Application Security Imperiled by Attackers
By Arndt Lingscheid, Global Solution Owner Cybersecurity and Data Protection, at SAP SE, and Martin Mueller, Presales and Program Manager, SAP Security Suite, SAP Germany SE
Application security is being threatened by cyberattacks on the application layer, such as SAP S/4HANA systems, which target valuable resources organizations store there.
Despite the increase in attacks, companies are not allocating resources to combat these threats.
According to a report by the Ponemon Institute, there is a vast gap between the security risk and the allocation of spending to application security. Based on a survey of 634 enterprise IT and security practitioners, 38% of respondents said that the level of risk to applications is high, but only 17% of the data protection and security budget is allocated to application security.
The situation today is very different from 20 years ago. Then, cyberattacks on SAP systems were rare. A company running SAP software had a closed IT environment. Today, the company is connected to the internet and running systems on-premise and in multiple cloud environments.
The most critical data is very often stored in SAP applications. To implement digital transformation, more and more open application programming interfaces (APIs) are being used. Employees use the internet and have multiple devices. External partners and consultants join and leave the company on an ongoing basis, some never to return.
New business processes for suppliers, customers, and partners are constantly developing. The protection of the most important data stored in SAP systems is becoming critical. Therefore, new security concepts are necessary to protect the “crown jewels” stored in SAP systems. Companies need to deploy real-time detection and response to deal with the rise in attacks against the SAP application layer level. Let’s have a look at some examples of these attacks:
- A newly published SAP software vulnerability was exploited to access critical data two days after SAP issued a patch.
- A brute force attack was used to access SAP software with superuser permissions.
- External consultants disregarded security policies and worked as developers in a productive system.
- Business was interrupted for several days because an external partner deleted an SAP software-based business table.
- A privileged user manipulated their salary.
- Identity theft occurred with a user login at the same time in different locations.
- Information about new products stored in SAP software applications appeared on the internet before product launch.
Protecting the Intelligent Enterprise
An enterprise will only be able to defend itself against these attacks if everyone within the organization is aware of security and protecting the crown jewels, which are often located in the application layer. For robust defense, awareness needs to be the gatekeeper when you look at the four quadrants of protecting the intelligent enterprise (Figure 1):
- Identity and access governance
- Data protection and privacy
- Cybersecurity
- Enterprise risk and compliance
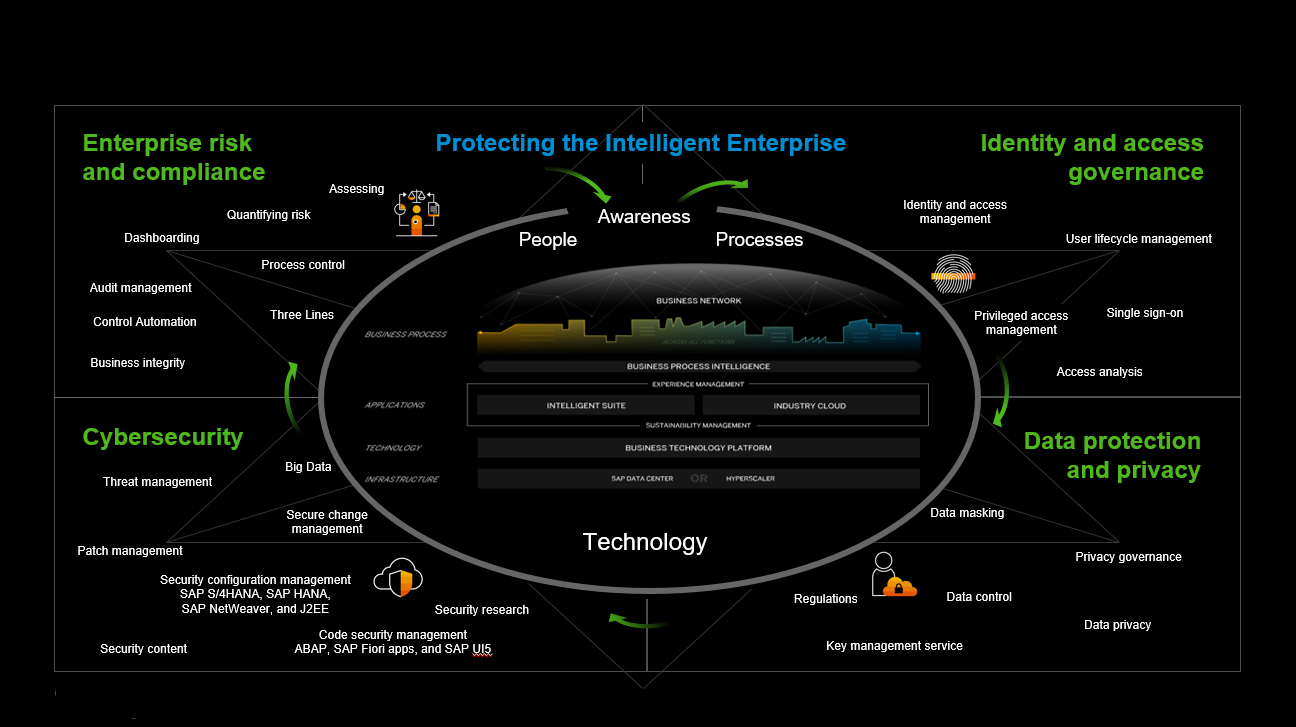
Figure 1: Protecting the Intelligent Enterprise
