Managing the Identity Life Cycle in Hybrid SAP Environments
by Regine Schimmer, Security Product Manager, and Matthias Kaempfer, Security Product Manager, SAP
Ensuring the security of IT systems is a primary concern for businesses of all shapes, sizes, and industries. When it comes to securing on-premise landscapes, the risks and challenges involved are fairly well known at this point, and most companies have invested in proven software such as SAP Single Sign-On, SAP Identity Management, SAP Solution Manager, and SAP Access Control to ensure the protection of their data and business processes.
Explore related questions
As businesses extend their landscapes to the cloud, however, they are faced with a new set of challenges. While cloud-based solutions have many advantages from a business and operations perspective, hybrid landscapes can be complex to manage when it comes to security. Companies must deal with challenges that arise from connecting cloud-based solutions to on-premise solutions, establishing secure communications, and, most important, ensuring compliant processes across both worlds.
To help organizations securely develop and administrate cloud-based solutions, SAP offers Enterprise Security Services — a portfolio of solutions that address key security needs for cloud-based applications. But what about hybrid environments that include not only cloud applications, but also on-premise applications with an existing on-premise security infrastructure already in place? How can organizations extend their landscape protection into the cloud while preserving their on-premise security investments?
This article shows IT architects and security administrators how to build a security bridge between on-premise and cloud-based applications in hybrid landscapes, providing the flexibility of the cloud with the stability of existing on-premise systems. It introduces Enterprise Security Services and then looks at how user authentication and identity management can be applied to hybrid landscapes. It also explains how to take advantage of existing on-premise security investments and how to manage risk and compliance in a hybrid environment.
Enterprise Security Services from SAP
Enterprise Security Services is a holistic approach for addressing cloud security. It provides a comprehensive guide to the different security services that are available and explains when they should be used and how to integrate them. Enterprise Security Services is composed of the following four categories (see Figure 1):
- Cloud identity services address identity and access management in the cloud. They can be used across the SAP cloud solution portfolio, and they include the Identity Authentication and Identity Provisioning services as a part of SAP Cloud Identity Services.
- Secure development services help support the development of secure applications on SAP Cloud Platform. These services, such as SAP Cloud Application Programming Model and the Cloud Connector, enable developers to build secure enterprise business applications.
- Risk and compliance are provided by solutions such as SAP Cloud Identity Access Governance to help security administrators manage risks and meet corporate compliance goals.
- Insight is delivered by SAP through its SAP Trust Center site to provide a transparent view into how SAP manages its customers’ cloud applications. With SAP Data Custodian, SAP customers can gain insight into the location and movements of data.
Security partners complete the picture by providing generic services such as static code and open source vulnerability scanners.
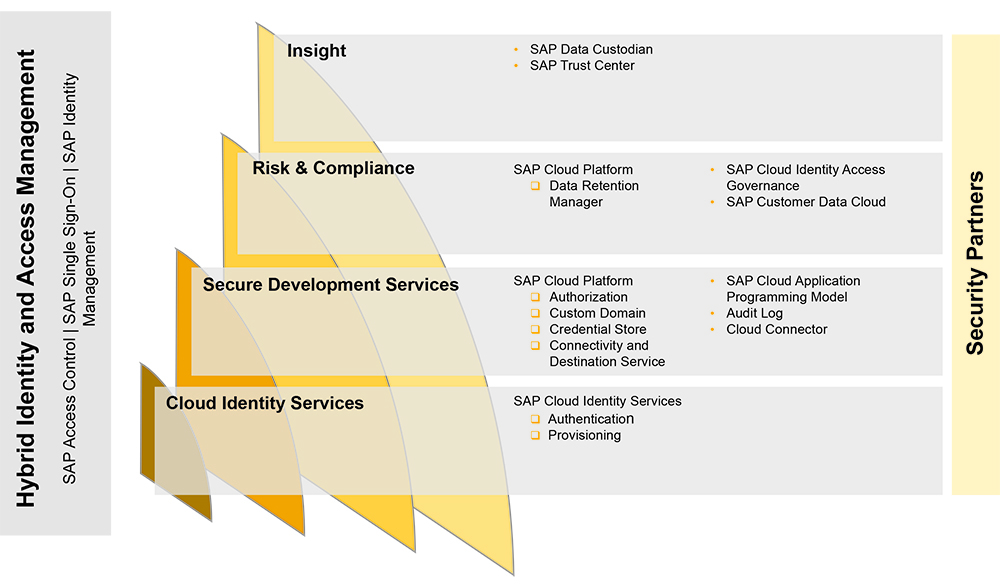
Figure 1 The Enterprise Security Services approach from SAP encompasses solutions, services, and information that help organizations address cloud security
To support customers running hybrid landscapes, SAP provides options for bringing these cloud-based security solutions and services together with existing on-premise security solutions for identity and access management in hybrid landscapes. In this article, we look at extending the on-premise solutions SAP Access Control, SAP Single Sign-On, and SAP Identity Management into the cloud for use with SAP Cloud Identity Services.
