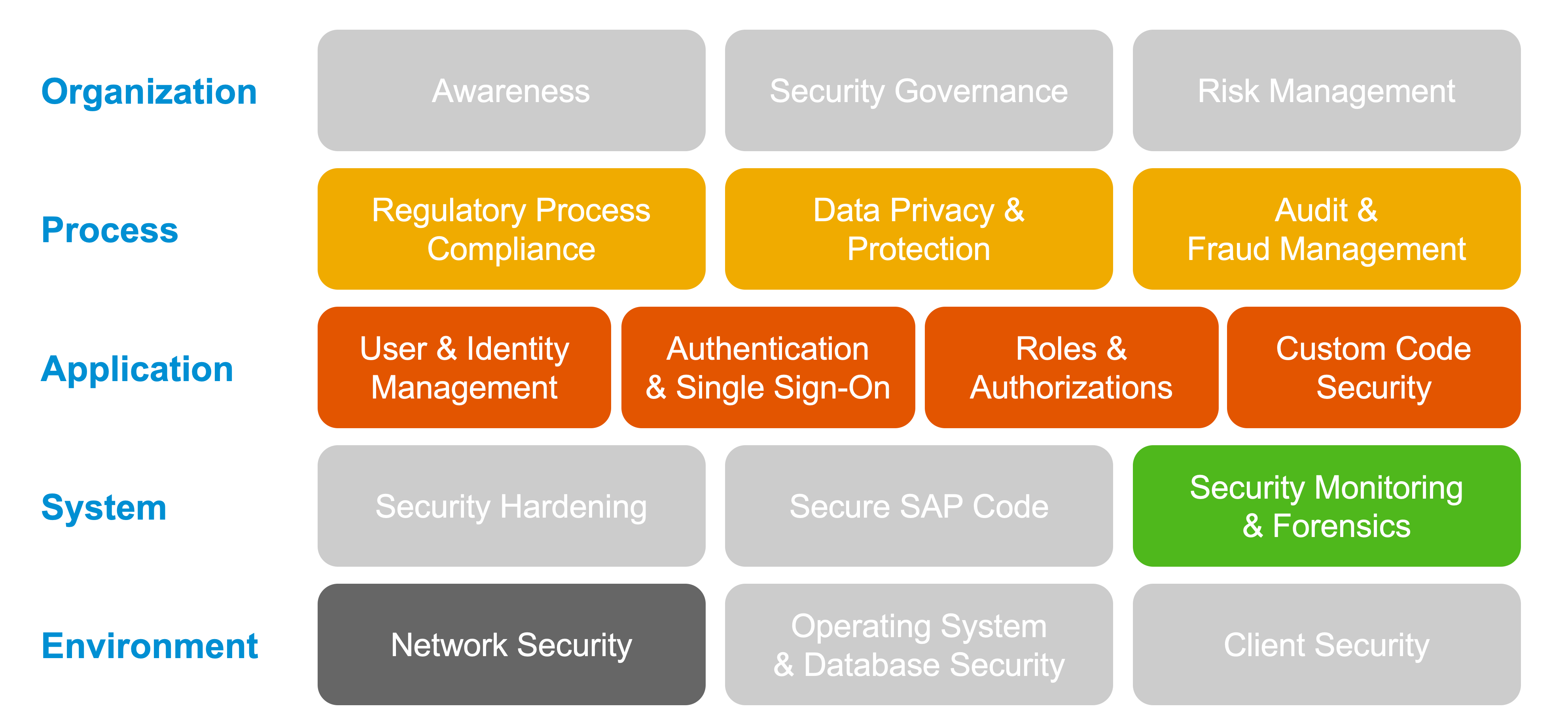
Secure Operations Map
The transformation to a cloud model hands over parts of cybersecurity to a company’s hyperscaler partner and SAP. SAP takes care with certified processes to keep your data secure — but some responsibility and tasks remain with you.
To address cybersecurity areas from different perspectives like identity and access management (IAM) or for a specific solution like SAP S/4HANA, SAP designed the Secure Operations Map (SOM).
The SOM (Figure 3) offers you guidance on how to build a strong security and compliance foundation for your SAP landscape.
