2021 GRC Trends Affecting the Intelligent Enterprise
Key Takeaways
⇨ Implementing a holistic view of access management and compliance
⇨ Leverage access privilege to suit your needs
⇨ View role design through a security lens
To streamline processes and operations while reducing IT teams’ burden, many members of the SAPinsider Community have started migrating to SAP S/4HANA as their core ERP and to cloud-native applications to run their businesses. However, these strategic moves have had implications on access governance, risk management, and regulatory compliance (GRC). A May 2020 SAPinsider research report found that 34% of respondents worked at organizations that were already running at least one instance of SAP S/4HANA, while 78% of the SAPinsider community used at least one of SAP’s cloud-based business solutions – and those numbers have increased.
SAPinsider spoke with Dudley Alan Cartwright, CEO of Soterion, to hear how organizations can apply a holistic view to GRC and how they can navigate Governance, Risk and Compliance (GRC) and Identity and Access Management (IAM) as they navigate the current business landscape and move toward the Intelligent Enterprise.
Addressing Key Business Objectives with Your GRC and IAM solutions.
Organizations implement Governance, Risk and Compliance (GRC) and Identity Access Management (IAM) solutions to address specific business objectives. However, according to Cartwright, the challenge that many organizations face is that they mistakenly believe that their GRC and/or IAM solution is the silver bullet to solve all their SAP security challenges. This often leads to the solution being under-utilized due to inefficient processes surrounding the solution.
Explore related questions
He advises that organizations take a more holistic approach when implementing a GRC and/or IAM solution. Companies must weigh the importance of each business objective for their organization. He explains that the typical GRC business objectives include:
- Ensuring a secure SAP solution
- Improving efficiencies
- Complying with regulations (in particular the data privacy regulations)
- Enhancing business accountability of access risk
Cartwright advises that enhancing business accountability of access risk is often the most challenging of the business objectives to get right. “Due to the technical nature of SAP authorizations, managing access risk has remained an IT function. The lack of business buy-in is often a result of complex solutions and processes. Coupled with this, the lack of senior management support for GRC projects also negatively impacts the ability to shift responsibility to the business,” he says. “Organizations need to convert the technical GRC language into a language the business users can understand. This can be done by using the ‘Effective GRC Pyramid’. The ‘Effective GRC Pyramid’ breaks the various GRC activities into individual components. Each component needs to address the organization’s specific business objectives. It is important to appreciate the inter-dependencies between the various components of the Effective GRC Pyramid. Deficiencies in any layer can result in the organization not achieving their desired business objectives,” he explains.
Fig. 1: Soterion’s pyramid emphasizing the interrelationships needed for organizations to take ownership of GRC
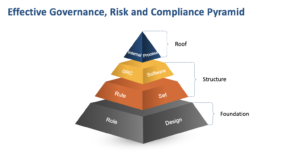
Companies that have addressed the SAP role design, and their SAP access risk rule set, generally experience a better business buy-in and accountability. “The SAP role design forms the foundation of all things GRC and IAM. If there are deficiencies in the SAP role design, it does not matter how good the organization’s access risk rule set and GRC solution are,” Cartwright explains.
He reports that organizations who have customized the standard ‘out-the-box’ rule set generally have better business buy-in and accountability. “The rule set customization project not only ensures that the organization monitors risks that are relevant to them, but it also serves as a great education process to educate the business users on the risks applicable to their area of responsibility. Business users who understand the access risks make more informed decisions.” Cartwright says.
Security Considerations When Moving to SAP S/4HANA
Since many companies are in the planning phases of their move to SAP S/4HANA, this presents a great opportunity for organizations to re-visit and/or address any SAP security deficiencies they may have, reports Cartwright. “Without proper planning, organizations run the risk of implementing a sub-optimal SAP security solution. This is likely to prove very costly to the organization, as once the SAP authorization solution is live in SAP S/4HANA, it becomes very difficult to fix any deficiencies without considerable effort, cost and business disruption. Look at performing many of the security activities prior to moving to SAP S/4HANA so as not to compete with other project resources, else the security element can be overlooked,” he says.
Cartwright notes that security becomes significantly more complex with the move to SAP S/4HANA due to the Fiori layer. Users will be assigned backend access via the PFCG roles, in addition to Fiori apps and services. Fault finding and general SAP authorization support will become much more challenging. It will be vital that organizations chose the correct SAP S/4HANA and Fiori role methodologies, he says.
As SAP S/4HANA will be very new to everyone, Cartwright says it is likely that SAP functional consultants will dictate user access with no consideration for access risk or on-going SAP security support. The recommendation of using the pre-defined Business Roles may be problematic for many organizations as they may provide very wide or inappropriate access.
Cartwright advises organizations deal with SAP security experts, and to make sure they explain their proposed design and methodology prior to the role build. “Be careful not to place too much importance on end-user experience at the expense of on-going Business as Usual (BAU) SAP security support and maintenance,” he adds.
He advises organizations to use the SAP S/4HANA project as an opportunity to cater for any data privacy regulations that may be applicable in your region. Many of the data privacy regulations require ‘Privacy by Design’. “Know what personal data your organization may hold and of that what is deemed sensitive. Ensure that the SAP S/4HANA role design project caters for this, Cartwright concludes.”
What Does This Mean for SAPinsiders?
In today’s remote settings and cloud environments, organizations can strengthen security and compliance by:
- Implementing a holistic view of access management and compliance: Instead of depending on a solution to resolve all GRC and/or IAM issues, you need business-wide investment and awareness into GRC, as well as education and training of all members of the team on SoD and access risks, to fully understand the issues and make appropriate decisions for your organization.
- Leverage access privilege to suit your needs: To ensure that the right people have the right access, you should involve multiple perspectives and should know in advance what roles should be customized to suit your business needs, confirming and agreeing on risks and rulesets that will meet your organization’s needs.
- View role design through a security lens: A security/GRC professional should help your decisionmakers understand the impacts of decisions based on risks identified through audits. To promote the dialogue, you should have IT and business teams examine regulations and their impacts and discuss role design on a regular basis.
Be proactive in adhering to regulations: Seek technological support in adhering to constantly evolving data privacy laws, and confirm that your cloud vendor hosts data and reports on data correctly. As new users are added to the system, organizations should constantly reassess privileges to confirm that the right people are being given the right amount of access.
ABOUT SOTERION
Soterion is a leading provider of SAP governance, risk and compliance solutions. Soterion’s GRC solutions provide SAP customers with in-depth access risk reporting to allow organizations to effectively managed their access risk exposure. Soterion is focused on simplifying governance, risk and compliance processes, with a focus on translating complexity into a business-friendly language to enhance better decision making and business accountability.



