Cybersecurity and Data Protection: Taking an Integrated Approach
By Fred Donovan, Senior Editor, SAPinsider
“The threat actor only needs to be right once. We need to be right every time,” says Scott Margolis, Managing Director for the Data Privacy and Protection Practice at Ernst & Young (EY).
The best way to stay ahead of threat actors, considering the global shift to remote work, is to implement an “integrated approach” to cybersecurity, data privacy and protection, and governance, Margolis advises. An integrated approach includes anticipating and thwarting threats, following cyber hygiene best practices, securing applications and data, and planning how to respond to cyber incidents.
Explore related questions
EY and SAP are working together to provide organizations with services and solutions to optimize security. They share insights on inventorying, classifying, and prioritizing data; analyzing how personal data is collected, used, and shared; understanding responsibility for data security across the organization; protecting enterprise applications and data; and making a defensible approach to cybersecurity sustainable.
SAP has identified cybersecurity and data protection priorities that you should include and embed in your business strategies: monitor applications that hold valuable data, scan for vulnerabilities, provide transparency, protect personal and sensitive data, and respond effectively to new privacy regulations (Figure 1).
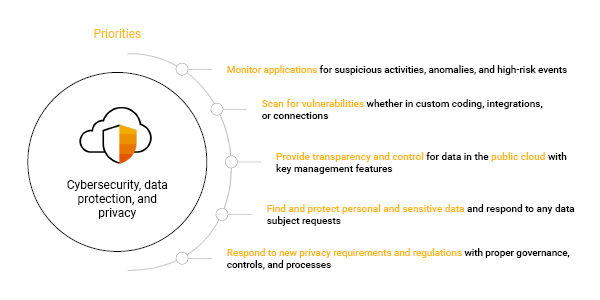
Fig. 1: Cybersecurity and Data Protection Priorities from SAP
Organizations that follow good cyber hygiene practices, in particular setting up and prioritizing a regular patch process, will be better positioned in improving security. SAP follows this advice, patching its own systems the second Tuesday of every month and encouraging other organizations to seek patch management advice.
A reliable source of enterprise security best practices is the National Institute of Standards and Technology’s (NIST) Cybersecurity Framework. You can learn more about this framework and how to apply it in your own organization by checking out “How to Build a Strong Security and Compliance Foundation for Your SAP Landscape: Ensure a Secure Environment Using SAP Solutions and the NIST Cybersecurity Framework.” This blog outlines how organizations are responsible for their data and how it can best be protected.
In one recent project, SAP ERP systems using either SAP ECC or SAP S/4HANA hosted on hyperscalers such as Microsoft Azure and Amazon Web Services were connected to the SAP Data Custodian pre-production tenant. Five use cases were implemented as part of this project — data regulation, data protection, anomaly detection, information detectors, and key management. The case studies demonstrated how SAP Data Custodian can help organizations by providing greater control and transparency of data in the public cloud.
To bolster data privacy, SAP Cybersecurity Solution Advisor Anne Marie Colombo recommends that organizations control user access to data by managing and securing it. SAP Privacy Governance assists organizations in understanding the mandates of data privacy regulations, like the European Union’s General Data Protection Regulation, and managing the controls needed to comply with these rules. The SAP product enables customers to manage data privacy impact assessments, data subject rights requests, and privacy policy distribution.
To learn more about adopting and implementing an integrated approach to cybersecurity and data privacy, read our recent article “A Holistic Approach to Managing Cybersecurity & Protecting Your Data.”