Figure 3: Overview of SAP Secure Operations Map
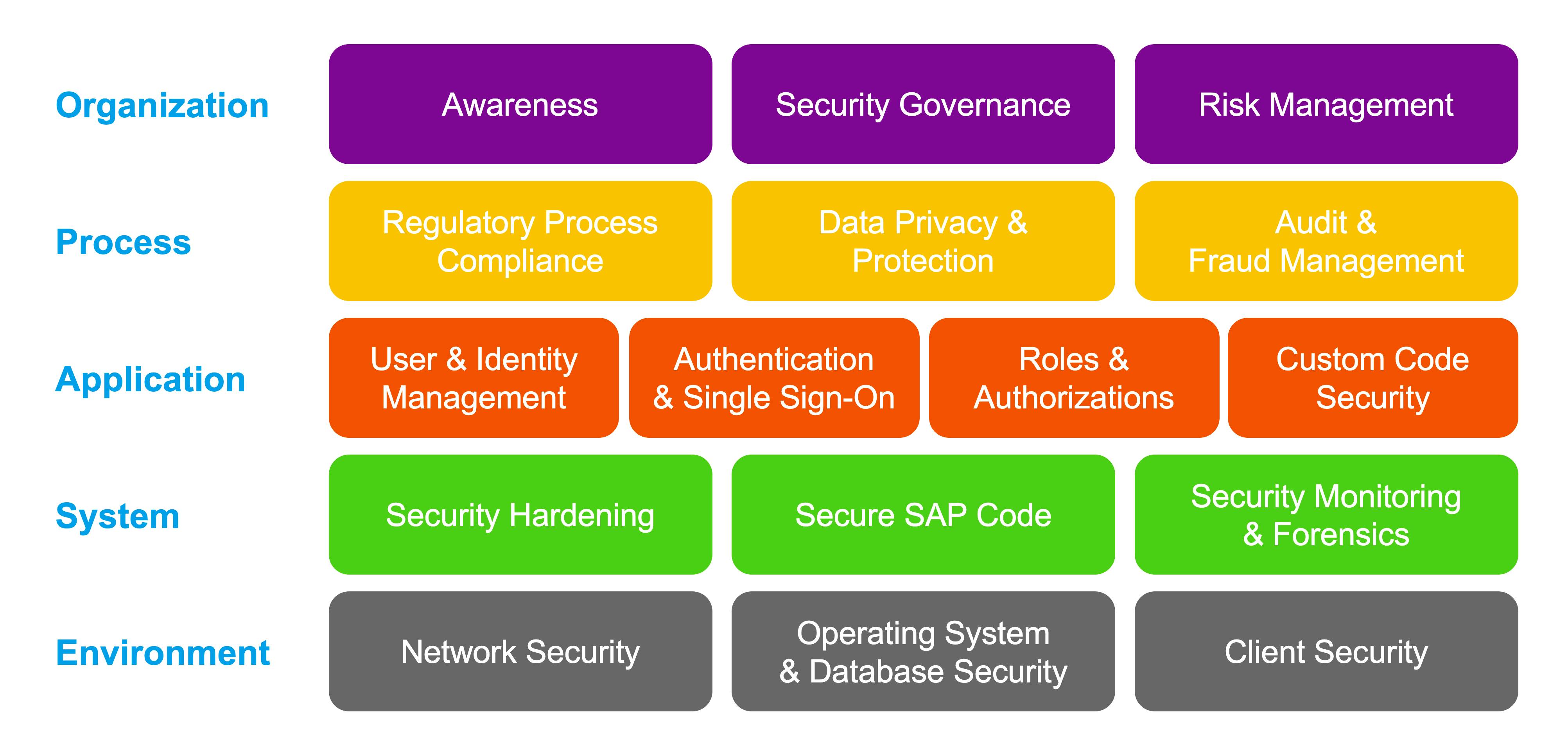
Source: SAP
The SOM is a reference model that structures the broad areas of cybersecurity and creates a solid base for a 360-degree review of cybersecurity and compliance practices in customer landscapes.
The SOM was designed based on SAP’s view of security topics, needs, and branches, but it can be mapped to other widely known cybersecurity frameworks such as the National Institute of Standards and Technology’s Cybersecurity Framework or the German Federal Cyber Security Authority’s IT-Grundschutz. What is particular to the SOM is that it can be used globally for the SAP environment.
The SOM is further interpreted in the context of SAP systems, although the model also could be applied to non-SAP realms.
Business Transformation with Business Process Intelligence
The intelligent business process re-design as part of RISE with SAP affects cybersecurity and compliance. It uses constant benchmarking to analyze, design, improve, roll out, and monitor business processes (Figure 4). From this perspective, cybersecurity and compliance follow the same approach.