Before diving into the details, we’ll start by explaining how an organization’s existing security solutions can provide it with a head start in ensuring secure identity and access management in a hybrid environment.
Get a Head Start with a Solid Security Infrastructure
Let’s look at a typical SAP customer scenario, where SAP Business Suite or SAP S/4HANA is deployed in an on-premise data center. The organization might also choose to run parts of the business system on an infrastructure-as-a-service (IaaS) provider. The security advantage of this type of setup is that regardless of where the system is running — whether on premise or on the IaaS — most of the existing on-premise security measures can be applied. This is because in both cases, the responsibility for the complete software stack is with the SAP customer. The existing on-premise security measures in many enterprises include SAP Identity Management, SAP Single Sign-On, SAP Access Control, and SAP Solution Manager. Figure 2 provides an overview of an example system landscape.
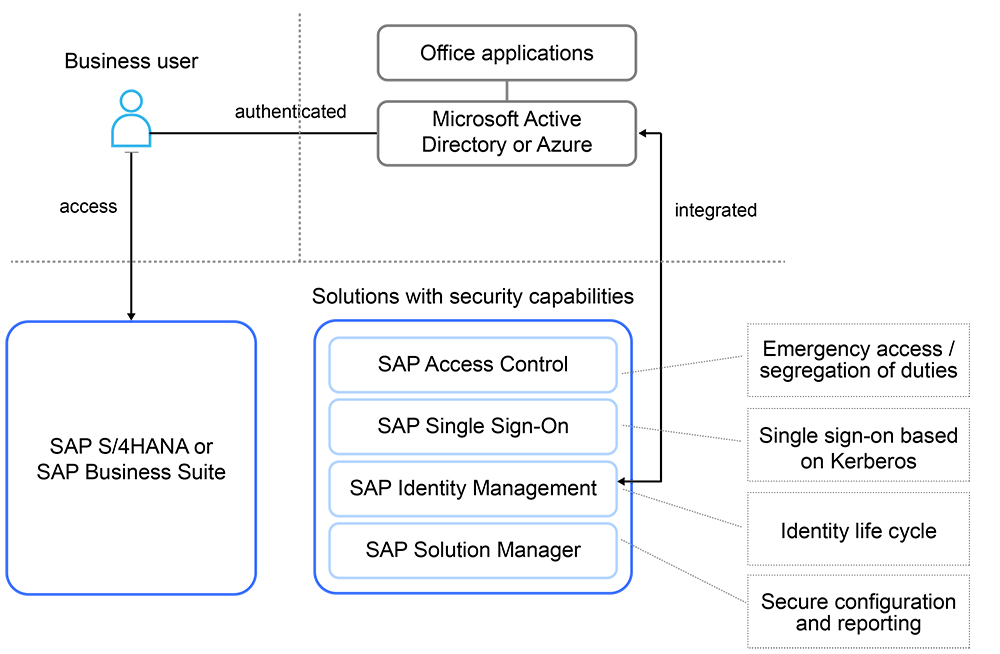
Figure 2 An example on-premise infrastructure for identity and access management
Technology and business never stand still, however, and in many companies, some lines of business are starting to push for cloud-based software-as-a-service (SaaS) solutions, which means security administrators must devise a security strategy for hybrid landscapes. While moving to a hybrid landscape adds some complexity to the picture, the investment in existing on-premise security infrastructures will pay off. The next section looks at how the existing infrastructure can smooth the path when extending existing on-premise user authentication and identity management into the cloud.
User Access in Hybrid Landscapes
Let’s start with single sign-on for business users in hybrid landscapes. Typically, an identity management system is used to manage business users for on-premise ABAP systems, while Microsoft Active Directory is used to access the office environment. In office environments, the standard authentication method is a username and password that will be converted into a Kerberos/SPNEGO (Simple and Protected GSSAPI Negotiation Mechanism) security token by Microsoft Active Directory Server. Note that for simplicity, we will refer to Kerberos/SPNEGO as simply Kerberos in this article, since SPNEGO is just a wrapper used around Kerberos for any web-based usage scenarios.