When a highly privileged user is created within identity and access management, the threat management tool must have the information to monitor the privileged user appropriately. The threat management tool then informs the technology within data protection to mask critical information in the user interface to prevent it from being seen or downloaded. Another example would be that data can be automatically masked according to attribute-based access or the location from which information is accessed.
This critical information needs to be processed and communicated to the enterprise risk and compliance tool to give executives, such as the chief information security officer (CISO), visibility to make the right decisions at the right time, based on quantifying risk and presenting and correlating it within an appropriate dashboard.
Securing the Crown Jewels
Organizations need to go beyond preventive measures and deploy real-time detection and response to protect their critical data.
SAP Enterprise Threat Detection, cloud edition (Figure 2), which became available in July 2021, provides transparency into suspicious user behavior and anomalies in SAP business applications to identify and stop security breaches in real-time. It uses automated processes based on SAP HANA technology to track hacker activity using predefined and easily customizable attack path patterns.
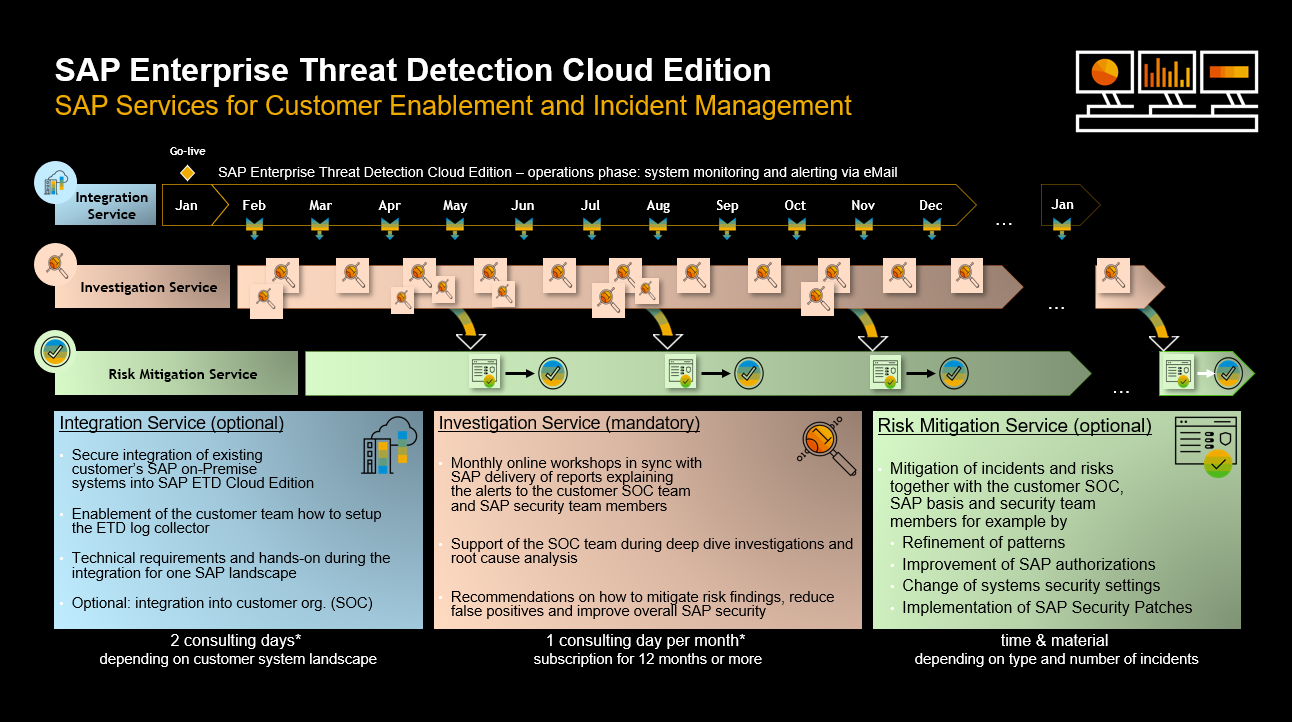
Figure 2: SAP Enterprise Threat Detection Cloud Edition
The managed service provides customers with a 24/7 security monitoring service. This avoids the need to build a large security team with appropriate availability and deep security knowledge. Nevertheless, the customer should have sufficient expertise to understand the alerts and execute the predefined security procedures.