Figure 4: RISE with SAP BPI Component
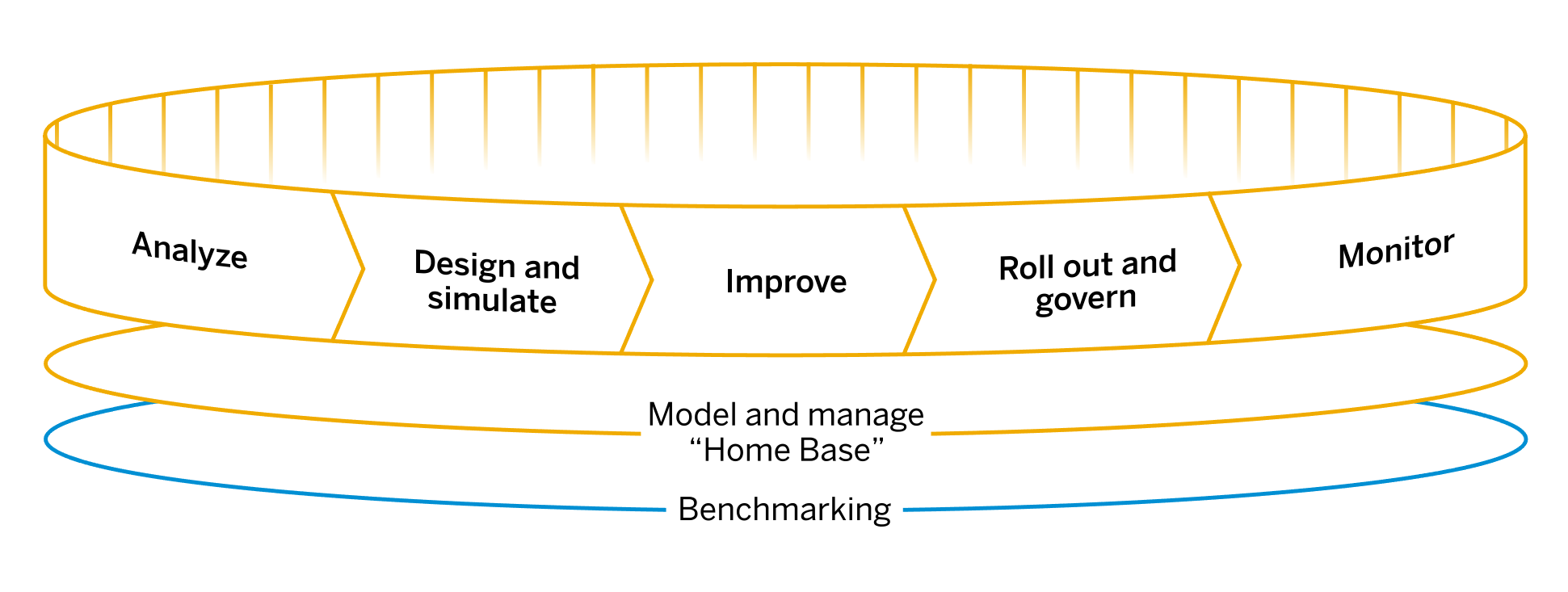
Source: SAP
The authors of this article recommend that you revisit security on a regular basis. New functionality and new technologies require new security measures. New attack patterns arise and need to be countered, and your processes need adjustments.
Remember, security involves measuring risk, so you can have a higher or lower level of security based on risk.
In the case of SAP S/4HANA and IAM, the business process re-design with RISE with SAP impacts several SOM layers. The “organization” and “process” layers are the less technical side of the SOM compared to the other layers. At the “organization” layer, it is important to define the environment for SAP systems and SAP cloud solutions. It sets the stage and defines needs and requirements as inputs to be considered.
General security awareness is an important pre-condition to achieve security. Not everyone has to be a security expert, but everyone needs to contribute to the security of the organization. Ignoring or even circumventing security rules and mechanisms can endanger the whole landscape. Awareness thus is directly linked to user-friendliness and ease of handling security mechanisms or configurations.
A re-design of an intelligent hire-to-retire business process as part of RISE with SAP — using automated distribution, modern user interfaces, and a secure single sign-on with multi-factor authentication and robust IAM — will significantly improve your security awareness.
Technical System Transformation — What to Consider When Transforming Your Business with SAP S/4HANA
A good starting point to get an overview of your landscape and security settings is using the SAP Early Watch Alert as part of SAP’s services and support offerings. (Read the blog post “Displaying Security Alerts in the SAP EarlyWatch Alert Workspace” and learn how to get information about the security status of your system landscape.) With this dashboard you get an overview and details about your landscape, so you can understand in which areas you could benefit the most from the different cloud options we offer with RISE with SAP. It depends on your requirements and adoption level of the “as a service” offerings. This decision also changes the level of detail you must manage regarding different cybersecurity and compliance topics.