There are four types of user authentication typically used in hybrid SAP landscapes (see Figure 3):
- Single sign-on to SAP cloud applications
- Single sign-on to on-premise systems
- System-to-system principal propagation in a hybrid landscape
- System-to-system principal propagation on premise
What Is Principal Propagation?
A business user authenticates against the primary system. If this system wants to receive additional data from another system, it is often required to do it on behalf of the user or with the permissions of the user in the target system. A system-to-system communication with principal propagation allows the system to make an application programming interface (API) call on behalf of a user and not with a generic technical user. This has the advantage that there are no breaks within the authorization concept.
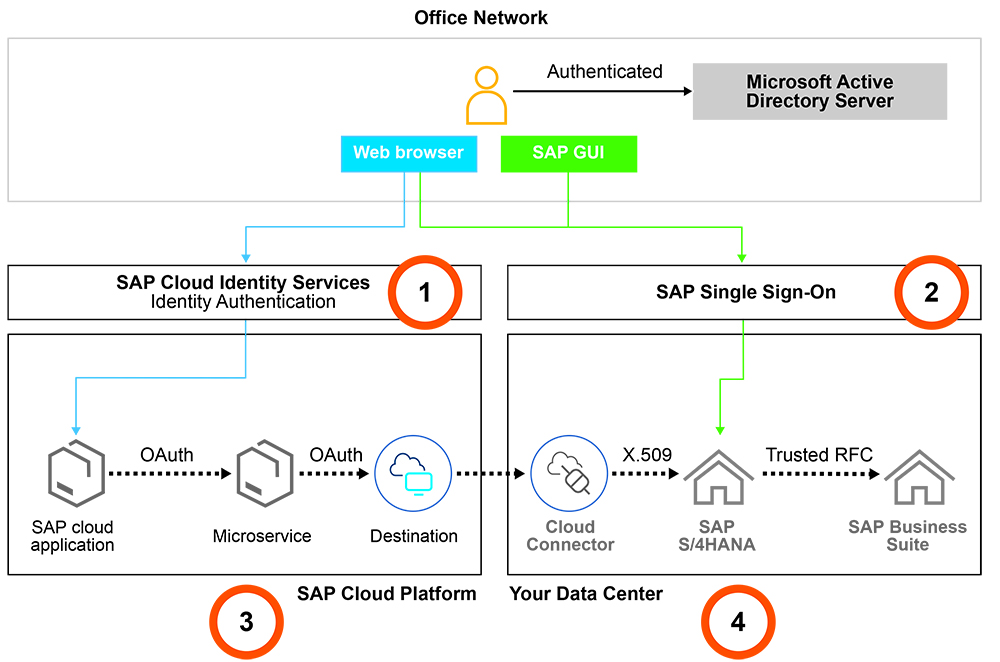
Figure 3 Four types of user authentication typically used in hybrid SAP landscapes
1. Single Sign-On to SAP Cloud Applications
Here, Identity Authentication — a component of SAP Cloud Identity Services — serves as the identity provider based on the SAML (Security Assertion Markup Language) standard. It is the central authentication point for business users to authenticate against SAP cloud applications, such as SAP S/4HANA Cloud and SAP Cloud Platform.
There are multiple options for enabling business users to authenticate against SAP cloud applications via Identity Authentication. In addition to the traditional username and password method, there are three other authentication methods that also allow you to integrate Identity Authentication with non-SAP security solutions:
- Using Kerberos tokens
- Using an X.509 certificate provided by SAP Single Sign-On or a third-party solution
- Integrating Identity Authentication with a third-party SAML-compliant identity provider
Kerberos or user certificates are security tokens on the user device. They can be used to authenticate against Identity Authentication without reentering the username and password. Here, we focus on the most commonly used methods in hybrid SAP landscapes: Kerberos and integration with a third-party SAML-compliant identity provider.
Many companies decide to integrate their on-premise and cloud environments with Kerberos, because it is very simple to apply. Kerberos security tokens are issued by Microsoft Active Directory Server and then available on the user device. The web browser on the user device will pick up the token for authentication. Identity Authentication verifies the token and then transforms it into a SAML token, which is the standard authentication method for enterprise cloud applications such as SAP S/4HANA Cloud and SAP Cloud Platform.