SAP Enterprise Threat Detection, cloud edition, is suitable for all sizes of customers. Small and medium-sized enterprise (SME) customers might decide on the cloud edition because of the issues about velocity and costs. Large customers might choose the cloud edition for the same reasons or because of an overall go-to-cloud strategy.
The solution provides alerts based on patterns in the following categories:
- Access to sensitive information
- Critical system configuration changes
- User management and privileged user management
- Critical system communication
- User login management
The managed service is available in two different approaches: baseline and extended services. The baseline service includes:
- 24/7 monitoring of your SAP environment
- Checking for 60 standard attack path patterns
- Risk-based and prioritized alerting
- Monthly reporting of all incidents and all log data
Examples of Alerts and Responses
The baseline service creates alerts leading to investigations by agents (security experts) working in the security operations center. Example 1 (Figure 3) below shows a true positive based on a compliance violation (SAP_All assignment by User JOE_SMITH).
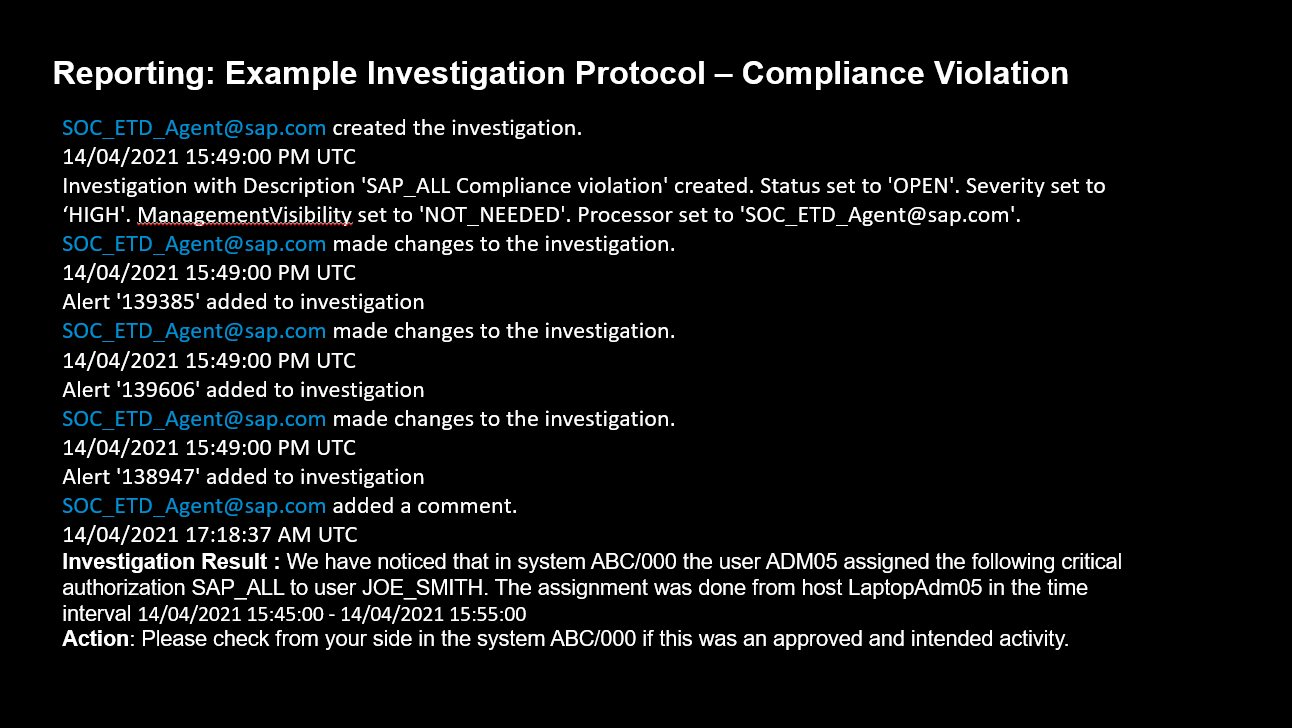
Figure 3: Reporting: Example Investigation Protocol — Compliance Violation
