Attacks to an SAP System: Bypassing Detection and How to Prevent It
Detecting attacks to SAP applications has become more and more important as we see companies making the headlines after being breached. Equifax is one example of how important it is to apply security patches and maintain the security of your applications.
Security patches not only prevent your SAP application from being exploited but also ensure that the system is properly functioning and recording all the necessary information to potentially identify malicious activity within the application.
There are multiple examples of security patches that can help you ensure that the information you have in your logs is consistent and was not tampered with. Here, I provide an example of a security vulnerability that attackers could exploit to hide their trails.
Explore related questions
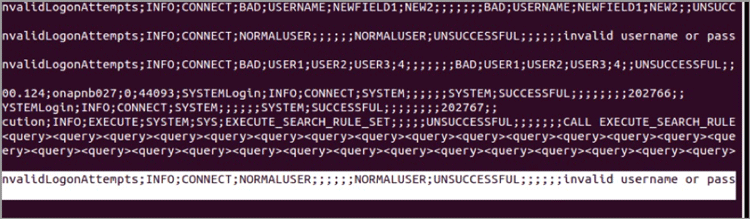
This software weakness affects SAP HANA 1.0 databases without the proper support package versions (fixes are available for SAP HANA 1.0 SP085.05, SP097.02 and SP102). Without the proper fixes, an attacker can insert arbitrary fields in the log file, even without authentication. For example, in the case of an invalid logon attempt to the SAP HANA Extended Application Services (an important event from a security standpoint, by the way), the login would look like the script in the system log shown in Figure 1.
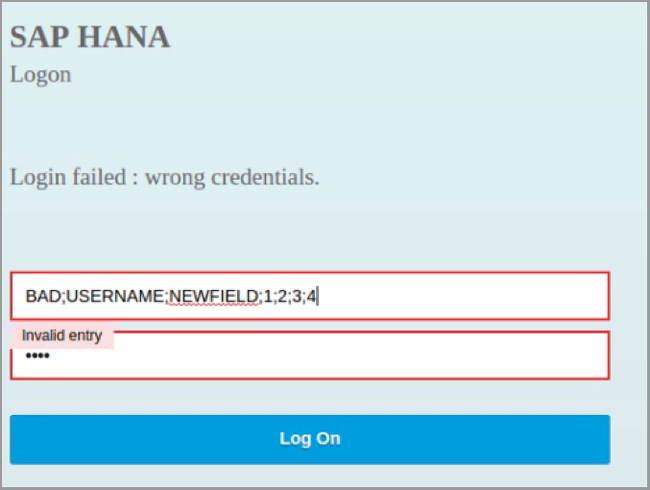
However, if a malicious attacker tries to use a brute-force attack against the SAP HANA system, he can inject arbitrary log fields. This attack works by adding semicolon characters to the username as shown in Figure 2.
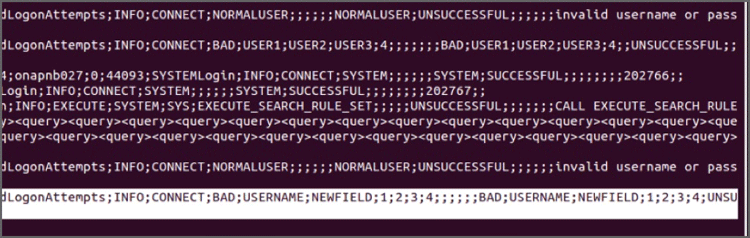
After the successful injection of fields into the log file, the log line with the unsuccessful login event contains additional data, as shown in Figure 3.
This is an important issue to fix, through SAP Security Note 2197459, as you cannot rely on your SAP HANA logs otherwise. You can learn more about strategies to secure your SAP systems at Cybersecurity for SAP Customers 2018 in Prague June 27–29. For more tips on how to secure an SAP environment, read this blog.