The second option is to integrate Identity Authentication with a third-party SAML-compliant identity provider, such as Microsoft Azure. To support this scenario, SAP offers multiple integration options — here, we describe the two most commonly used:
- Using Identity Authentication as a proxy
- Synchronizing user data
With the proxy mode, Identity Authentication delegates the authentication to a trusted identity provider such as Microsoft Azure, which takes over the process of authentication, issues the SAML token, and provides the SAML token to the web browser on the user device. This token is then used to access the business application. With the synchronization option, Identity Authentication issues the SAML token, but based on synchronized user data from Microsoft Azure. The best option depends on the architecture or the structure of the IT organization. If there is a dedicated SAP department, this team might want to be responsible for the business application end to end and often will choose to synchronize users.
Note!
It is important to note that eventually, most SAP cloud applications will only trust Identity Authentication as their primary SAML identity provider, which means Identity Authentication will become mandatory to access SAP cloud applications. The reason for this is that there must be a common, central point for authentication so that SAP can provide optimized integration and preconfigured cloud systems.
2. Single Sign-On to On-Premise Systems
If business users want to access on-premise ABAP-based systems via SAP GUI or a web browser, the well-established SAP Single Sign-On solution is a good choice:
- For access via SAP GUI, the options are Kerberos and X.509 certificates.
- For access via web browsers, the options are Kerberos, SAML, and X.509 certificates.
To enable single sign-on for SAP GUI, which is still commonly used, the Secure Login Client component of SAP Single Sign-On is deployed along with SAP GUI. This allows the use of Kerberos security tokens, issued by Microsoft Active Directory Server, on the user device. Here, the Secure Login Client picks up the Kerberos token and sends it via SAP GUI to the ABAP system. SAP Single Sign-On enables the ABAP system to validate the token for authentication. Ideally, the same user IDs are used in Microsoft Active Directory Server and the SAP system — if not, a mapping table must be maintained.
You can use a Kerberos token for the entire authentication, but you can also choose to use X.509 user certificates. Certificates are sometimes required to integrate non-SAP applications and can help if you are using multiple unharmonized Microsoft Active Directory Servers. The Secure Login Server component of SAP Single Sign-On will generate a short-lived user certificate and deploy it to the user device. The business user must provide a username and password or a valid Kerberos token to receive the certificate.
If a business user wants to access an SAP Fiori or any other browser-based application, there are three options:
- Kerberos: The web browser will use Kerberos for authentication. SAP Single Sign-On enables the SAP system to accept Kerberos tokens.
- Kerberos to an X.509 certificate: This would follow the same steps described for SAP GUI. The user certificate will also be available in the web browser for authentication.
- SAML: The ABAP system also supports SAML tokens for authentication. The tokens are issued by SAP Cloud Identity Services or a third-party SAML-compliant identity provider.
If SAP GUI is not in use, SAML is a good choice, since it is often the common denominator in hybrid landscapes. While historically all SAP user interfaces were based on SAP GUI, all new user interfaces run in a web browser. Whether an organization is still using SAP GUI depends on the individual system landscape and the adoption of new user interface technologies, such as SAP Fiori, within the company.
3. System-to-System Principal Propagation in a Hybrid Landscape
Here, a business user is authenticated against the organization’s custom cloud applications on SAP Cloud Platform via Identity Authentication. There is also an additional microservice, which is called via the custom cloud application, and the microservice itself needs to access data from an on-premise system via a remote function call (RFC). The requirement is that the system-to-system communication is done with the permissions of the business user. To solve this problem securely, SAP Cloud Platform supports user propagation (system-to-system communication on behalf of a business user).
The steps within the system-to-system communication include the following (note that most of these steps happen automatically in the background):
1. To enable custom-cloud-application-to-microservice communication:
- The business user accesses a custom cloud application with a valid SAML token.
- The token is forwarded to the authorization server (XSUAA, which is a component that manages authentication to applications deployed in SAP Cloud Platform).
- The authorization server adds the authorization information of the business user and generates an OAuth token on behalf of the business user.
- The OAuth token is used to authorize against the microservice.
2. To enable microservice-to-on-premise communication:
- The destination to the on-premise system must be maintained within SAP Cloud Platform.
- A secure tunnel must be established via the Cloud Connector, which links SAP Cloud Platform applications and on-premise systems.
- The Cloud Connector converts the OAuth token into an X.509 user certificate.