RISE with SAP is a holistic enterprise transformation and change process. SAP pulls its knowledge from the SAP Customer Success program and packages that knowledge to help customers with their technical migration. You can benefit from the improved automation to roll out the recruit-to-retire business process and the corresponding IAM processes, tools, and knowledge. You have the choice to extend your IAM or redefine it with SAP’s Software as a Service (SaaS) solutions.
An SAP S/4HANA transformation with IAM already contains changes like the use of HTTP interfaces with web services and SAP Fiori apps. The existing SAP GUI-based authorization concept requires a review, including SAP Fiori catalogs and our SAP best practices recommendations. This information guides you through the process and offers authorization concepts created automatically based on your authorizations and usage.
SAP S/4HANA also introduced the concept of the business user, which combines the detailed data of a business partner with a user and reduces the redundancy in the corresponding user entity. This requires a review of the user flows, including new interfaces to manage the entities. In the SAP One Domain Model, the user includes a subset of attributes of a person and other information like IDs and authorizations. This split of entities is important for the master data flows and user flows of the intelligent enterprise.
RISE with SAP comes with SAP Business Technology Platform (BTP) as a Platform as a Service (PaaS) solution that integrates and extends your SAP landscape. The SAP BTP includes new user, authentication, and authorization concepts.
The different cybersecurity and compliance topics for business transformation are covered with templates, reference architectures, and guidance from services and support as part of the RISE with SAP offering. Cybersecurity and compliance follows a benchmarking and review process, which includes a hand-over after the SAP S/4HANA transformation to the SAP Cloud Application Services to operate the solutions.
Post-Go-Live Activities
Once a successful implementation and configuration has been achieved following SOM best practices, the journey starts with the new hybrid cloud environment (Figure 5).
Figure 5: Secure Operations Map — RISE with SAP and SAP S/4HANA
Source: SAP
Now, the day-to-day activities running in a highly secure and compliant system landscape must be planned and processed, keeping a focus on static system security.
While it is advisable to cover static system security with a sophisticated patch management program, there must be a security strategy plan and execution for all aspects of a dynamic system as well. Here the managed security services provided by the SAP Cloud Application Services team come into play with a holistic and mature portfolio of services. It is very helpful to outsource day-to-day activities to SAP experts and free up resources internally for other innovative topics and activities of the core business.
For example, the initial segregation of duties (SoD) checks and the new authorization enhancements are a base for building and adjusting roles and authorizations as requested by the lines of business. All adjustments and newly created roles and authorizations need to comply with regulations and must be auditable. The challenge here is that the entire landscape must be considered: Where to create the users, roles, and authorizations? How to ensure SoD? What should reporting look like? What is the process for creating and changing roles and authorizations?
There is a need to add, delete, connect, and disconnect systems securely. Managed security services provided by SAP Cloud Application Services deliver sophisticated advisory, planning, and execution of these tasks, with a focus on hardening systems and interfaces and regular penetration testing.
When it comes to custom coding, it must be made secure prior to release. Custom code needs to be checked for any security gaps, miscoding, or even hard-coded backdoors. Only coding checked for vulnerabilities should be released to avoid any breaches or misuse.
Another very important aspect is security monitoring. Having SAP’s Early Watch Alert Management service is good, but not enough. There should be a combination of Early Watch and SAP Solution Manager or SAP Focused Run to cover all aspects of a static system security. In addition, SAP offers a sophisticated solution for in-application real-time monitoring called SAP Enterprise Threat Detection. This is a valuable addition to the entire monitoring strategy and can be combined with an existing security incident and event monitoring (SIEM) solution.
Managed security services provided by SAP Cloud Application Services offer support with experts taking over monitoring tasks and helping customers with forensics and countermeasures. There is also a new offering for SAP Enterprise Threat Detection Cloud, which is being delivered in combination with a baseline set of SAP Cloud Application Services managed security services.
Indeed, a well-planned and executed transformation is a must to be aligned with all involved vendors. Especially when it comes to security, there must be a clear strategy to co-operate over the entire landscape in a secure and compliant manner.
RISE with SAP provides a path to the intelligent enterprise for every customer, independent of starting point or complexity. SAP experts are in place to guide, support, and act as the trusted advisory in any stage of your transformation journey.