In the example, the customer gets the information about who is responsible for the SAP_All assignment to User JOE_SMITH. In addition, the customer receives the alerts and the corresponding logfile information. As a result of this report, the customer still needs to mitigate the risk internally, using the actions described in the report. This can be done by the customer or by a service provided by a partner or SAP.
Let’s have a look at another example (Figure 4). The investigation protocol shows user JOE_SMITH has been assigned to the user group ADMIN. In addition, the customer gets the information about who made the assignment and when it was done, based on alerts and logfile information, including the steps that should be taken to mitigate the risk.
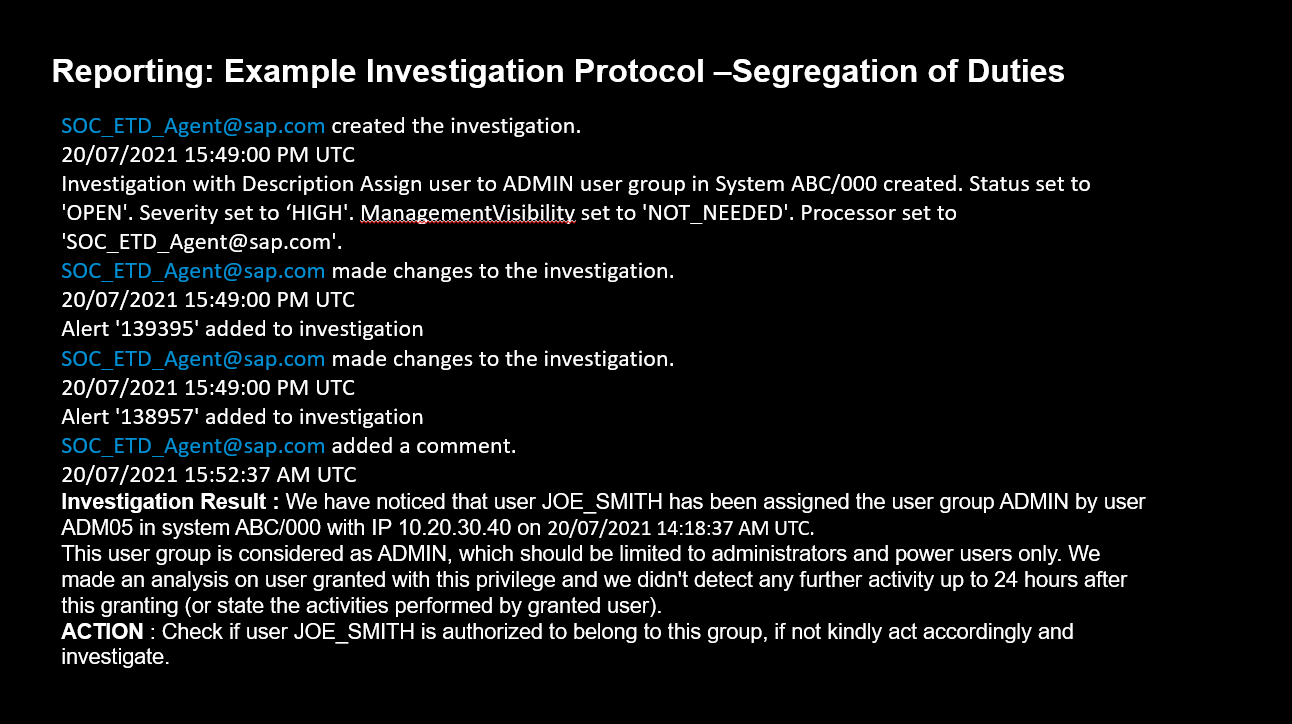
Figure 4: Reporting: Example Investigation Protocol — Segregation of Duties
Another example shows how important the user patterns in the background are. Figure 5 displays an example where an investigation was created because a user type was changed from a technical user to a dialog user. This example highlights the importance of the content patterns that are part of the product. New and updated content patterns are provided by SAP as part of the managed service.
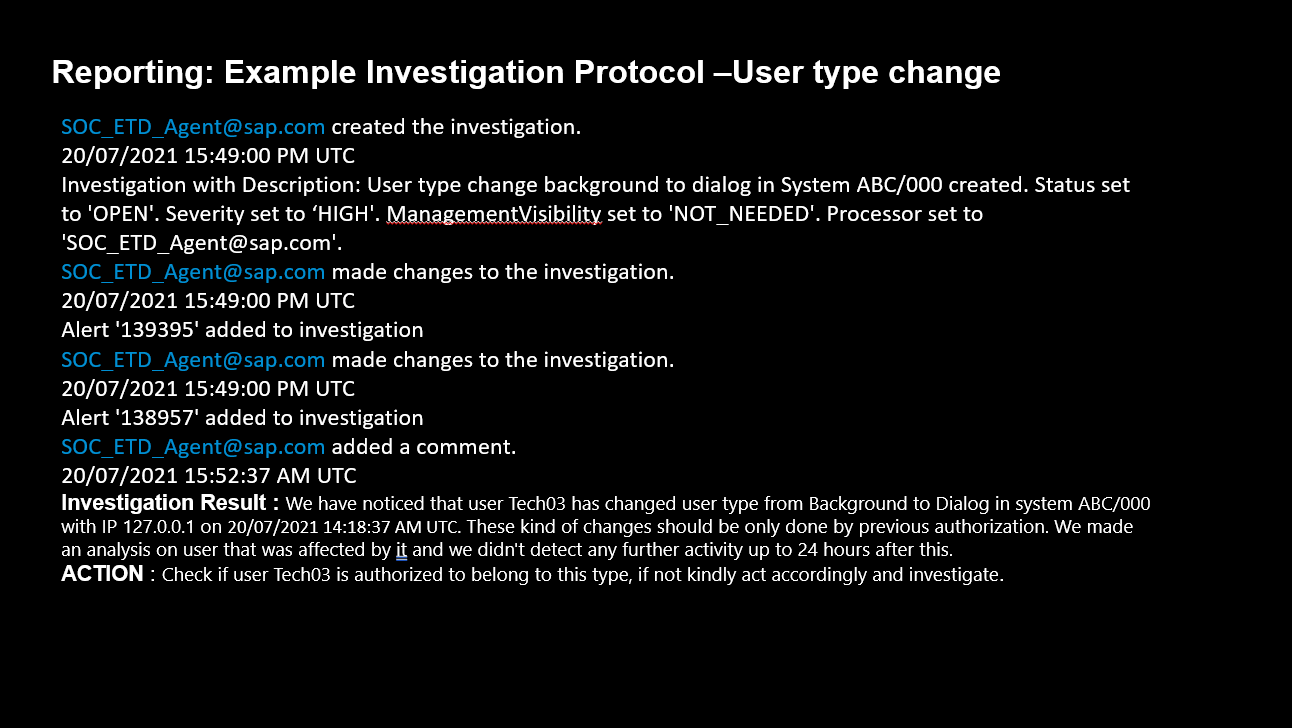
Figure 5: Reporting: Example Investigation Protocol — User Type Change
Example 4 shows that the agent created an investigation based on a download of a critical filename (Figure 6). A pattern automatically created an alert because the file with the name “Password” was downloaded. Based on the data in the alert, the agent decided it was a false positive because the downloaded file was a readme.txt file with no password information. No critical data was downloaded.