- The user certificate is used to authenticate against the on-premise system.
- The user authorizations of the on-premise system are applied to the session.
4. System-to-System Principal Propagation On Premise
System-to-system authentication between two on-premise systems on behalf of a user is not new to SAP customers. We briefly describe it here to provide a full picture.
Sometimes business processes span across multiple SAP systems in SAP customer landscapes — for example, SAP S/4HANA may request data from SAP Business Suite via an RFC. To support this scenario, many years ago SAP established the concept of a trusted relationship between ABAP systems. This means that one ABAP system trusts the user authentication process of another ABAP system, and the system will apply user authorizations within the local system.
Identity Management in Hybrid Landscapes
Once a user is authenticated, it is time to manage what that user may and may not do in the business systems. As mentioned earlier, many SAP customers have invested a significant amount of resources in a well-defined identity management system for their on-premise applications. The SAP ERP Human Capital Management solution is often used as the main system for employee information, and SAP Identity Management securely provisions this data to the on-premise SAP and non-SAP systems across the system landscape. With this approach, user data is always up to date, user rights can be granted and revoked at the touch of a button, and many manual, error-prone processes are eliminated.
But what about hybrid landscapes? Fortunately, there is no need to start from scratch to incorporate cloud applications — SAP Identity Management can simply be extended into the cloud. SAP Cloud Identity Services offers the Identity Provisioning component, which can be integrated with SAP Identity Management. Identity Provisioning serves as a central hub for user provisioning into SAP cloud solutions (see Figure 4).
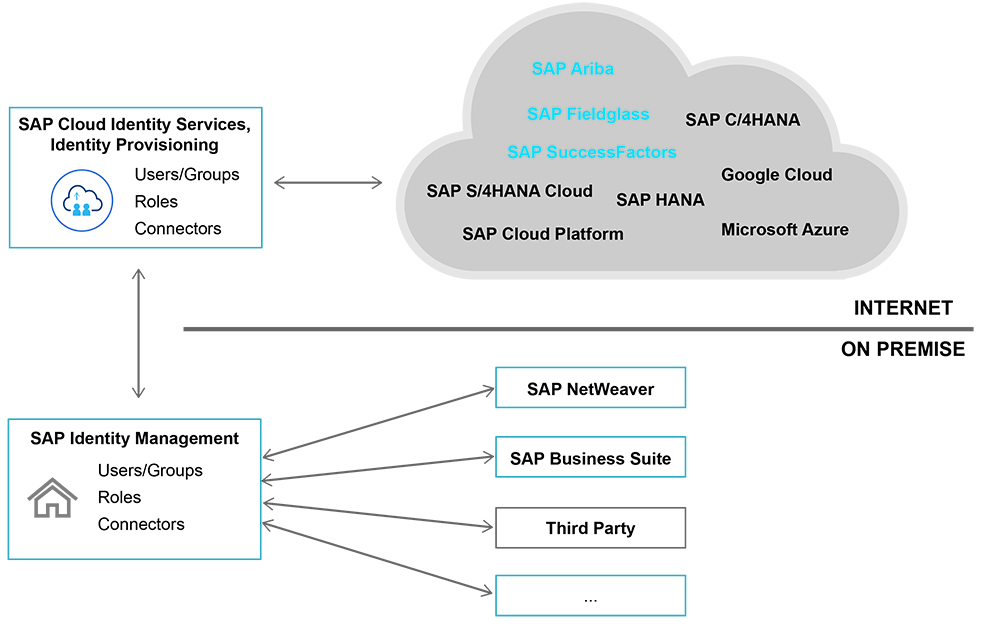
Figure 4 The Identity Provisioning component connects SAP Identity Management systems with SAP cloud solutions
Using the System for Cross-domain Identity Management (SCIM) protocol, SAP Identity Management sends a provisioning request to Identity Provisioning. A special connector for Identity Provisioning is shipped with SAP Identity Management, which makes the configuration easy. Users and groups as well as their roles can be sent from SAP Identity Management to Identity Provisioning, which in turn makes them available to connected cloud applications such as SAP S/4HANA Cloud, SAP Ariba, and SAP Fieldglass.
Risk and Compliance in Hybrid Landscapes
As organizations shift their focus from on premise to the cloud, and cloud applications take on a more business-critical role, they need to think about extending the way they manage risk and compliance into the cloud as well. Many SAP customers are already using SAP Access Control to minimize segregation-of-duties risks in their on-premise landscapes. When considering moving applications that contain sensitive data to the cloud, compliance becomes a pressing concern — perhaps even more than it was in an on-premise environment due to the very nature of the cloud, which introduces easy access to data from anywhere. While this access can significantly enhance productivity, it can also pose additional threats to data integrity.
