Shift to Remote Work Underscores Need for a Robust Identity and Access Management Program
by Fred Donovan, Senior Editor, SAPinsider
As a result of the COVID-19 pandemic, remote workforce models are likely here to stay. This shift magnifies the importance of organizations guaranteeing that only authorized individuals can access their network and data. The best way to avoid unauthorized users from entering SAP systems is through a robust and automated identity and access management (IAM) program.
According to a survey of IT decision-makers by LastPass, 98% of respondents said they depend on IAM platforms to secure their business in the current work-from-anywhere environment, and 96% said that remote work had impacted their IAM strategy.
Explore related questions
More than half of respondents strongly agree that increasing security for their remote workforce using IAM is critical.
Respondents recommended IAM solutions such as single sign-on, multifactor authentication, and password management to secure remote workers while IT retains visibility and control over logins.
Sarma Adithe, SAP’s Chief Product Manager for Access Governance, advises organizations to adopt cloud-based user authentication and provisioning to ensure a unified approach for IAM and support the identity lifecycle of employees.
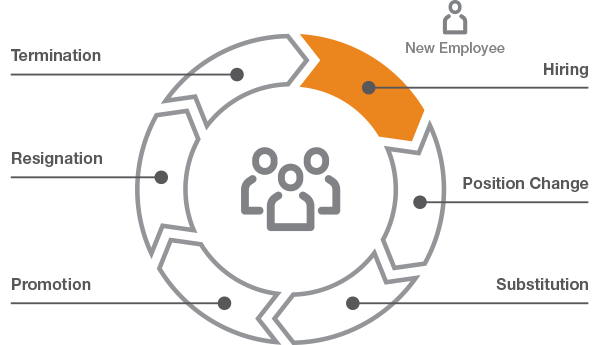
Figure 1 — The identity lifecycle of employees
Managing the identity lifecycle of employees (Figure 1) is vital for production and compliance. Productivity is impacted when an employee cannot access required resources to accomplish a task. Regulatory compliance issues can arise when an employee keeps access rights to resources no longer needed or authorized.
Automating IAM in a Complex Enterprise Environment
Automating IAM helps the IT team secure a remote workforce in a complex enterprise environment, James Roeske, CEO of the Customer Advisory Group says. “Getting people the right access in an automated, safe, and Segregation of Duty (SoD)-free way helps everyone.”
An automated IAM system that defines and grants access triggered by HR events will enable a new employee to be productive on day 1. An automated IAM platform will continue to boost productivity because it adjusts the employee’s access as roles and responsibilities change. And once the employee leaves the organization, all access must be canceled to ensure that person no longer has access to corporate resources.
In addition, IAM controls should align to corporate governance objectives and polices. “The cycle should be able to identify risk, associate mitigation control, and apply Continuous Control Monitoring (CCM) to help ensure mitigation controls are still effective,” Adithe observes.
Automated IAM needs to be supported by human-instituted policies and controls to protect organizations, comply with regulations, and enable maintenance and cleanup of access.
“Assigning access that honors all the required policies and regulations from a compliance standpoint should be an inherent process,” Adithe says. He also recommends harmonizing access and defining employee responsibilities and roles in a standardized way.
Automated IAM, along with good access hygiene, effective role design, and human decision-making, will help keep organizations secure in a remote and constantly evolving work environment.
To learn more about automated IAM in the enterprise, read SAPinsider’s recent article “How Identity and Access Management Technology Is Supporting People Power.”