Figure 6: Reporting: Example Investigation Protocol — False Positive
Currently, the managed service is only offered within the European Union. A roll-out of the service to other regions is already planned. Depending on customer requirements, additional data centers and provisioning of the service can be added.
With the next version of the service, SAP plans to give customers an additional management report, which will provide an easy-to-use dashboard view of the cybersecurity status of their SAP landscape (Figure 7). The example shows a comparison of the investigations created by the agents in the last two months. A similar report showing the number of alerts will be available as well.
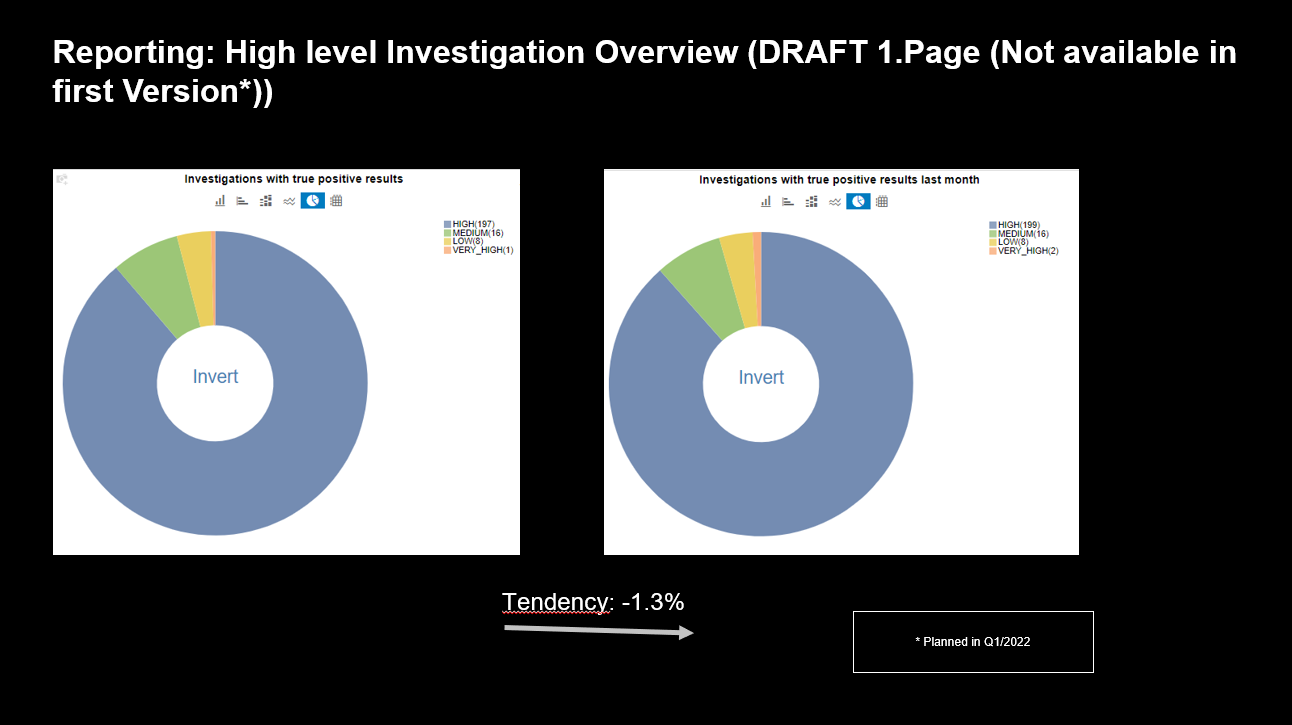
Figure 7: Reporting: High Level Investigation Overview
In addition to the baseline service, SAP will begin offering the extended service in the first quarter of 2022. The extended service includes the baseline service features along with committed response times, individually adapted security analysis, and customized service level agreements (Figure 8).