As with the previous identity management scenario, existing on-premise security investments can be leveraged and extended into the cloud by connecting SAP Access Control and SAP Identity Management to SAP Cloud Identity Access Governance, as shown in Figure 5. SAP Cloud Identity Access Governance is based on SAP Cloud Platform and enables instant insight into potential risks and access issues.
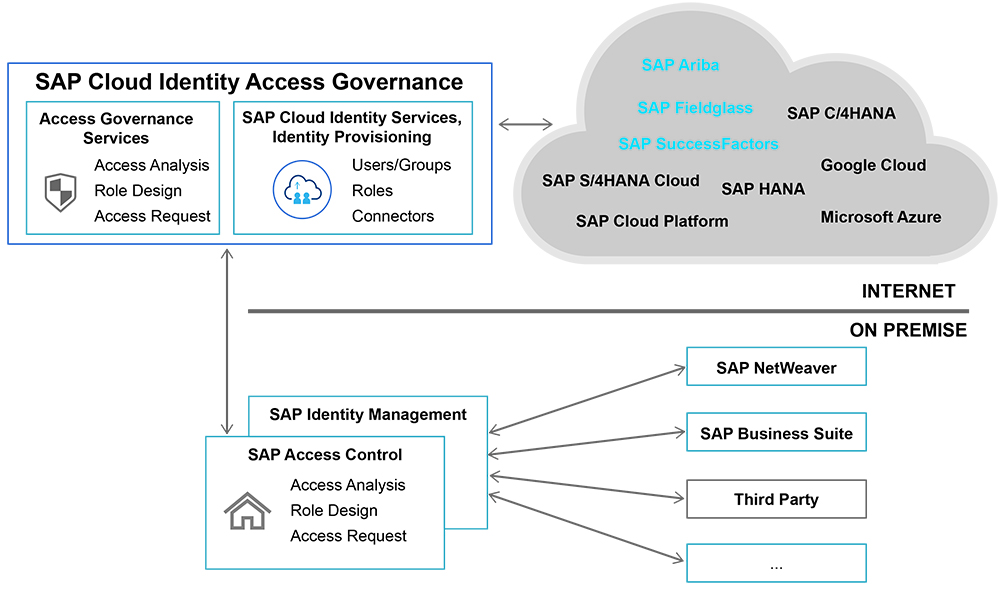
Figure 5 SAP Access Control and SAP Identity Management can be extended to the cloud using SAP Cloud Identity Access Governance
SAP Cloud Identity Access Governance provides access analysis, role design, access request, access certification, and privilege access management in the cloud. An on-premise SAP Access Control application can be connected using the “IAG Bridge” concept, which turns SAP Cloud Identity Access Governance into an extension of SAP Access Control, creating a tightly integrated web of compliance within the business.
Learn more about managing risk and compliance in hybrid landscapes at https://www.sap.com/products/cloud-iam.html.
Summary
While it is not possible to simply transfer all identity and access management concepts and processes from an on-premise environment into a mixed bag of on-premise and cloud applications, it is actually quite easy to protect existing investments when making the move to the cloud. With some tweaks and configurations, many security settings and strategies can be transferred to SAP Cloud Platform. The combined security infrastructures of an on-premise SAP environment and cloud applications can provide organizations with the best of both worlds.
Learn More
- SAP Cloud Identity Services
https://community.sap.com/topics/cloud-platform-identity-authentication
https://community.sap.com/topics/cloud-platform-identity-provisioning
- SAP Identity Management
https://community.sap.com/topics/identity-management
- SAP Single Sign-On
https://community.sap.com/topics/single-sign-on
- SAP Cloud Identity Access Governance
https://www.sap.com/products/cloud-iam.html
- SAP Access Control
https://www.sap.com/products/access-control.html

Regine Schimmer (regine.schimmer@sap.com) is a Product Manager for SAP security and identity management solutions at SAP SE in Walldorf. She has more than 15 years of experience with SAP security solutions.

Matthias Kaempfer (matthias.kaempfer@sap.com) is a Product Manager for SAP security solutions at SAP SE in Walldorf. He has more than 20 years of experience in SAP technology and security.