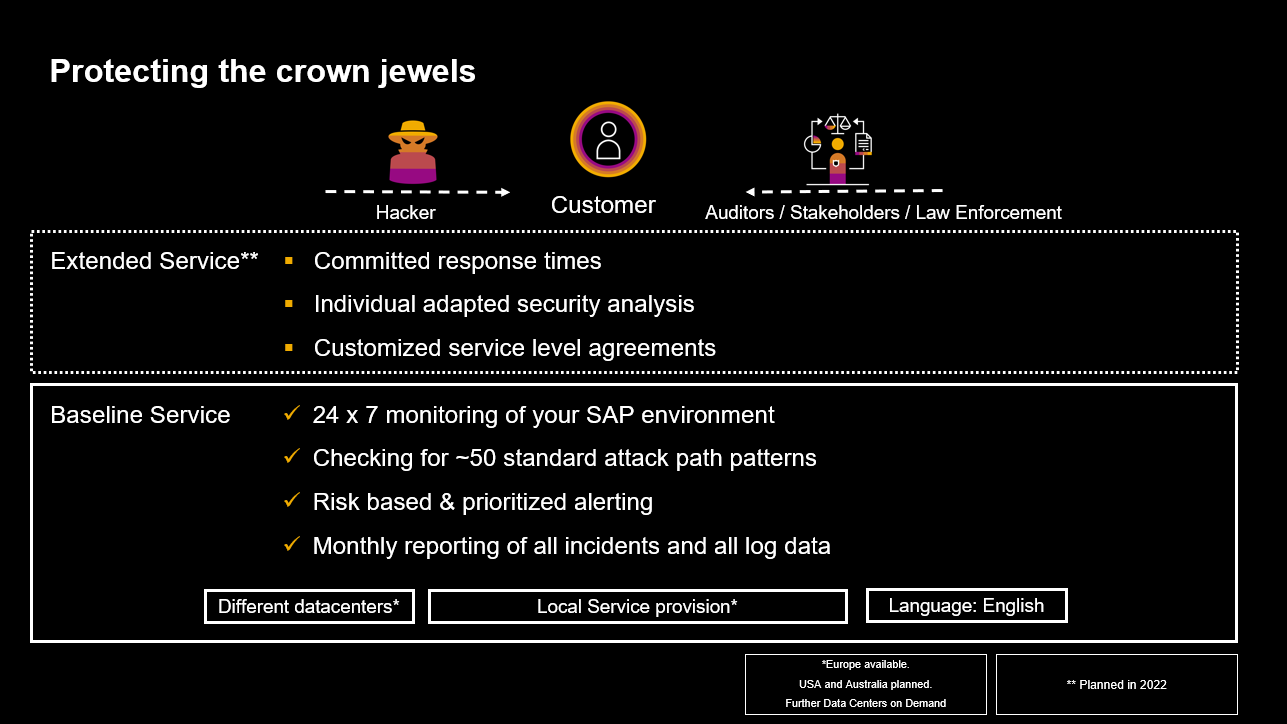
Figure 8: Protecting the Crown Jewels
“Security is a top priority for SAP. We know some of our customers don’t have in-house security operations centers to monitor and protect their mission-critical applications from ever-growing cybersecurity threats,” says Thomas Ruhl, Head of Product Management for Customer Innovation and Maintenance at SAP.
“That’s why we released SAP Enterprise Threat Detection, cloud edition: a solution that bundles powerful software and a managed service by SAP security experts to defend against cyberattacks and safeguard their business,” he adds.
SAP customers understand the severe problem of application security and are looking for a solution to stop cyberattacks. In response, SAP developed a monitoring tool to detect attacks on SAP applications called SAP Enterprise Threat Detection. Using the same technology, SAP now delivers a managed service based on this proven technology.







